LogEntries integration for Splunk On-Call 🔗
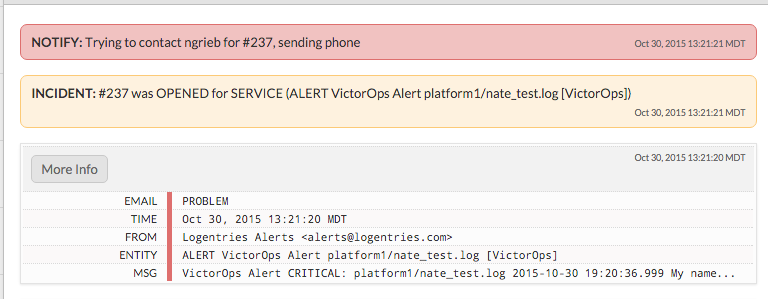
Logentries offers real-time log management and analytics at any scale. This integration allows you to send tagged Logentries alerts into Splunk On-Call using the Generic Email Endpoint. The following guide walks you through the steps needed to implement this integration.
Requirements 🔗
This integration is compatible with the following versions of Splunk On-Call:
Starter
Growth
Enterprise
Splunk On-Call 🔗
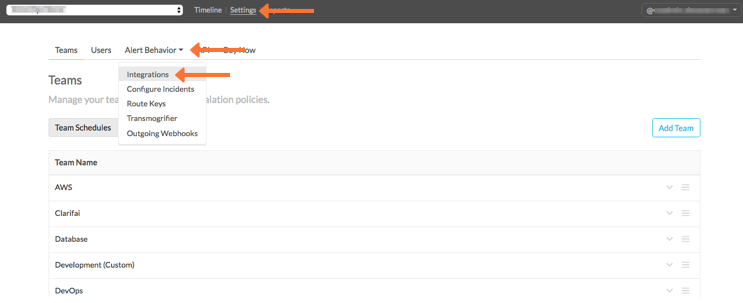
In Splunk On-Call, select Settings, Alert Behavior, Integrations, :guilabel:`LogEntries.
If the integration isn’t active, select Enable Integration to generate your endpoint URL. Copy the URL to the clipboard and replace the $routing_key fragment with the routing key you want to use. See Create Routing Keys in Splunk On-Call.
LogEntries configuration 🔗
From the main dashboard, select Tags & Alerts from the menu.
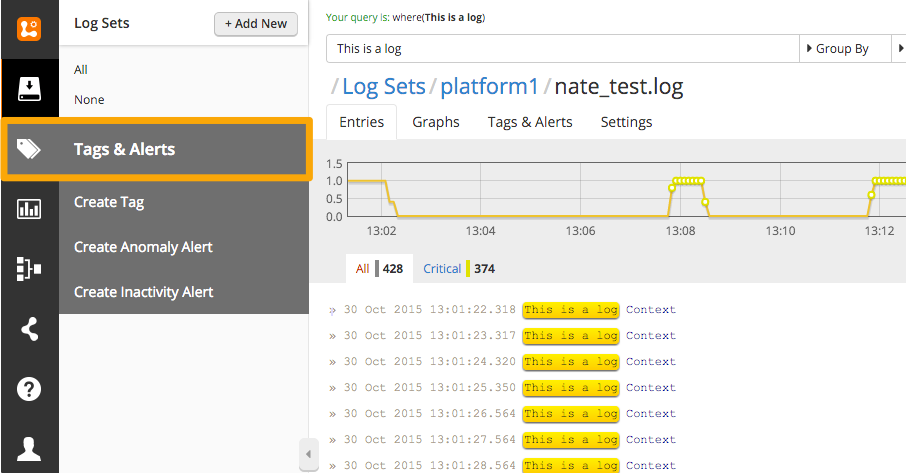
Edit an existing tag or create a new one. When naming the tag, append the Splunk On-Call severity level you want for that alert. For example appending the term warning creates a warning alert in Splunk On-Call, while appending the term critical creates a critical incident in Splunk On-Call.
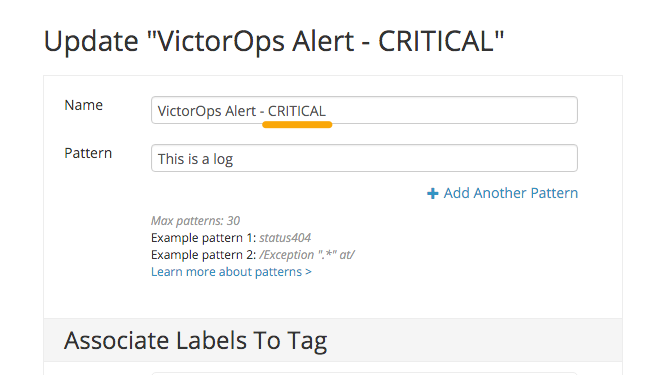
Add your Splunk On-Call email endpoint to the email addresses notified by the Logentries alert tag.
Now whenever the search is matched, an alert is sent to the Splunk On-Call timeline with the associated severity level.