Graylog integration for Splunk On-Call 🔗
Graylog is an open source centralized log management solution built to open standards for capturing, storing, and activating real-time analysis of terabytes of machine data.
Requirements 🔗
This integration is compatible with the following versions of Splunk On-Call:
Starter
Growth
Enterprise
The integration is compatible with Graylog version 3.1 and higher.
Splunk On-Call configuration 🔗
In Splunk On-Call, navigate to Integrations, Graylog.
Select Enable Integration and copy the Service API Endpoint for later use.
Graylog configuration 🔗
Create Splunk On-Call Notification 🔗
Open the web UI for Graylog at http://127.0.0.1:9000. From there, log in and go to Alerts Notifications and select Create Notification. Give the notification a title and description.
Select HTTP Notification for notification type and copy the Service API Endpoint from the previous field into the URL field.
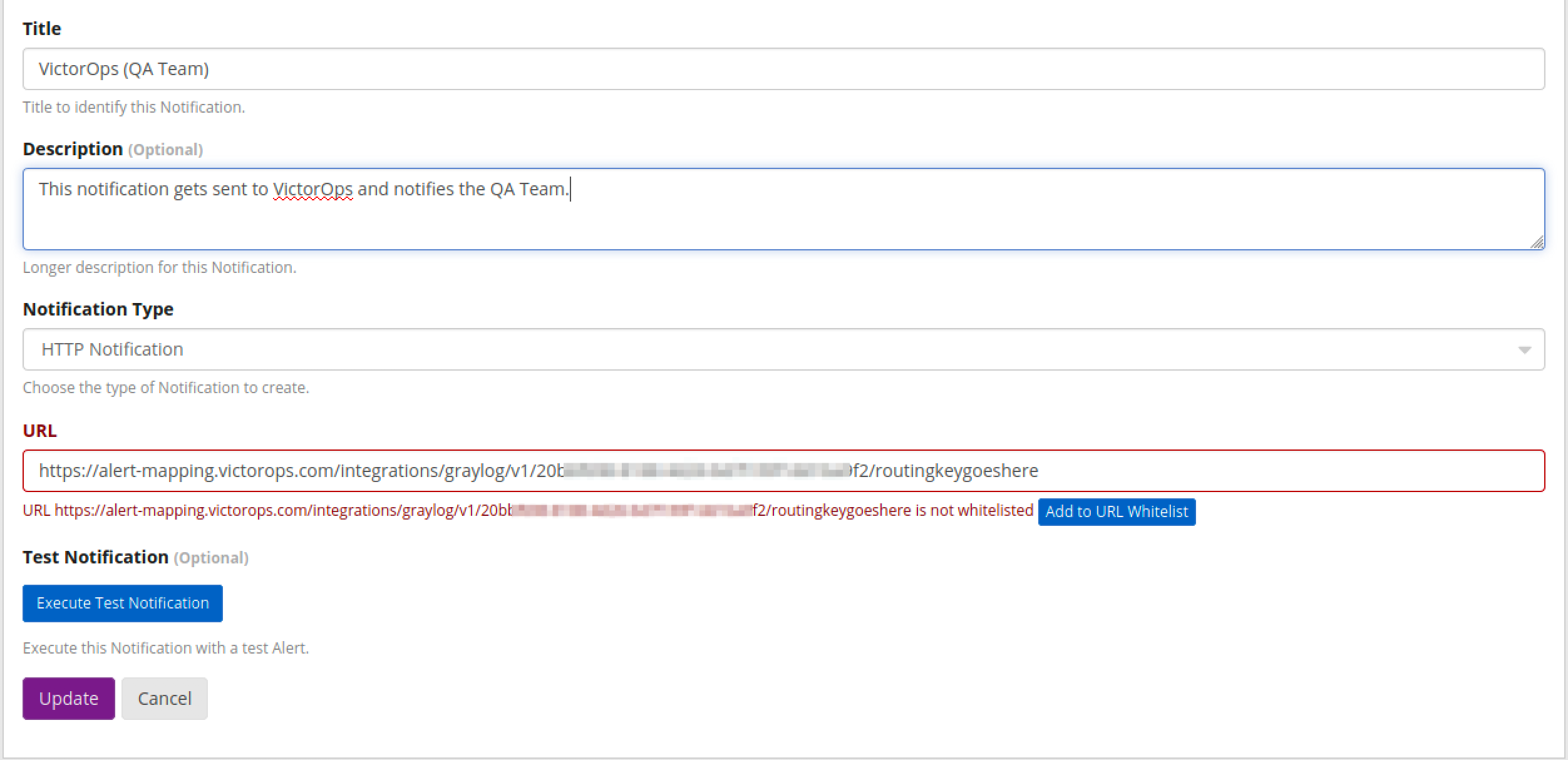
Put the appropriate routing key at the end of the URL and make sure to add it to Graylog’s allowed URL’s if needed.
Next select Execute Test Notification to produce a test alert on your timeline.

Select Create/Update to save the notification.
Note
If you’d like Graylog to notify multiple routing keys, you need to set up a new notification for each routing key.
Add Splunk On-Call notification to an event definition 🔗
Under the Alerts tab in Graylog, navigate to Event Definitions and either create a new event definition or edit a preexisting one.
Go to the Notifications tab of the event definition and select Add Notification. Select the notification you’ve created and select Done.

Splunk On-Call automatically aggregates alerts with the same event definition ID.