Configure identities
These identities (or user roles) are included as part of the Splunk App for PCI Compliance:
- admin
- pciadmin
- pcianalyst
- pciuser
Identities list
The identities list provides information about the users in your cardholder data environment, such as the user name, first and last name, and email address. Some of these fields, such as priority, watchlist, and endDate are used for dashboard charts and to calculate the urgency of notable events associated with identities. Other fields, such as "business unit" and "category", are used by the filters at the top of the dashboards. You can search on any of these fields from the identity list and use them while investigating events.
When an event contains a field that the Splunk App for PCI Compliance identifies as belonging to a specific identity, the app looks up the identity in the identities list and generates new fields that contain the information from the identities list. The identity information provides the app with contextual information about the identities involved in an event or related to a notable event that can allow a PCI compliance analyst or incident investigator to identify additional identity information such as priority, categories, business unit, watchlist, and other information. Administrators are encouraged to populate the identities list by either building an automated capture from an existing identity database or to simply populate the file manually.
There are several ways to modify the identities list for the Splunk App for PCI Compliance.
Modify the list from within the app:
See "Integrating third party data" for more information.
Update the CSV files directly on the operating system in your deployment:
Modify $SPLUNK_HOME/SA-IdentityManagement/lookups/identities.csv file. See Identities#Identities_list_location"Identity list location" for more information.
Create scripted inputs.
You can also create an automated integration script with an external CMDB or asset management system. See "Scripted inputs" for more information.
For more information about how Identity lists are used in the Splunk App for PCI Compliance, see "Identity Correlation" in the Splunk App for PCI Compliance User Manual.
Identities list location
The identities list is located under the Supporting Add-on for identities:
$SPLUNK_HOME/etc/apps/SA-IdentityManagement/lookups/identities.csv
You can modify the list by navigating to Configure > General > Lists and Lookups and using the lookup editor. For more information, see "Modify your identity list".
Identity fields
The first line of the identities.csv file lists all the identities fields:
Identity lookups are performed on the src_user and user fields at search time.
The table describes the identity fields.
| Field | Description | Examples |
|---|---|---|
| identity (key) | Pipe-delimited list of usernames representing the identity. | Mr. Tim, manager | admin |
| prefix | Prefix of the identity name. | Mr., Mrs., Ms., Dr. |
| nick | Nickname of the identity. | Bobby, Spud, Dr. Z |
| first | First name of the identity. | Gordon |
| last | Last name of the identity. | Tristler |
| suffix | Suffix of the identity name. | Jr., Esq., M.D. |
| Email address of the identity. | accounting@acmetech.com, gntrisler@acmetech.com | |
| phone | Phone number for the identity. | +1 (800)555-8924 |
| phone2 | Secondary phone number for the identity. | +1 (800)555-8924 |
| managedBy | Username representing manager of the identity. | lietzow.tim, a.koski |
| priority | Priority of the identity. | Value can be "low," "medium," "high," or "critical". For example, CEO would be "critical" |
| bunit | Business unit associated with identity | emea, americas. |
| category | Category of the identity. Can be a pipe-delimited list | intern, officer, pip, pci | ES, BD | PS |
| watchlist | Is the identity on a watch list? | Value can be "true" or "false |
| startDate | Start/Hire date of the identity. | 3/29/88 5:15 |
| endDate | End/Termination date of the identity. | 7/12/08 19:49 |
Integrating third party identity data
To integrate identity data from third party sources you can:
- Identity lists Identities
- Modify Lists and Lookups
- Create a custom scripted input
Using any of these options maps the identity data and use it as part of the Splunk App for PCI Compliance solution.
Create your identity list
1. To create or modify your identity list from within the app, click Configure.
2. Click Identities on the Configure panel.
3. Click Edit to edit the identities.csv file. Use the editor to manually make changes or additions to the identities file. One way to add content is to copy data from a spreadsheet (in CSV format) and paste it into the editor.
Note: The editor does not validate input. Make sure your changes are correct.
4. Click Save. The changes are saved to identities.csv. You must place this file on each search head in a distributed deployment.
You can also edit the $SPLUNK_HOME/etc/apps/SA-IdentityManagement/lookups/identities.csv file to make your changes or additions.
Update the list periodically to ensure that the Splunk App for PCI Compliance has reasonably up-to-date identity information. Update at least every quarter.
Modify your identity list
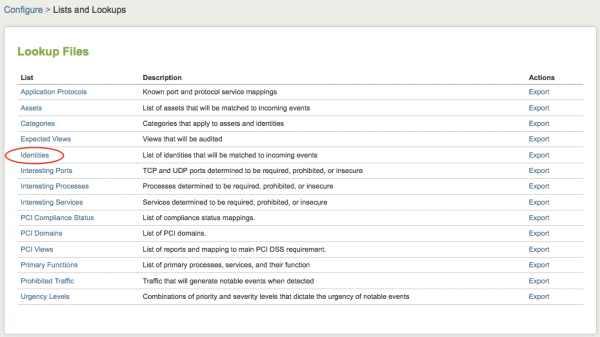
1. To modify your identity list from within the app, click Configure.
2. Click Lists and Lookups on the Configure panel.
3. Click Identities to edit the identities.csv file and make your changes or additions.
4. Click Save. This file must be placed on each search head in a distributed deployment.
Scripted inputs
Note: Splunk Enterprise loads the identities list at search time. You do not need to restart Splunk Enterprise after changes.
You can view Identities at any time by going to Resources > Identity Center in the Splunk App for PCI Compliance.
Identity categories
The category list specifies a list of categories that you can use for the category field in the identities list. The category list can be any set of categories you choose. Common examples are compliance and security standards (such as PCI) governing the identities, or functional categories (such as officer, pci-analyst, and so on).
These user categories are available in the Splunk App for PCI Compliance.
| Category | Description |
|---|---|
| cardholder | cardholder user |
| contractor | contractor user |
| default | default user |
| intern | temporary intern user |
| officer | user who is an officer of the company |
| pci | PCI analyst or PCI compliance manager |
| privileged | user with additional privileges |
| sox | Sarbanes–Oxley user |
You can edit this list by navigating to Configure > Lists and Lookups > Categories. For more information, see "Modify your identity list".
Identities and PCI compliance
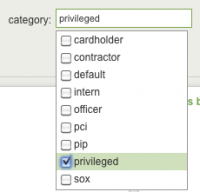
In the Identity Center, the Category field displays these identity categories, available for use as filters.
This filter restricts the view to events related to privileged access. You can use the dashboard filters to show only privileged access, or any other identity category.
Privileged accounts: Any account that is known to have administrator or super-user access is considered "privileged" (such as root or administrator accounts).
To edit this list of categories, navigate to Configure > Lists and Lookups > Categories. For more information, see "Modify your identity list".
Configure user roles
Splunk Enterprise includes a built-in user management system and also provides facilities for integration with external authentication systems such as LDAP or SSO systems. Splunk authentication allows you to add users, assign them to roles, and give those roles custom capabilities as needed for your organization. The Splunk App for PCI Compliance uses the Splunk rights management system to manage access and authentication via rights and roles. Additional roles are created for the various types of users who work with Splunk App for PCI Compliance.
- Use Settings > Access controls > Users to add users and assign roles.
- Use Settings > Access controls > Roles to set the capabilities that a role has.
See "About user authentication" in Securing Splunk Enterprise for information about setting up user authentication.
In Splunk Enterprise itself, the admin role has (almost) complete administrative access, and that role inherits all capabilities of the other roles. All Splunk Enterprise roles describe additive powers which are potentially inherited by other roles. This design avoids potential conflicts between the capabilities of two or more roles.
Splunk Enterprise has three predefined user roles: admin, power, user. The Splunk App for PCI Compliance adds three additional predefined user roles: pci_admin, pci_analyst, pci_user. All Splunk App for PCI Compliance users should be assigned appropriate roles in order to receive the capabilities that are necessary to perform their duties.
There are three conceptual categories of PCI compliance users used by the Splunk App for PCI Compliance:
- PCI Compliance Manager: Reviews PCI Compliance Posture, Protection Centers, and Audit dashboards in order to understand current PCI Compliance Posture of the organization. PCI Compliance Managers generally do not configure the product or manage incidents.
- PCI Compliance Analyst: Uses PCI Compliance Posture and Incident Review dashboards to manage and investigate PCI compliance incidents. PCI Compliance Analyst are also responsible for reviewing Protection Centers and providing direction on what constitutes a PCI compliance incident. Generally, they define the thresholds used by correlation searches and dashboards. A PCI Compliance Analyst needs to be able to edit correlation searches and create suppressions.
- PCI Compliance Administrator: Installs and maintains Splunk Enterprise and Splunk Apps. This user is responsible for configuring workflow, new data sources, tuning of rules, and troubleshooting the application.
Each user type requires different levels of access to perform its assigned functions. The following table outlines the various capabilities required by the different functions.
| Role | PCI Compliance Manager | PCI Compliance Analyst | PCI Compliance Administrator |
|---|---|---|---|
| pci_user capabilities | |||
| pci_analyst capabilities | |||
| admin capabilities |
In the following table, each row inherits the role of the rows above it, and the capabilities of that role.
| Splunk role | Inheritance | Notes |
|---|---|---|
| user | Inherits no other roles by default and cannot perform real-time searches. | View PCI compliance dashboards and search notable event indexes. |
| pci_user | Inherits the user role.
|
Have all the capabilities of a user, plus the ability to perform real-time searches. This role is assigned by a pci_admin.
|
| power | Inherits the user role but does not inherit the pci_user role.
|
Have all the capabilities of a user, in addition to the ability to perform real-time searches.The capabilities of pci_user and power are the same. However, you should use the pci_user role for PCI compliance users to facilitate upgrades with future capabilities.
|
| pci_analyst | Inherits the power and user roles' capabilities.
|
Can own notable events and perform workflow status transitions. This role is assigned by a pci_admin.
|
| pci_admin | Provides a grouping of capabilities necessary to administer the product. It inherits pci_analyst, pci_user, power, and user roles.
|
Can perform all capabilities of a pci_analyst and pci_user.Can edit correlation searches, edit review statuses, own notable events, and perform all workflow transitions. The pci_admin can also create and assign custom PCI compliance roles. The pci_admin role is a "container" for capabilities required to administer PCI compliance only.
|
| admin | The admin role inherits pci_admin, pci_analyst, pci_user, power, and user role capabilities.
|
Can administer the Splunk App for PCI Compliance with no additional capabilities. All Splunk Enterprise administrators are assumed to be PCI compliance administrators. |
Role inheritance
Understanding Splunk role inheritance is critical to managing PCI compliance roles. To delete capabilities (or permissions) from roles, Splunk Enterprise iterates through inheritance relationships. Removing an inherited role has collateral effects.
Editing pci_admin and removing pci_analyst from "Inherited Roles" removes any capabilities that were inherited by pci_analyst, unless they were explicitly granted to pci_admin.
For example, pci_admin inherits the pci_analyst capabilities, and therefore has the can_own_notable_events capability. Removing can_own_notable_events from pci_analyst impacts pci_admin as well. If an administrator edits the pci_admin role and explicitly enables the can_own_notable_events capability, then pci_admin retains the can_own_notable_events capability even after removing the inherited pci_analyst capability of can_own_notable_events.
Note: The pci_admin role does not explicitly grant the edit_log_review_settings capability needed to edit log review settings. This is a known limitation. The admin role inherits this capability by default.
See "Add and edit roles with Splunk Web" in Securing Splunk Enterprise.
Set up concurrent searches
By default, Splunk Enterprise only allows three searches to be run concurrently for 'user' and 'power' roles. When you install the Splunk App for PCI Compliance, it increases these values to ten by default because dashboards generally execute more than three searches. You might want to change the number of concurrent searches.
To change the number of concurrent searches:
- Click Manager.
- Click Apps.
- Select Setup next to PCI Compliance.
- Change the number of concurrent searches for either the
adminor thepoweruser. - Click Save.
To manually change the default search quota by editing the authorize.conf file:
Edit the file at $SPLUNK_HOME/etc/system/local/authorize.conf and set srchJobsQuota for each role.
See the following example:
[role_user] srchJobsQuota = 15 [role_power] srchJobsQuota = 15
Edit notable event suppression for a new user or role
The first part is done using Splunk Web, and the second part requires you to edit a file.
To enable non-admins to have the ability to create notable event suppressions, in Splunk Web, do the following:
1. Log in as admin.
2. Navigate to Manager > Access Controls > Roles.
3. Select the role (for example, pci_analyst) to modify.
4. In the editor, add edit_suppressions to the role.
5. Cilck Save.
The suppression of notable events is an event type. Add the modified role to a list of roles allowed to modify event types.
The second step, is make changes to the local.meta file to add this role to the list:
1. Edit the $SPLUNK_HOME/etc/apps/SA-ThreatIntelligence/metadata/local.meta file.
2. Make this addition for the pci_admin role:
##access = read : [ * ], write : [ admin,role2,role3 ] [eventtypes] access = read : [ * ], write : [ admin,pci_analyst ]
3. Save the file.
4. Restart Splunk Enterprise to enable the changes.
| Configure assets | Configure Primary Functions list |
This documentation applies to the following versions of Splunk® App for PCI Compliance: 2.1.1
 Download manual
Download manual
Feedback submitted, thanks!