Vulnerability Scan Details
Report on vulnerabilities discovered on PCI assets. This report looks at vulnerability scan details data produced by firewalls, routers, switches, and any other device that produces vulnerability data.
Vulnerability scans of the cardholder data environment expose potential vulnerabilities in networks that could be found and exploited by malicious individuals. When these weaknesses are identified, the organization should correct them and repeat the vulnerability scan to verify that they have corrected the vulnerabilities.
This report shows all vulnerabilities identified for selected assets. Use this report to identify specific high and/or critical vulnerabilities on cardholder systems that need to be fixed.
Relevant data sources
Relevant data sources for this report includes any vulnerability data.
How to configure this report
1. Index vulnerability scan results in Splunk Enterprise.
2. Map the vulnerability data to the following Common Information Model fields:
category,severity,signature,dest,os
You can also map these additional fields:
cve, bugtraq, cert, msft, mskb, xref, cvss
3. Tag the successful synchronization data with vulnerability and report.
Report description
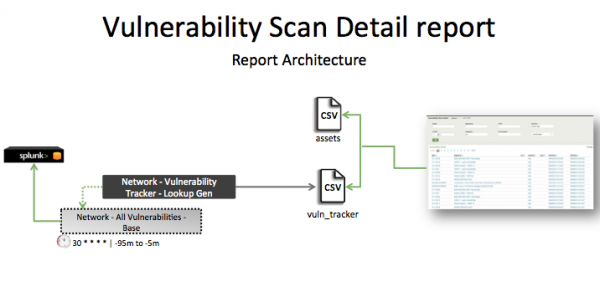
The data in the Vulnerability Scan Details report is populated by a lookup search that runs against the vuln_tracker lookup. This lookup is created by the Network - Vulnerability Tracker - Lookup Gen saved search, which is a post-process task of the Network - All Vulnerabilities - Base saved search. This information is combined with information from the asset table to produce the report.
This search runs on a 30-minute cycle and looks at 90 minutes of data.
Note: The report window stops at 5 minutes ago because some data sources might not have provided complete data in a more recent time frame.
| Schedule | 30 * * * * | Runs on a 30-minute cycle. |
| Report window | -95m@m to -5m@m | Looks at 90 minutes of data. |
Useful searches/Troubleshooting
| Troubleshooting Task | Search/Action | Expected Result |
|---|---|---|
| Verify that you have data from your network devices. | sourcetype=<expected_st> | Returns data from your network devices. |
| Verify that vulnerability data is in Splunk Enterprise. | tag=vulnerability tag=report or `vulnerability` |
Returns vulnerability data. |
| Verify that fields are normalized and available at search time. | `vulnerability` | table _time,dest,category,signature,cve,bugtraq,cert,msft, mskb,xref,severity,cvss,os vendor_product |
Returns a table of the vulnerability data fields. |
| Verify that the vulnerability tracker file is populated | | inputlookup append=t vuln_tracker or `vuln_tracker_simple` or `vuln_tracker` |
Returns data in the vuln_tracker |
| PCI Asset Logging | Rogue Wireless Access Point Protection |
This documentation applies to the following versions of Splunk® App for PCI Compliance: 2.1.1
 Download manual
Download manual
Feedback submitted, thanks!