Notable events
When a correlation search included in the Splunk App for PCI Compliance (or added by a user) identifies an event or pattern of events, it creates a notable event. Correlation searches filter the IT security data and correlate across events to identify a particular type of incident (or pattern of events) and then create notable events. The app includes pre-configured correlation searches to create notable events, and lets you add your own.
Correlation searches run at regular intervals (for example, every hour) or continuously in real-time and search events for a particular pattern or type of activity. The notable event is stored in a dedicated notable index, which is implemented as a summary index in Splunk Enterprise. The Incident Review dashboard is used to view and act on notable events. A notable event might be a single event of high importance, such as any activity from a known web attacker, or an aggregate of multiple events that together warrant review, such as a high number of authentication failures on a single host followed by a successful authentication.
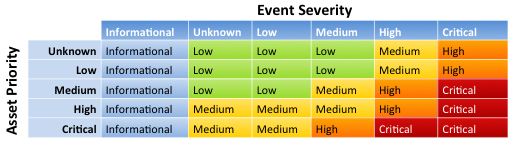
When notable events are created, relevant information from the asset list is combined with the event information. To help to further identify important patterns, correlation searches are each assigned a "severity" of informational, low, medium, high, or critical. Notable events are assigned an "urgency", based on the severity of the event and the priority of the asset corresponding to the event.
- If Event Severity is Informational, the Event Urgency is Informational, regardless of Asset Priority
- If Asset Priority is Unknown or Low and Event Severity is Unknown, Low, or Medium, the Event Urgency is Low
- If Asset Priority is Unknown or Low and Event Severity is High, the Event Urgency is Medium
- If Asset Priority is Unknown or Low and Event Severity is Critical, the Event Urgency is High
- If Asset Priority is Unknown or Low and Event Severity is Critical, the Event Urgency is High
- If Asset Priority is Medium and Event Severity is Unknown or Low, the Event Urgency is Low
- If Asset Priority is Medium and Event Severity is Medium, the Event Urgency is Medium
- If Asset Priority is Medium and Event Severity is High, the Event Urgency is High
- If Asset Priority is Medium and Event Severity is Critical, the Event Urgency is Critical
- If Asset Priority is High and Event Severity is Unknown, Low, or Medium, the Event Urgency is Medium
- If Asset Priority is Medium and Event Severity is High, the Event Urgency is High
- If Asset Priority is Medium and Event Severity is Critical, the Event Urgency is Critical
- If Asset Priority is Critical and Event Severity is Unknown or Low, the Event Urgency is Medium
- If Asset Priority is Critical and Event Severity is Medium, the Event Urgency is High
- If Asset Priority is Critical and Event Severity is High or Critical, the Event Urgency is Critical
Note: Correlation searches do not use the calculated severity described if the events being searched contain a severity value (that is, a field named "severity").
How to suppress notable events
In some cases, you might want to prevent certain types of notable events from appearing on the Incident Review dashboard or contributing to alert thresholds. To do this, you need to create a notable event suppression. See "Suppressing notable events" in this manual.
| Create new correlation searches | Configure Incident Workflow |
This documentation applies to the following versions of Splunk® App for PCI Compliance: 2.1.1
 Download manual
Download manual
Feedback submitted, thanks!