System Patch Status
This report collects information on the patch status of cardholder systems and provides visibility into the current patch state for systems within the PCI cardholder data environment. Use this report to identify systems that are not patched according to policy.
Many attacks use widely published exploits that can be avoided if systems are patched appropriately. PCI DSS requires that systems and applications are protected by installing the latest vendor-supplied patches. Splunk software uses the data from your patch management solution to generate this report.
Relevant data sources
Relevant data sources for this report include patch activity data from the native OS or a patch management tool (for example, Windows update, yum update, Lumension).
How to configure this report
1. Index patch activity data from the systems to be monitored.
2. Map the patch data to use the following Common Information Model fields:
signature_id,signature,status
3. Tag the patch activity data with system, update, and status.
4. Set the should_update column of the assets table to true for any asset that should be evaluated for patch activity.
Report description
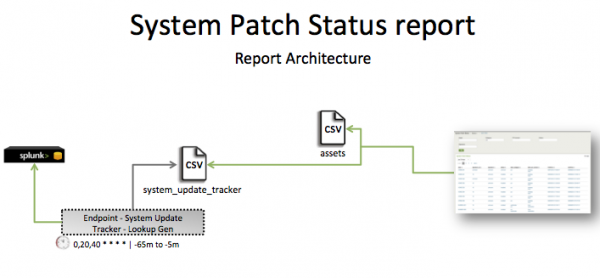
The data in the System Patch Status report is populated by the services_tracker lookup. This lookup is generated by the Endpoint - Services Tracker - Lookup Gen saved search.
This search runs on an offset 20-minute cycle and looks at 60 minutes of data.
| Schedule | 0,20,40 * * * * | Runs on an offset 20 minute cycle. |
| Report window | -65m@m to -5m@m | Looks at 60 minutes of data. |
Note: The report window stops at 5 minutes ago because some data sources might not have provided complete data in a more recent time frame.
Useful searches/Troubleshooting
| Troubleshooting Task | Search/Action | Expected Result |
|---|---|---|
| Verify that patch activity data is available in Splunk Enterprise. | tag=system tag=update tag=status | Returns system patch status data. |
| Verify that fields are normalized and available as expected. | tag=system tag=update tag=status | table signature_id, signature, status or `system_update` |
Returns a table of the system patch status data fields. |
| Verify that the system update tracker is populated as expected. | | inputlookup append=T system_update_tracker or | `system_update_tracker` |
Returns data in the system_update_tracker. |
| Patch Service Status | Anomalous System Uptime |
This documentation applies to the following versions of Splunk® App for PCI Compliance: 2.1.1
 Download manual
Download manual
Feedback submitted, thanks!