Create new correlation searches
Create a correlation search
You can create your own correlation searches to generate notable events that you want to have stored in the notable index and to appear on the Incident Review dashboard. Create a Splunk saved search that finds the pattern you want and set it up to work with PCI Compliance.
1. Click Configure.
2. Click Correlation Searches.
3. Click New to open the Correlation Search editor.
Create and name your base search
1. Determine a name for your search. This name is used in the search string, so define it ahead of time. The Splunk App for PCI Compliance uses the following convention for correlation searches:
Domain - Descriptive Name - Rule
Example: A correlation search that looks for a large number of failed logins might be given the name:
Access - Excessive Failed Logins - Rule
2. Create a search that identifies the events that you want. Go to the Search dashboard and try search strings, building up a string that selects all the patterns you want.
Example: The following search identifies six or more failed authentication events per app and source, where "app" refers to the application used to authenticate. For example, "win:local" refers to the local authentication performed on a Windows system (using the keyboard) and "win:remote" refers to a remote API (such as telnet).
`authentication(failure)` | stats count,dc(user) as user_count,dc(dest) as dest_count by app,src | where count>=6<
Modify the search
After you have a search that works, you must modify it to work properly with the notable index, as follows:
- Make sure that the search sets a creation day for the notable event.
- Eliminate duplicate firings by creating and using a unique ID for the correlation search.
- Ensure the notable event is timestamped correctly.
- Remove the
_rawfield, if present.
1. Generate the notable event date. This is the day that the correlation search identified the pattern and created a notable event. You can generate the date by piping your search to the `get_date(now())` macro.
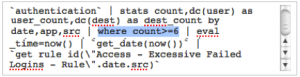
`authentication(failure)` | stats count,dc(user) as user_count,dc(dest) as dest_count by app,src | where count>=6 | `get_date(now())`
2. Aggregate equivalent notable events generated by the same correlation search using the `aggregate($string$)` macro. Aggregating events sets a correlation search to create a notable event based on an issue but to avoid creating multiple notable events in a single day. After the correlation search creates a notable event for that day, it ignores subsequent triggers if the rule_uid field matches.
To set the rule_uid and aggregate events, use the `aggregate($string$)` macro. This macro takes a string and aggregates all matching instances of the string. To use this macro, you need to construct a string that is identical for notable events you want to consider equivalent, but different for non-equivalent results from the correlation search. For example, for our failed login search above, we want to create separate notable events if we see six failed logins on two different hosts, six failed logins for two separate apps on the same host, or six failed logins for the same app and host on two different days.
To create a unique string, PCI Compliance uses the convention:
\"Rule Name\".date.field1.field2
Where:
- Fields are separated by a period (.)
- The first field is the rule name in double quotes ("). The quotes must be escaped with backslashes.
Enclosing a field in quotes escaped with backslashes (\") tells the app to take this value literally. Fields not enclosed in quotes are substituted with the field value for this notable event.
- The second term is the date, as generated above.
- Additional terms are any other fields that the rule should aggregate on (like the
srcordestfield).
Example: The example below aggregates by search_name, date (created with `get_date(now())`), app, and src. This means that subsequent correlation search firings with the same date, app, and src values are aggregated from an incident review perspective.
`authentication(failure)` | stats count,dc(user) as user_count,dc(dest) as dest_count by app,src | where count>=6 | get_date(now())` | `aggregate(\"Access - Excessive Failed Logins - Rule\".date.app.src)`
3. Set the timestamp for the notable event to the current time, that is, the time at which the notable event was triggered. To do this, populate the _ time field piping your search to eval _time=now().
`authentication(failure)` | stats count,dc(user) as user_count,dc(dest) as dest_count by app,src | where count>=6 | get_date(now())` | `aggregate(\"Access - Excessive Failed Logins - Rule\".date.app.src)` | eval _time=now()
4. Save and remove the _raw field, if present. If the _raw field exists, then Splunk Enterprise only saves _raw and ignores the other fields. Thus, the _raw field should be copied into another field and then removed. To do this, add the following to the search:
| eval orig_raw=_raw | fields - _raw
Note: This step is unnecessary if the search contains the stats command because it removes _raw by default. The example above does not need to be modified.
Here is an example of a different search that uses the _raw syntax. This search takes all warnings from the source WinEventLog:Directory Service and converts each warning to a separate notable event.
source="WinEventLog:Directory Service" Type="Warning" | `get_event_id` | rename event_id as orig_event_id | eval orig_raw=_raw | fields - _raw | fields + orig_raw,orig_event_id,host,sourcetype,EventCode | `get_date(now())`| `aggregate(\"Access - AD Test - Rule\".date.EventCode)` | eval _time=now()>
Note: This example requires a working windows domain controller and the addition of WinEventLog:Directory Service as a data source.
Scheduling real-time searches
The Splunk App for PCI Compliance introduces the ability to use real-time correlation. To schedule a search as "real-time", set the Time Range fields to "real-time" values. See "About real-time searches and reports" in the Search Manual.
Note: The Search type > Cron Schedule field is automatically filled in. When using a real-time search, this field controls how often the Splunk search scheduler confirms that the search is still running.
Configure correlation search thresholds
Some security problems can be detected based in part on the volume of events. For example, a small number of new infections on a large network might be considered normal. However, a large number of new infections might indicate the presence of a deeper problem, such as an outbreak. Correlation searches for these types of security problems generate notable events when certain security indicators exceed a given value.
Understand correlation search thresholds
Correlation searches use thresholds to set the number of security events of a specified type that must occur to trigger a notable event. You can configure the thresholds for these searches based on the typical number of events in your environment. For example, the Outbreak correlation search triggers when the number of new infections within the last 24 hours exceeds the threshold, alerting you when an organization-wide issue is developing. However, the Outbreak correlation search needs to be adjusted to reflect the size and load of your environment. A large enterprise might consider ten new infections within a 24-hour period an outbreak, whereas a small company might consider only 3 new infections an outbreak. The threshold sets the number of infections that correlation search considers noteworthy.
Threshold settings are best configured after developing a baseline of security events. Index two weeks of data before finalizing the baseline settings. Thresholds need to be adjusted over time as the network changes.
See "Correlation Search Thresholds" in the Splunk App for PCI Compliance User Manual for more detail on setting thresholds.
Edit correlation search thresholds
Correlation searches are implemented using saved searches in Splunk Enterprise. To change a correlation search threshold, you need to edit the associated saved search.
To do this:
1. Select Configure > Correlation Searches to see a list of all correlation searches.
2. Click the name of the correlation search to modify.
3. Locate the threshold for the correlation search. Usually, this has a greater than (>) sign and a number.
4. Adjust the number to the value you have determined is correct for your environment.
5. Click Save at the bottom of the page.
Configure the watchlisted event correlation search
To use the watchlisted event correlation search, a set of watchlisted events needs to be defined. A watchlisted event in the Splunk App for PCI Compliance is defined as any event that has the tag "watchlist".
These watchlist events are included with the Splunk App for PCI Compliance:
| Name | Watchlist |
|---|---|
| TA-sav | [eventtype=sav_hacktool]
[eventtype=sav_wineventlog_hacktool] [eventtype=sav_keylogger] [eventtype=sav_wineventlog_keylogger] [eventtype=sav_rootkit] [eventtype=sav_wineventlog_rootkit] |
| SA-IdentityManagement | (via identity lookup)
[src_user_watchlist=true] [user_watchlist=true] (via asset lookup) [host_owner_watchlist=true] [orig_host_owner_watchlist=true] [src_owner_watchlist=true] [dest_owner_watchlist=true] [dvc_owner_watchlist=true] |
| SA-ThreatIntelligence | By default the Splunk App for PCI Compliance does not ship with any watchlisted events enabled SA-ThreatIntelligence. For this reason the "watchlist" tag has been disabled. To enable the watchlist feature, do the following from the Manager: 1. Enable the tag "watchlist" in the SA-ThreatIntelligence app. 2. Add a valid search string to the eventtype "watchlist" in the SA-ThreatIntelligence app. |
| Splunk_TA_windows | [eventtype=windows_audit_log_stopped]
[eventtype=windows_audit_log_cleared] |
| TA-sep | [eventtype=sep_risk_hacktool] |
| TA-mcafee | [eventtype=mcafee_watchlist_gambling] |
To add events to the watchlist, simply tag any field value in the event with the tag "watchlist". This tag can be created in the same manner as any other tag.
For more information on creating tags, see "Tag and Alias Field Values in Splunk Web" in the Knowledge Manager Manual and "How can I set up a watchlist" in Splunk Answers.
It is best to select as specific a field value as possible when tagging events as "watchlist", to prevent this correlation search from matching too many events.
Configure correlation search governance
A governance or control number can be assigned to a correlation search. To do this, set up your Governance list and configure the search.
Configure governance list
To set up the Governance list to display in the governance filter drop-down list on the Incident Review dashboard, do the following:
1. Set up the list of governance standards. To do this, edit the file $SPLUNK_HOME/etc/apps/SA-ThreatIntelligence/lookups/governance.csv. This file is a list of the governance standards to display, with one item per line.
Make sure the first line says "governance".
governance pci hipaa
Add governance to a correlation search
1. To add a governance and control number to a specific correlation search, determine the exact name of the saved search. To do this, look for the field titled "Search Name" in the notable event or find the name in the list of correlation searches in the Splunk App for PCI Compliance (Configure > Correlation Searches). For example, the correlation search for locating insecure or cleartext authentication is Access- Insecure Or Cleartext Authentication Detected - Rule and it is part of the Access Security domain.
2. Open the file $SPLUNK_HOME/etc/apps/SA-ThreatIntelligence/local/savedsearches.conf in a text editor.
3. Add a stanza for governance to the correlation search in the following format. The terms you must edit are in bold:
[<search_name>] action.summary_index.<governance>_control = #
For example, to add governance for PCI 2.3 and HIPAA 1.1.4 to the correlation search
Insecure Or Cleartext Authentication Detected, you would add the following stanza:
[Access - Insecure Or Cleartext Authentication - Rule]
action.summary_index.pci_control = 2.3 action.summary_index.hipaa_control = 1.1.4
Note: The governance settings are only applied to notable events created after the changes are made. Notable events created previously do not have the updated governance information.
| Configure correlation searches | Notable events |
This documentation applies to the following versions of Splunk® App for PCI Compliance: 2.1.1
 Download manual
Download manual
Feedback submitted, thanks!