Deployment options
This section describes the deployment options to consider when deploying the Splunk App for PCI Compliance solution. It includes single server deployments, distributed deployments, the implications of deploying the product with other apps, and remote data collection.
The recommended deployment has the following components:
- Search head: A Splunk instance with a web interface that accepts users and directs search requests to one or more search peers. The search head must have the full Splunk App for PCI Compliance application installed. For larger deployments with many users, you might want to deploy multiple search heads.
- Indexer: A Splunk instance that indexes data, transforming raw data into events and placing the results into an index. Indexers must have an installation of the technology add-ons needed for the PCI app data inputs. An Indexer can perform other functions, such as data input.
- Forwarder: Light Splunk instances that collect and forward data to the indexers. Forwarders load balance data streams between indexers. Forwarders monitor files, run scripted inputs to gather data, and accept data over UDP or TCP ports.
Note: Heavy weight forwarders must have an installation of the technology add-ons needed for the PCI app data to function as intended. For technology add-on deployment considerations, treat them as an indexer and forwarder. They do not index data.
Components
The table shows which Splunk App for PCI Compliance files need to be installed on each component of a distributed deployment.
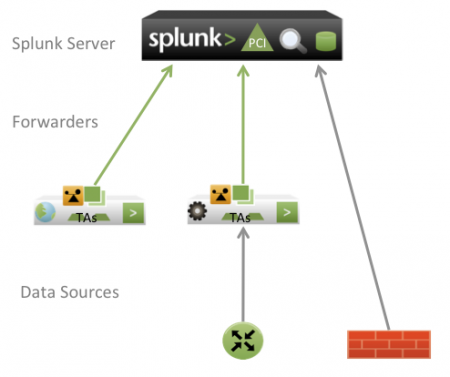
Single-server deployment
For small deployments, the Splunk App for PCI Compliance can be installed on only one server. In this deployment scenario, the PCI app is installed on a single server that acts as both a search head and an indexer. This configuration supports one or two users running concurrent searches, and is commonly used in a lab or test environment. When installing the PCI app in a single server environment, do not install other apps on the same server. Splunk forwarders are still used to send data from remote servers and applications into the single Splunk PCI instance.
See the "Install the Splunk App for PCI Compliance" section in this manual for details about hardware and software requirements.
See the Capacity Planning Manual for information about the limitations of a single-server deployment.
Use a minimum of two servers be used in a PCI deployment. Use one as a dedicated search head, and one as a dedicated indexer. This configuration enables solutions administrators to expand and scale as needed to support other apps and solutions.
Install an existing (and running) instance of Splunk Enterprise:
- Download the app.
- Install the app.
- Configure the app.
This diagram shows a typical single server deployment of the Splunk App for PCI Compliance on a Splunk server.
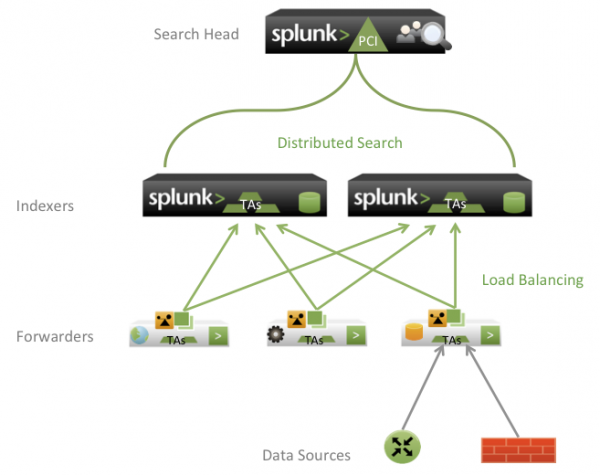
Distributed deployment
A distributed deployment is a collection of two or more Splunk indexers and a dedicated search head. Multiple indexers allow Splunk software to distribute the workload of processing the incoming events while also improving search performance by splitting the search overhead across multiple servers. See "Summary of performance recommendations" in the Capacity Planning Manual, which includes the amount of indexing and searching that make a distributed deployment necessary.
Note: Use a dedicated search head when deploying the Splunk App for PCI Compliance in a distributed deployment.
The following diagram shows a typical distributed deployment.
For a multiserver deployment, you need to add your indexers as search peers on the Splunk Enterprise instance that you designate as a search head. Use Splunk Web by clicking on Manager > Distributed Search from the Splunk App for PCI Compliance dashboard.
See "Distributed Splunk Enterprise overview" in the Distributed Deployment Manual for information on multiserver deployment. See "Using the deployment server" in this manual for information about the Splunk deployment server.
Technology add-ons
You only need to deploy the technology add-on to the indexers if the technology add-on includes index-time operations. To validate that a technology add-on includes index-time operations, review the README file included with the technology add-on.
Deploying in a virtual environment
Things to keep in mind when installing the Splunk App for PCI Compliance in a virtual machine include:
- Hardware and software requirements are the same for an installation of the Splunk App for PCI Compliance in a virtual environment. You still need appropriate resources for the data load.
- Oversubscription of the virtual machine leads to poor performance.
See "Virtual Hardware" in the Capacity Planning Manual.
Deploying with other apps
The Splunk App for PCI Compliance relies on the knowledge supplied in the technology add-ons. These add-ons specify the complex data processing necessary to optimize, normalize, and categorize your compliance data for use in the PCI Compliance solution. Apps and add-ons that have been developed separately might include data knowledge that has not been normalized for the Splunk App for PCI Compliance and can overwrite fields that the app uses, preventing the proper functioning of the searches, dashboards, and reports that rely on those fields.
Note: For optimal performance of the Splunk App for PCI Compliance, install on a dedicated search head without other apps installed and that indexers only use the necessary PCI Compliance-compatible technology add-ons.
In some cases, it might be necessary to install other apps on the same search head or server as the Splunk App for PCI Compliance. Many apps and add-ons provided by Splunk software are compatible with the PCI Compliance solution. Compatible apps are documented as such on the Splunkbase download page for the app. Installing apps or add-ons that are not designated as compatible with the Splunk App for PCI Compliance can negatively impact performance of the app and prevent data from being processed correctly, preventing some data from showing up on dashboards.
Remote data collection
Use forwarders to collect data from remote systems ("Using forwarding agents"). A node where a forwarder is installed is a collection point for one or more data sources. The technology add-ons for those data sources should be installed on the forwarder, ensuring that the data is properly tagged. To manage and distribute technology add-ons across many forwarders, use the Splunk deployment server ("About deployment server") or a third party software distribution system.
| Platform and hardware requirements | Data management overview |
This documentation applies to the following versions of Splunk® App for PCI Compliance: 2.1.1


 Download manual
Download manual
Feedback submitted, thanks!