インシデント後レビューレポートの作成 🔗
Splunk On-Callのインシデント発生後レビューレポートでは、特定のインシデントや時間範囲にまつわるイベントの履歴を把握できるため、次に同じような状況が発生したときに、どのように問題を解決したかを文書化することができます。当社は、インシデントで何が起こったかをカタログ化するだけでなく、イベントを全体的に分析し、チームや組織がデータをより深く掘り下げるための実行可能なステップを定義することが重要だと考えています。
インシデント発生後のレビューレポートを作成するには、Splunk On-Call Webポータルにアクセスし、Reports を選択します。
Post-Incident Reviews オプションを選択し、New Report を選択します。タイトルを入力し、Create Report を選択します。
インシデント後のレビューレポートの設定 🔗
新規レポートを作成すると、メインレポート設定ページに入り、インシデントの影響に関するコンテキストをチームに提供および定義することができます。ここでは、レポートにタイトルを付け、日付範囲を設定し、編集権限を制限または共有し、インシデントが顧客に影響を与えたかどうかを選択します。将来のインシデント管理のガイドラインとなる詳細な*アクション項目*を作成することもできます。アクション項目を収集、追加することで、チームは現在のインシデントから学び、今後の対応を改善するためのステップを踏むことができます。
現在、レポートの日付範囲データリターンは4か月単位に制限されています。レポート範囲が定義されると、その期間に発生した全てのタイムラインイベントがレポートビルダーに入力されます。
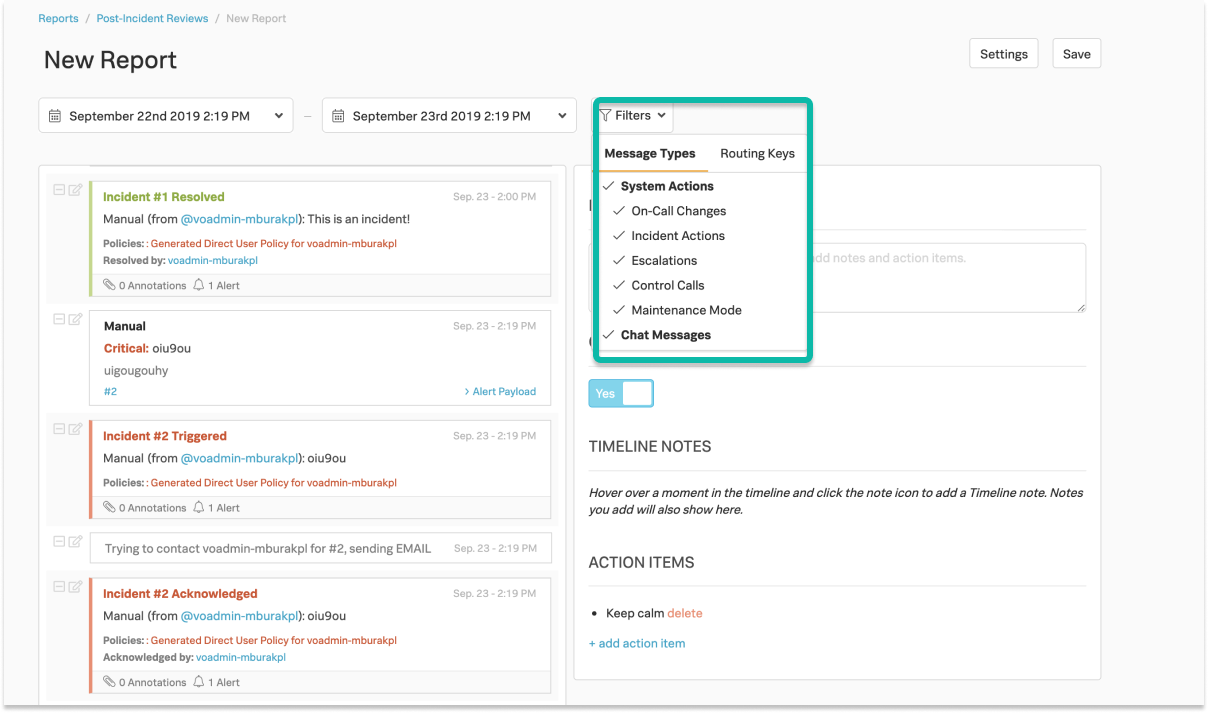
インシデント後レビューレポートの範囲の絞り込み 🔗
システムアクションやチャットメッセージを含むメッセージタイプ、またはルーティングキーでフィルターすることができます。
レポートビルダーの左側にある削除またはマイナス(-)ボタンを選択することで、アラート、アクション、または投稿を非表示にすることができます。
さらに、削除またはマイナス(-)ボタンのすぐ右にあるメモ帳と鉛筆のアイコンを選択することで、アラート、アクション、または投稿にメモを追加することができます。これらのメモは、インシデントまたはイベント中に何が起こったかを概要で分析するのに役立つように、メモが割り当てられている特定のイベントカードの下に表示されます。

注釈
概要フィールドとタイムラインメモは、次のページで説明されているマークダウンライブラリをサポートしています: Mastering Markdown。
アラートペイロードを選択すると、特定のインシデントカードに関連するフィールドと値が表示されます。
アラートルールエンジン による注釈は、インシデント後レポートにも表示されます。
インシデント後レビューレポートが完成したら、右上の Save を選択します。レポート作成後、印刷、PDF化、または再度開いて編集することができます。