Privileged User Activity
This report shows raw events associated with privileged user activity and provides you with a report of all administrative activity. Use this report to evaluate privileged user accounts and review the activity to identify potential security threats that can lead to potential cardholder data compromise.
Accounts with increased privileges, such as the administrator and root accounts, can have an impact on the security or operational functionality of a system. PCI DSS requires that all actions taken by individuals using administrative credentials be monitored for misuse and abuse.
Relevant data sources
Relevant data sources for this report include any data that includes a privileged user account reference.
How to configure this report
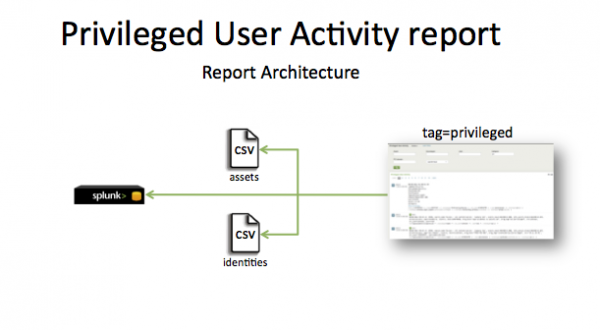
1. Index privileged activity from all systems, applications, and devices.
2. Add a category of privileged to all privileged user identities in the identity table.
3. (Optional) Tag specific events as being privileged using a tag of privileged.
Report description
The data in the Privileged User Activity report shows raw events. The view uses a raw event search that is initiated at dashboard load time, based on the selected time frame. See the View full results link to go back to the flash timeline.
Useful searches and Troubleshooting
| Troubleshooting Task | Search/Action | Expected Result |
|---|---|---|
| Verify that you have data from your system, application, or device. | sourcetype=<expected_st> | Returns data from your systems, applications, and/or devices. |
| Verify that all privileged activity is returned. | tag=privileged | Returns privileged user activity data. |
| Verify that all privileged user activity fields are populated. | tag=privileged | table event_id host sourcetype src_user user eventtype | Returns a list of events and privileged user activity fields of data. |
| System Time Synchronization | PCI Asset Logging |
This documentation applies to the following versions of Splunk® App for PCI Compliance: 2.1.1
 Download manual
Download manual
Feedback submitted, thanks!