PCI Asset Logging
This report provides a list of all PCI assets that have stopped logging their data to Splunk Enterprise or that have never logged data to Splunk Enterprise. Use this report to ensure that all PCI assets are logging their data to Splunk Enterprise. Use this report to repair any systems that are non-compliant in their logging configurations.
PCI DSS requires that audit logs from systems, applications, and devices in the cardholder data environment be promptly backed up to a central log server. Splunk Enterprise functions as this central log server and monitors the data flow from all PCI assets.
Relevant data sources
Relevant data sources for this report include Splunk metadata and audit logs.
How to configure this report
You do not have to configure this report. It uses Splunk metadata and the assets table to create results.
Report description
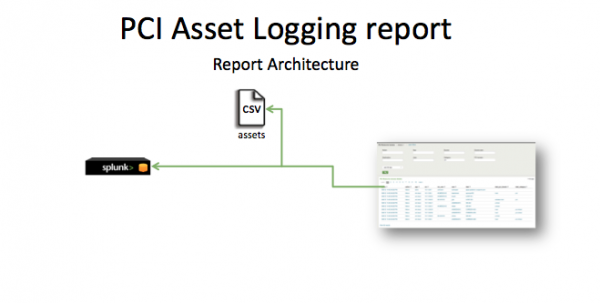
The data in the PCI Asset Logging report is populated by a lookup that runs against the assets.csv file. The user creates the asset table.
Useful searches/Troubleshooting
| Troubleshooting Task | Search/Action | Expected Result |
|---|---|---|
| Verify that you have data from your network device(s). | sourcetype=<expected_st> | Returns data from your network device(s). |
| Verify that metadata is accessible and data exists for the hosts from which data is collected. | `host_eventcount` | Returns host metadata. |
| Verify that metadata is successfully joined with the asset table. | | `asset_eventcount` | Returns PCI asset logging data. |
| Verify that PCI asset logging fields are populated. | | metadata type=hosts index=* | Returns table of PCI asset logging fields fields. |
| Verify population of the access_summary index. | `get_summary(access_summary,Access - All Authentication - Summary Gen)` _time,action,app,src,src_user,dest,user | Returns a table of fields in the access_summary index. |
| Privileged User Activity | Vulnerability Scan Details |
This documentation applies to the following versions of Splunk® App for PCI Compliance: 2.1.1
 Download manual
Download manual
Feedback submitted, thanks!