Outlyer integration for Splunk On-Call 🔗
Outlyer is a monitoring service for DevOps and Operations teams running Cloud, SaaS, Microservices and IoT deployments. Designed for today’s dynamic environments that need beyond cloud-scale monitoring, it makes monitoring effortless so you can concentrate on running a better service for your users. The following guide walks you through this integration.
In Splunk On-Call 🔗
From the Splunk On-Call web portal, select Settings, then Alert Behavior, then Integrations.
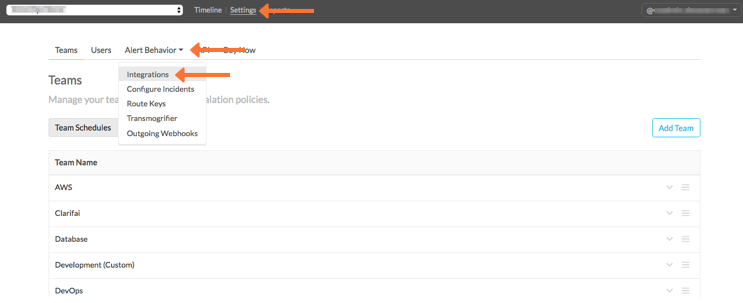
Select the Outlyer integration option.
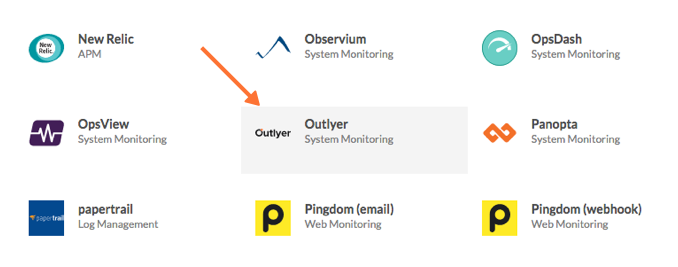
Select Enable Integration.
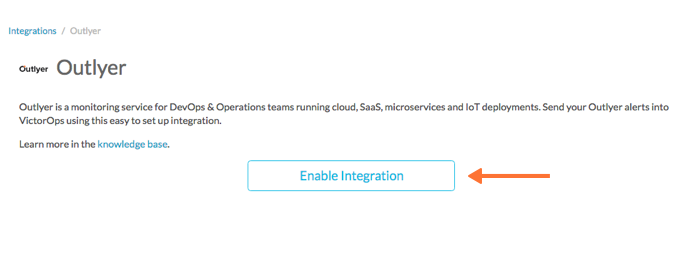
Copy the Service API Endpoint to the clipboard. Make sure to replace the “$routing_key” section with the actual routing key you intend to use.
Note
To view or configure route keys in VictorOps, select Alert Behavior, then Route Keys.
In Outlyer 🔗
From the Outlyer web interface, select the account you want to use for the integration.
Select Alerts from the sidebar.
Select an existing alert or ADD NEW ALERT if you need to create an alert to integrate.
Select ACTIONS.
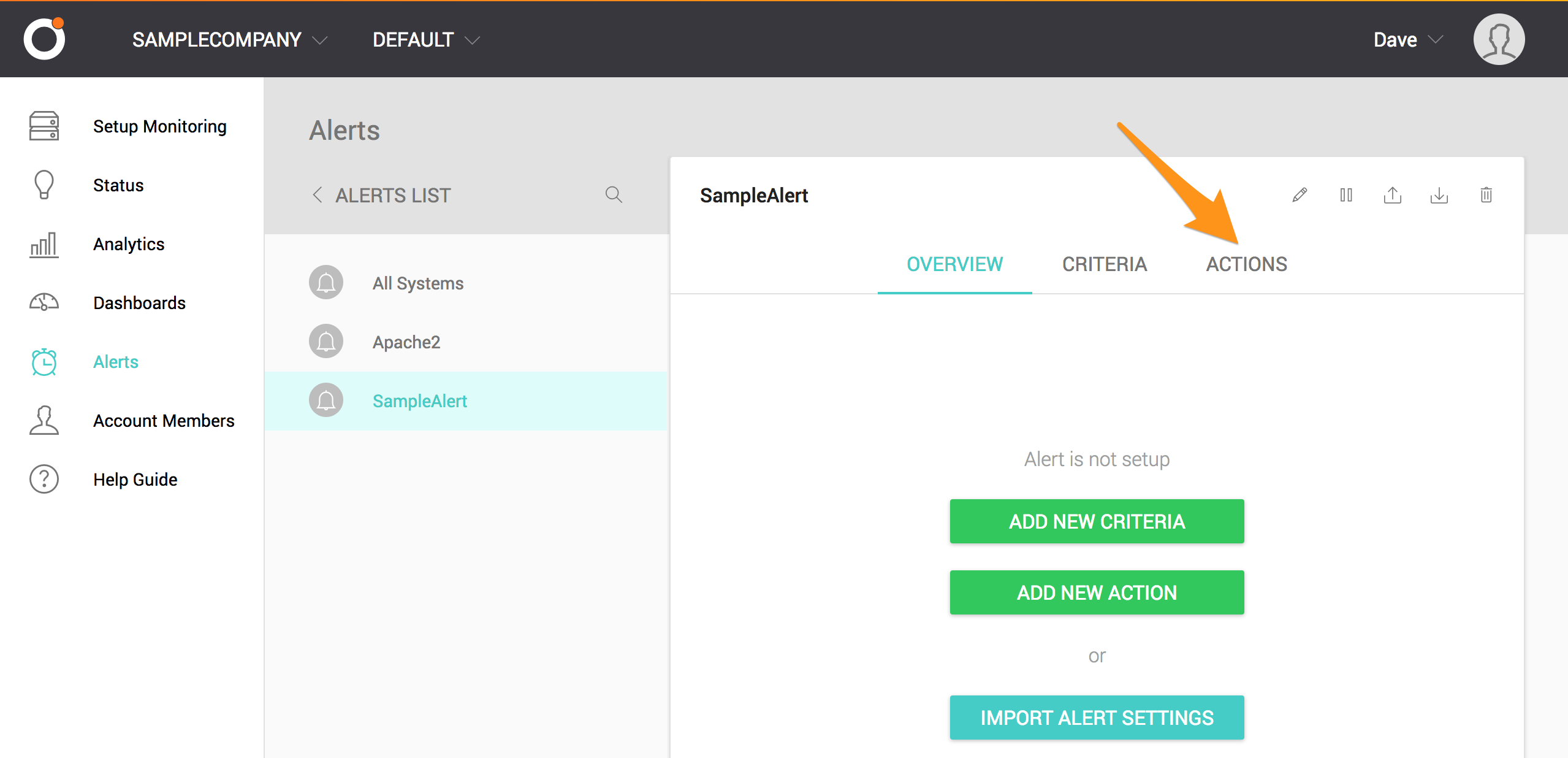
Select ADD NEW ACTION.
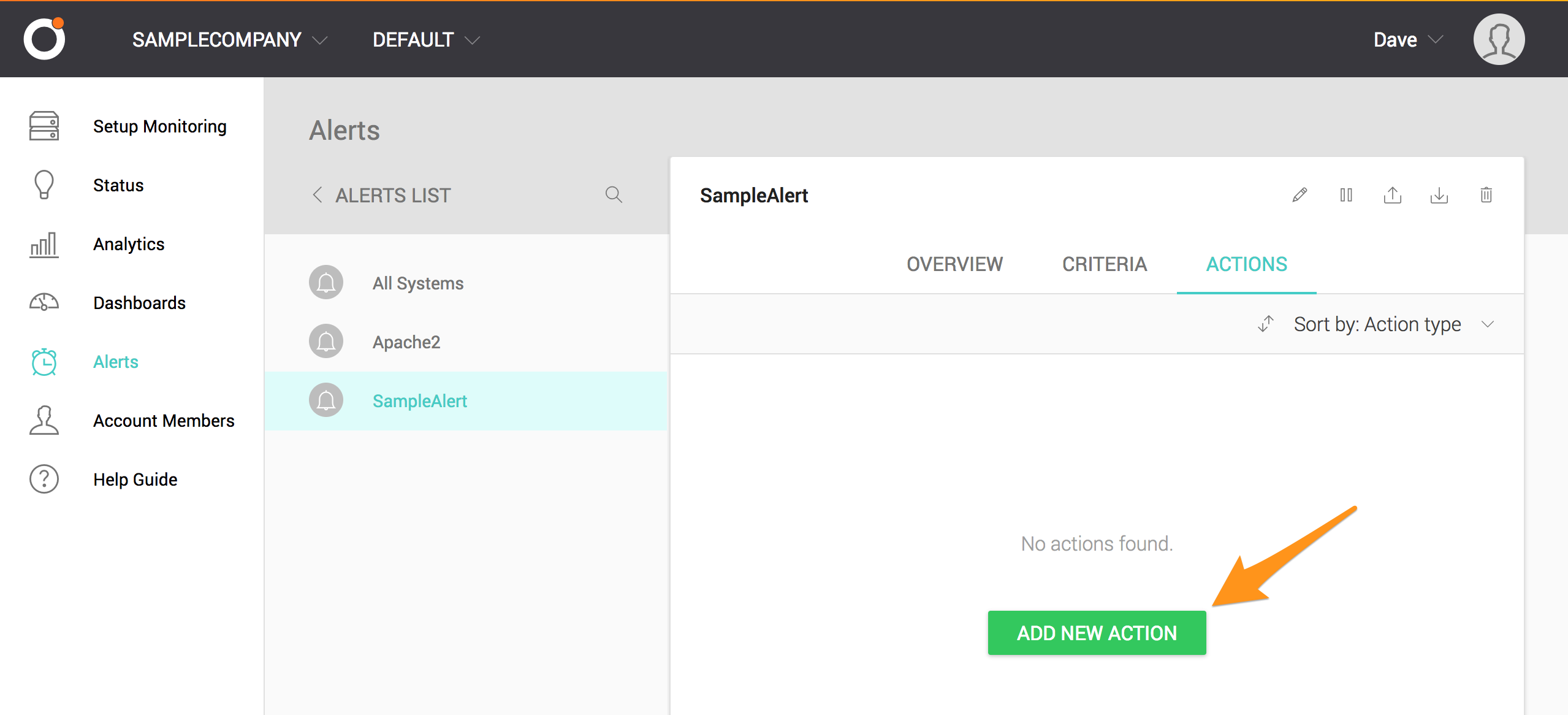
Select Call a Webhook from the dropdown menu.
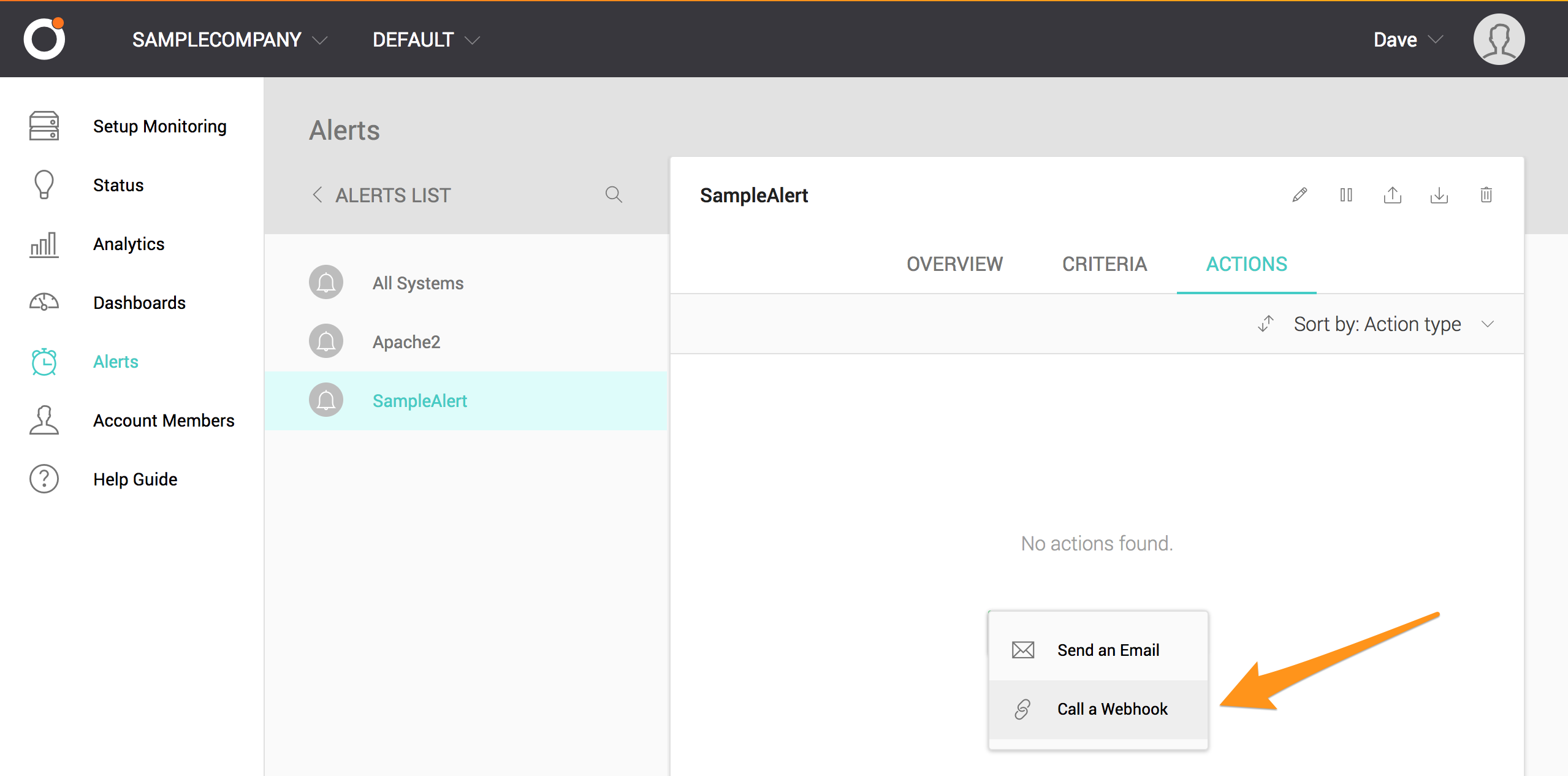
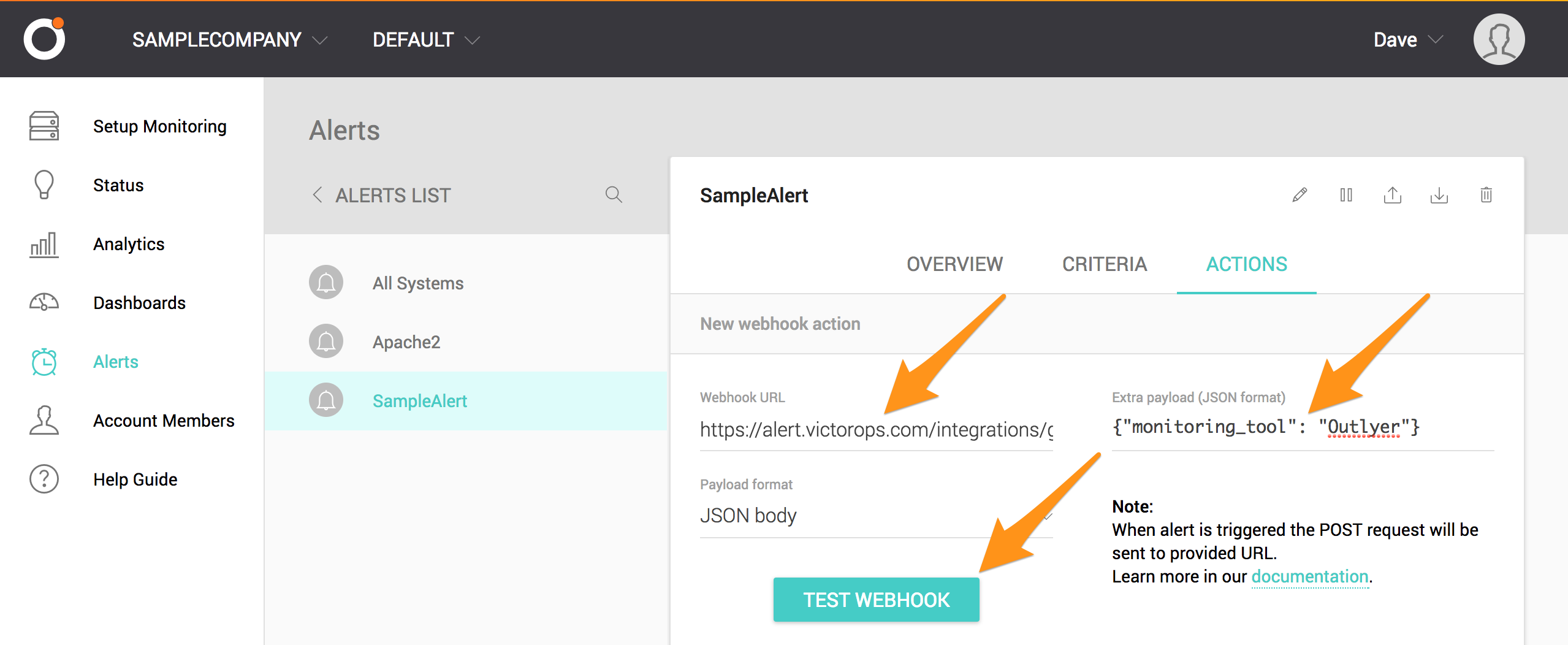
Paste the “URL to notify” that you copied from the
Splunk On-Call Integrations page for Outlyer in the “Webhook URL” field, then
enter "monitoring_tool": "Outlyer" inside the curly braces of the
“Extra payload” field. Finally, select TEST WEBHOOK.
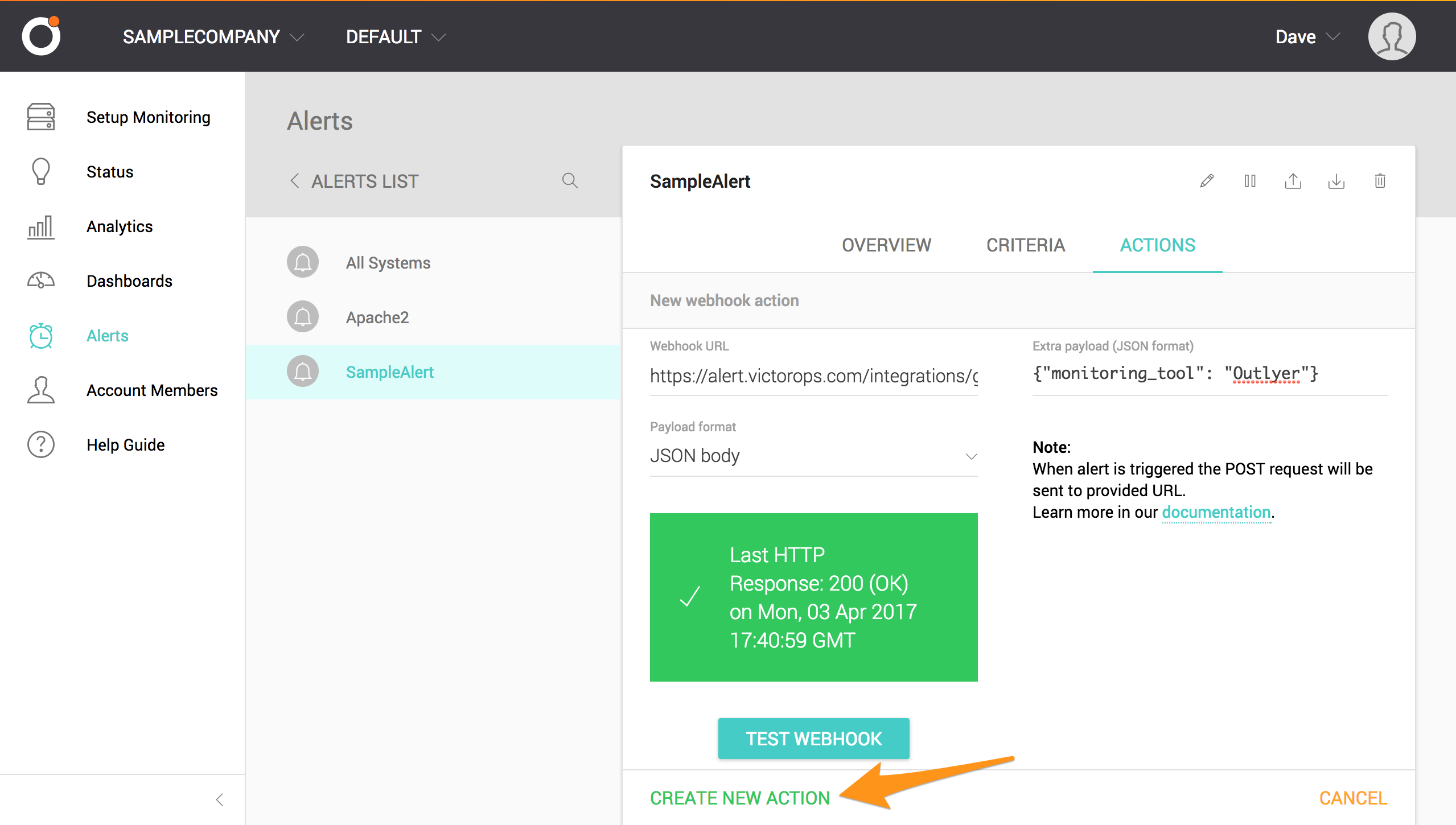
The test returns a green “Response: 200 (OK)” message. Select CREATE NEW ACTION.
Check for the notification in Splunk On-Call.
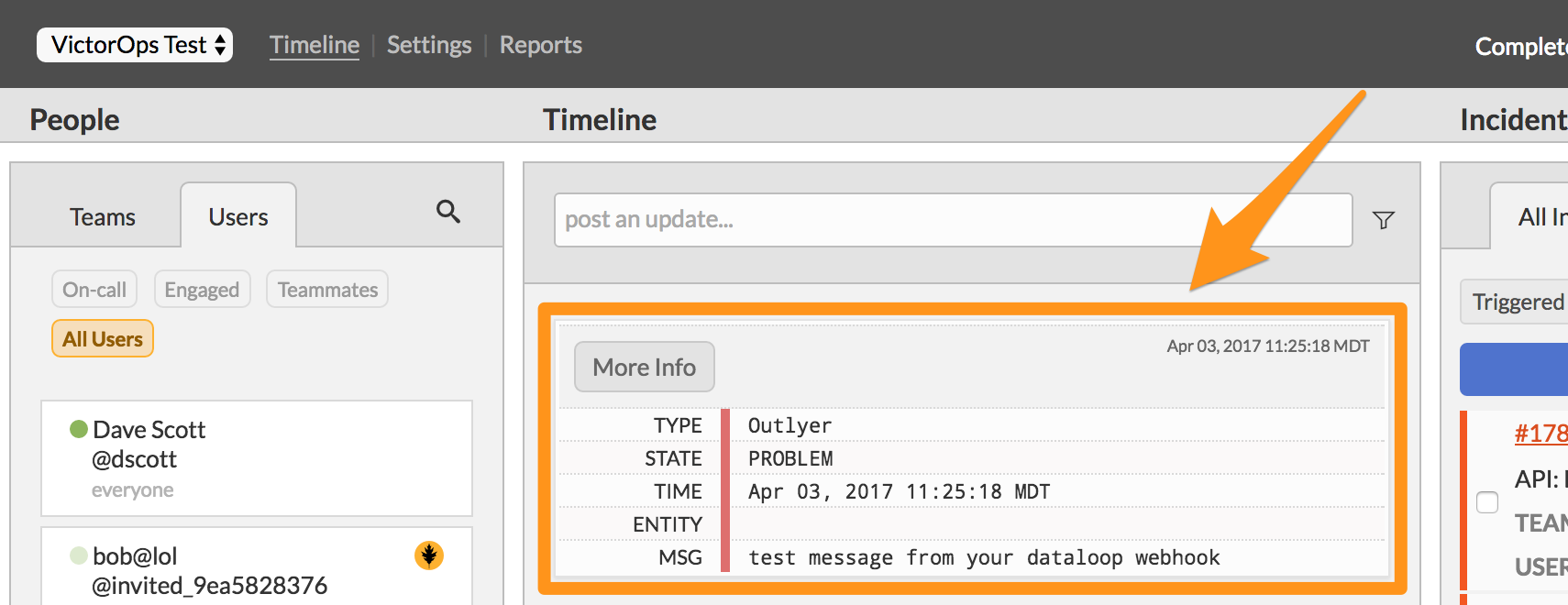
You have completed setting up this integration. If you have any questions, contact VictorOps support .