Splunk On-Callインシデント頻度レポート 🔗
インシデント頻度レポートの目的は、インシデントに関連するデータとコンテキストをチームに提供し、インシデント管理対応を積極的に行うことです。
要件 🔗
このインテグレーションは以下のバージョンのSplunk On-Callと互換性があります:
エンタープライズ
Splunk On-Callタイムラインは、問題が発生した際にチームに完全な状況を伝えるリアルタイムの情報を提供しますが、インシデントの発生頻度レポートを使用して、事後のインシデントの流れを分析します。
インシデント頻度レポートにアクセスするには、Reports、Incident Frequency の順に移動します。
チームフィルタリング 🔗
All を選択することで、Splunk On-Callに寄せられるすべてのインシデントの全体像を把握することができます。また、個々のチームを深く掘り下げて、チームに影響を及ぼしている特定の問題領域を明らかにすることもできます。
セグメント化 🔗
問題の原因箇所を特定するのは困難です。そのため、フラッピングアラート、注意が必要なプラットフォームの部分、インシデントがどこから発生しているかを理解するための情報を特定する機能を提供します。インシデントをセグメント化するために、インテグレーション、ホスト、サービス、ルートキーの4つのオプションを提供します。
日付範囲とバケット化 🔗
インシデントのトレンドがチームに与える影響を日次、週次、月次で確認できます。範囲をどこまで細かく設定するかはユーザー次第です。
テーブルビューとホバー状態 🔗
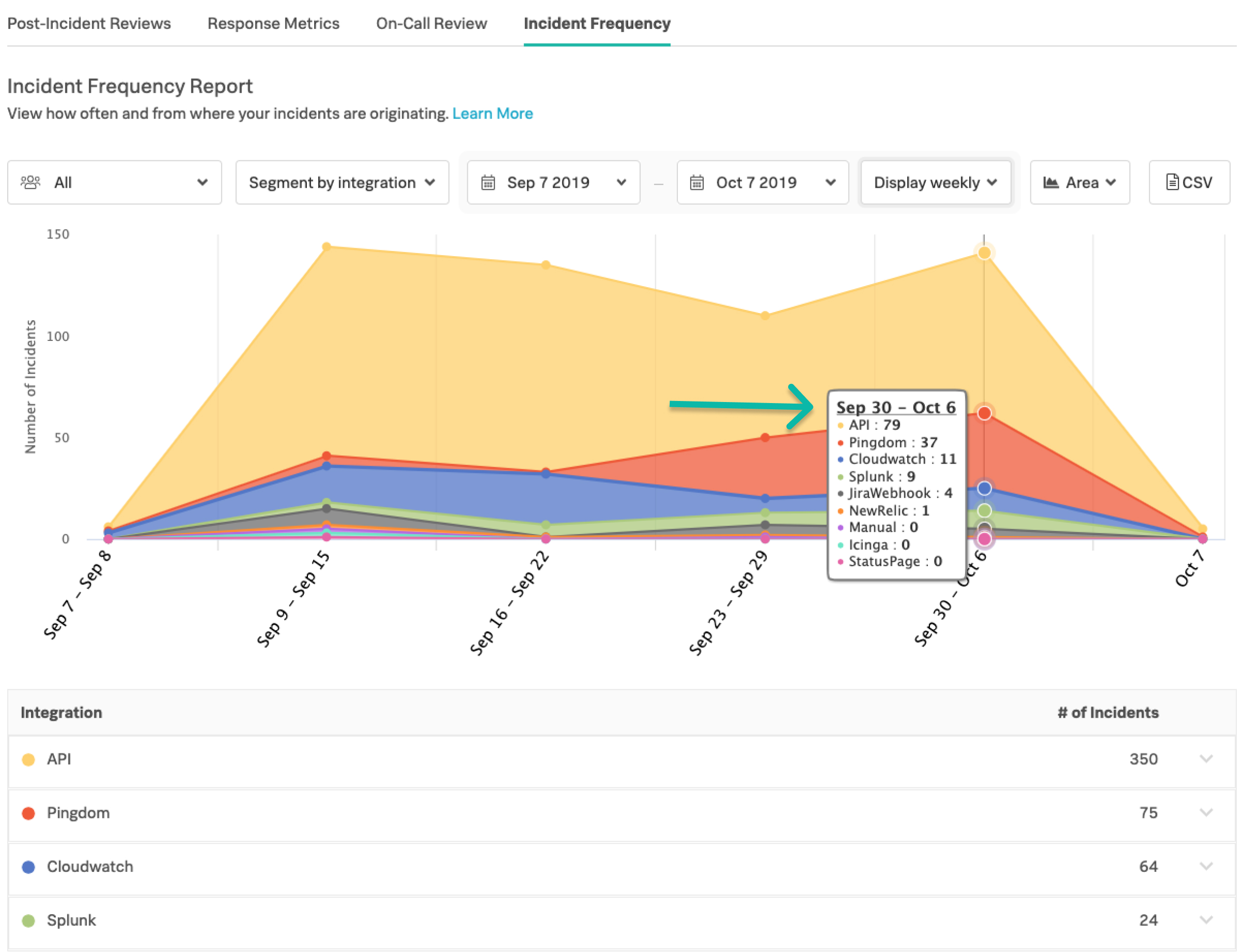
テーブルビューは、選択したセグメントフィルターに関連するインシデントの頻度上位15件に一致するように調整されます。
Hover State を見るには、グラフ上の任意の位置にカーソルを合わせると、ポップアップでその期間の情報が表示されます。そのホバー状態を選択することで、下の表は選択した期間に焦点を当て、時間バケット化の選択によって特定の期間に何が起こったかを強調します。Reset ボタンを選択することで、テーブルビューをリセットすることができます。注:ホバー状態の選択は、CSVの内容には影響しません。特定の日付範囲で CSVを分割するには、日付範囲ルールを調整します。
CSVダウンロード 🔗
CSVで配信されるデータは、設定ビューで設計された日付範囲とチームセグメントが常に反映されます。フィルターによるセグメントや日付範囲のバケット化を変更しても、ダウンロードの内容には影響しません。
CSVについての留意点:
タイムスタンプの粒度はミリ秒単位です
CSVはインシデントIDの降順でソートされます。
CSVファイルの列見出し 🔗
インシデント頻度CSVファイルをダウンロードする際、インシデントが記録された時間/タイムゾーンの単位を含む以下の列を見つけることができます。時間関連の列見出しは、これらの形式で表示されます:
確認時間(秒)解決時間(秒)インシデント開始時間(UTC)確認時間(UTC)解決時間(UTC)
インシデント頻度レポート:CSVフィールド定義 🔗
以下は、IFR CSVダウンロードのフィールドを定義するための簡単な用語集です。これらの定義は、インシデントフィールドの用語集とは異なる場合があります。
フィールド |
定義 |
|---|---|
インシデント番号 |
entity_idライフサイクルの一意の数値タグ。 |
ページングされたチーム |
トリガーされたインシデントによりチームがページングされます。 |
ページングされたエスカレーションポリシー |
トリガーされたインシデントによってページングされるエスカレーションポリシー。 |
ページングされたユーザー |
トリガーされたインシデントによってページングされた特定のユーザー。 |
エンティティID |
インシデントの中央識別子:entity_id。 |
エンティティ表示名 |
entity_idに影響を与えない、より簡潔で直感的なインシデント名:entity_display_name。 |
ルーティングキー |
インシデントを特定のチームに誘導するために使用されます:routing_key。 |
モニタリングツール |
定義されたインテグレーション。 |
サービス |
モニタリングツール内のチェックのタイプ。entity_display_nameフィールドから構築されます。 |
ホスト |
問題の特定の場所。hostnameまたはhost_nameフィールドから構築。 |
エンティティタイプ |
特定のレガシーインテグレーションのためのフィールド。 |
最後のアラートID |
ID: VO_UUID. |
アラート数 |
インシデントカードに描かれたアラートカウント。 |
アラート数 |
インシデントカードに描かれたアラートカウント。 |
インシデント開始時間 |
最初のページング時間。 |
トリガーされた時間 |
Splunk On-Callエンドポイントが受信した時刻:VO_ALERT_RCV。 |
確認時間 |
インシデント確認時間 |
解決した時間 |
インシデントが解決した時間。 |
確認者 |
このインシデントを確認したユーザー名を表示します: ack_author。 |
解決した時間 |
インシデントが解決した時間。 |
解決者 |
このインシデントを解決したユーザー名を表示します。 |
最後のアラート時間 |
最終アラートの時刻。 |
現在のフェーズ |
インシデントの状態:トリガー、確認、解決済み |