ルールエンジンの注釈 🔗
注釈は、ルールのマッチング条件を満たすインシデントのペイロードに追加できる、情報またはリソースへのリンクです。URL、_image/spoc URL、またはプレーンテキストの注釈にすることができます。+ Add an Annotation を選択して、1つのルールに複数の注釈を追加できます。
要件 🔗
このインテグレーションは以下のバージョンのSplunk On-Callと互換性があります:
エンタープライズ
すべてのユーザーは、Splunk On-Callサポートにいつでも質問することができます。
ライブチャット:Splunk On-Callインスタンスにログインしている場合、Splunk On-Callサポートチームとライブチャットを行うことができます。
URL 🔗
URLにアノテーションを付ける場合、インシデントのペイロードでユーザーに表示されるテキストである「ラベル」を追加する必要があります。注釈を選択すると、ユーザーはそのURLに直接移動します。
モニタリングツールからのペイロードのフィールドにURLリンクが含まれている場合、変数展開(以下で説明)を使用して、そのフィールドの値を注釈にインポートすることができます。
変数展開:ルールエンジンは、アラートフィールドの内容をルールに取り込むことができるため、ユーザーはアラートのデータで注釈や変換を動的に更新することができます。これは、ペイロードフィールドを使用して構文( {{field\_name}} )で行うことができます。または、次の構文で正規表現(RegEx)キャプチャグループを使用することもできます: \ {{\\n}} (nはキャプチャグループの番号です)。
一般的な例:ランブックのURLをアラートに追加する
ルール:
When state_message matches Server is DOWN
アラートに次の注釈をつけます: URL [ドロップダウンから選択] ランブック[urlにリンクされたラベル]
次に、アラートのstate_messageがServer is DOWNと一致すると、アラートカードの」annotations」タブの下にランブックが表示されます。
画像URL 🔗
URLでホストされているすべての_image/spocは、インシデントのペイロードで_image/spocとしてレンダリングできます。
注釈
Splunk On-Callは添付ファイルを受け付けず、_image/spocを保存しません。インシデントに注釈された_image/spocは、URLリンクを介してホストされ、利用可能でなければなりません。
モニタリングツールからのペイロードのフィールドに_image/spoc URLが含まれている場合、変数展開を使って、このようにフィールドの値を注釈にインポートすることができます。
When field_of_your_choice matches * using wildcard
アラートに次の注釈をつけます: _image/spoc URL [selected from dropdown] Load Graph [label] ${{load_graph_field_name_here}}
備考 🔗
インシデントに注釈を付けると、特定のメッセージをプレーンテキストでユーザーに伝えることができます。メモは、More Info を選択すると、アラートの上部にあるアラート注釈セクションに表示されます。
アラートフィールドによる注釈の追加 🔗
アラートに注釈を追加できるのは、アラートルールエンジンだけではありません。アラートがRESTスタイルのインテグレーションに向けられる場合、アラートペイロードに適切な構文のフィールドを含めることで、注釈を自動的に作成することができます。
注釈
インシデントが確認状態にあり、同じ entity_idを持つ新しいアラートがSplunk On-Call Timelineに入ると、そのアラートはオープンインシデントの下に 集約されます。最新のアラートに含まれる新しい注釈は、インシデントの注釈タブに追加されます。注釈は各アラートペイロードにも反映されます。
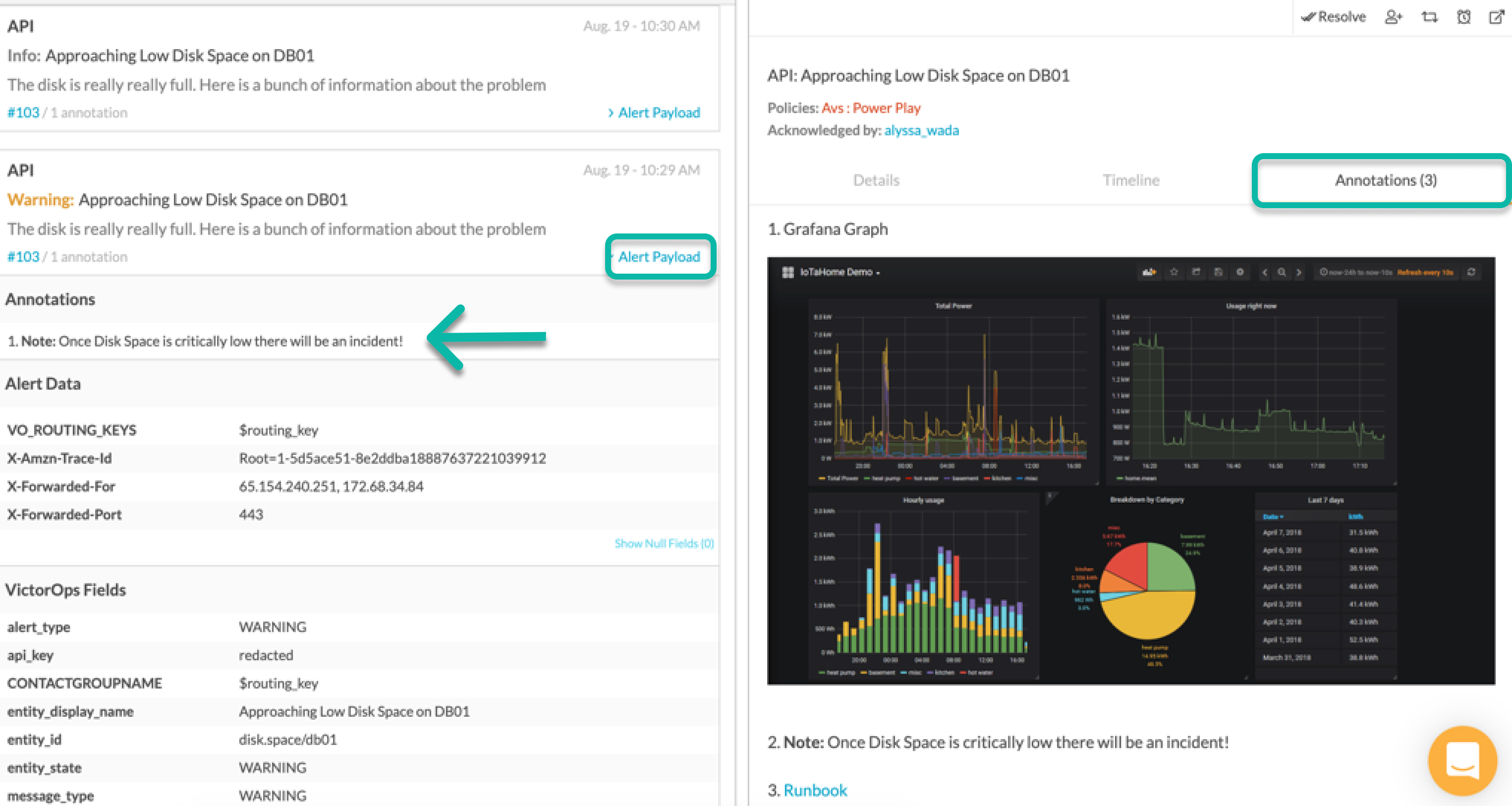
注釈ペイロード 🔗
Splunk On-Callでは、以下の構文で3種類の注釈を使用できます。注:注釈構文の最後に、注釈のタイトルをカスタマイズできます。たとえば、前述のスクリーンショットでは、URL注釈のタイトルはSplunk On-Callでは「Runbook」として表示されます。
ペイロードの例 🔗
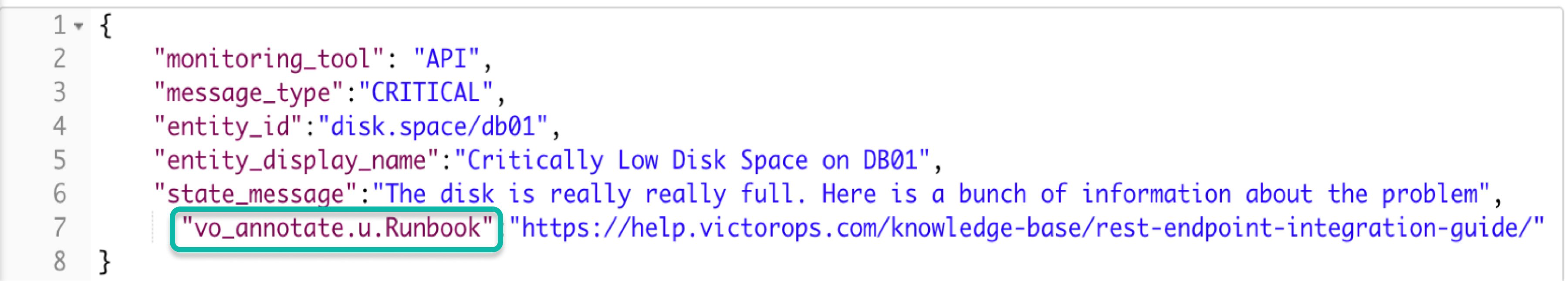
URL: vo_annotate.u.url
{ “monitoring_tool”: “API”, “message_type”:“INFO”,
“entity_id”:“disk.space/db01”, “entity_display_name”:“Approaching Low
Disk Space on DB01”, “state_message”:“The disk is really really full.
Here is a bunch of information about the problem”,
“vo_annotate.u.Runbook”:“https://help.victorops.com/knowledge-base/rest-endpoint-integration-guide/”
}
注:vo_annotate.s.note`
注釈
注釈には1124文字の制限があります。
{ “monitoring_tool”: “API”, “message_type”:“INFO”,
“entity_id”:“disk.space/db01”, “entity_display_name”:“Approaching Low
Disk Space on DB01”, “state_message”:“The disk is really really full.
Here is a bunch of information about the problem”,
“vo_annotate.s.Note”:“Once Disk Space is critically low there will be an
incident!” }
Image URL: vo_annotate.i.image
{ “monitoring_tool”: “API”, “message_type”:“INFO”,
“entity_id”:“disk.space/db01”, “entity_display_name”:“Approaching Low
Disk Space on DB01”, “state_message”:“The disk is really really full.
Here is a bunch of information about the problem”,
“vo_annotate.i.Graph”:“https://community.iotawatt.com/uploads/db6340/original/1X/266a3917cc86317830ae9cda3e91c7689a6c73a7.png”
}