Default Account Access
This report provides a six-month rolling view of attempts to access cardholder systems using default user accounts. This report looks at all activity by accounts categorized in the Identity table with category=default. A default list of accounts is provided in the Identity table, which can be edited using the List and Lookups configuration dashboard.
Relevant data sources
Relevant data sources for this report includes Windows Security, Unix SSH, and any other application, system, or device that produces authentication data. The report looks at data in the access_summary summary index.
How to configure this report
1. Index authentication data from a device, application, or system in Splunk software.
2. Map the data to the following Common Information Model fields:
host, action, app, src, src_user, dest, user
3. Set the category column of the Identity table to default for all accounts that are considered default accounts.
Report description
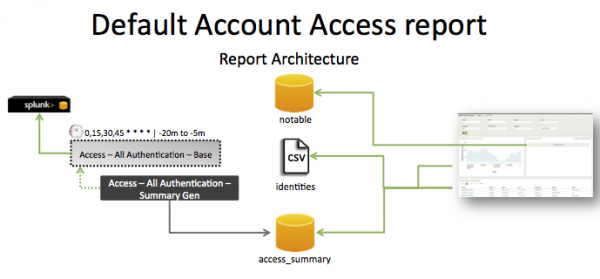
The data in the Default Account Access report is populated by an ad hoc search that runs against the access_summary summary index. This index is created by the Access -- All Authentication -- Summary Gen saved search, which is a post-process task of the Access -- All Authentication -- Base saved search.
This search runs on a 15 minute cycle and looks at 15 minutes of data.
| Schedule | 0,15,30,45 * * * * | Runs on a 15 minute offset window. |
| Report window | -20m@m to -5m@m | Looks at 15 minutes of data. |
Note: The report window stops at 5 minutes ago because some data sources may not have provided complete data in a more recent time frame.
Useful searches/Troubleshooting
| Troubleshooting Task | Search/Action | Expected Result |
|---|---|---|
| Verify that you have data from your network devices. | sourcetype=<your_sourcetype_for_your_data> | Returns data from your network devices. |
| Verify that authentication data is indexed in Splunk Enterprise. | tag=authentication or `authentication` |
Returns all default account activity data from your devices. |
| Verify that default user accounts are tagged properly. | `default_user_accounts` | Returns all a list of all default account activity. |
| Verify that authentication attempts for default users are returned. | `default_user_accounts` `authentication` | Returns a list of all default account authentication activity. |
| Verify that authentication data is normalized to the Common Information Model properly. | `authentication` | fields sourcetype, action, app, src, src_user, dest, user | Returns a list of events and the specific default account activity fields of data populated from your devices. |
| Verify that the summary index is populated. | `get_summary(access_summary, Access - All Authentication - Summary Gen)` | Returns data in the access_summary index. |
Additional information
The report displays all attempts from users in either the src_user or user fields.
The assets table includes user information for default accounts such as root, network service, and other accounts that can produce a lot of data. Customers might not want to include that data in the report. They can modify the assets table or modify the saved search to exclude particular users.
- The
Access – All Authentication – Summary Genis a post-process task. You can find the details of this search in the$SPLUNK_HOME/etc/apps/SA-AccessProtection/default/postprocess.conffile.
- The
Network – Communication – Summary Genis a post-process task. You can find the details of this search in the$SPLUNK_HOME/etc/apps/SA-NetworkProtection/default/postprocess.conffile.
| Network Traffic Activity | Insecure Authentication Attempts |
This documentation applies to the following versions of Splunk® App for PCI Compliance: 2.1.1
 Download manual
Download manual
Feedback submitted, thanks!