ルールエンジン: Splunk On-CallのカスタムアウトバウンドWebhook 🔗
要件 🔗
このインテグレーションは以下のバージョンのSplunk On-Callと互換性があります:
フルスタック
すべてのユーザーは、Splunk On-Callサポートにいつでも質問することができます。
ライブチャット:Splunk On-Callインスタンスにログインしている場合、Splunk On-Callサポートチームとライブチャットを行うことができます。
すべてのアラートは、タイムラインに到達する前にルールエンジンによって降順(上から下)に処理されます。つまり、ルールの順番は非常に重要です。ルールエンジンのメインページから、個々のルールをクリックしてドラッグし、順序を変更することができます。デフォルトでは、作成した新しいルールはリストの一番上に表示されます。
ルールを作成する際には、同僚の管理者がその目的を理解できるように、詳細な説明を加えるのが一般的な良い習慣です。
バーの右側にある記号を選択して、ルールを編集または表示します。
オプションには、ルールのオンまたはオフ、削除、プレビューが含まれます。ルールはデフォルトでオンになっています。
プレビュー 🔗
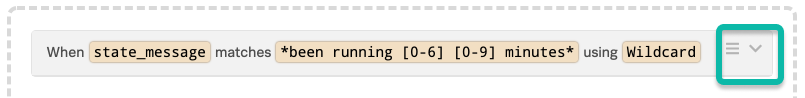
プレビューウィンドウを使うには、マッチング条件を設定し、編集シンボル(3本の水平線)を選択し、Preview を選択します。プレビューオプションはルールの右側に小さなウィンドウを開き、設定したマッチング条件を満たすタイムラインの最近のイベントを表示します。
これにより、タイムラインに戻ることなくアラートの内容を見ることができます。便利なトリックの1つは、非常に幅広いマッチング条件(パターンセクションでアスタリスク(*)を使用)を設定し、プレビューを開いて操作したいアラートを見つけることです。アラート上で More Info を選択すると、ペイロード全体が表示されます。任意のフィールドにカーソルを合わせてクリックすると、その選択にマッチするルールのマッチング条件が自動的に入力されます。
プレビューウィンドウを閉じるには、編集記号をもう一度選択し、Close Preview を選択します。
スコープの制限 🔗
一般的に使用される語句(例えば、」down 「や 「database」)に対してワイルドカードマッチングが必要な場面に遭遇することがあります。このような一般的なフレーズでマッチングを行うと、変更したくないアラートにルールが意図せず適用されることがあります。この問題は、ワイルドカードのマッチング条件の範囲を制限するために、一連の連続したルールを使用することで解決できます。
例えば、entity_idフィールドで 「staging 「という単語をキャッチし、これらのアラートをINFOアラートに変換して、午前3時にステージング環境で問題が発生した場合にインシデントを作成して誰にも通知しないようにしたいとします。しかし、ステージング環境に対してインシデントを作成したい場合もあるので、」staging 「というフレーズでマッチするルールを1つ作成することで、それを防ぐことができます。このケースでは、ある特定のモニタリングツール(New Relic)からのアラートにのみ影響を与えたいと考えています。
まず、モニタリングツールの値にマッチするルールが必要です。
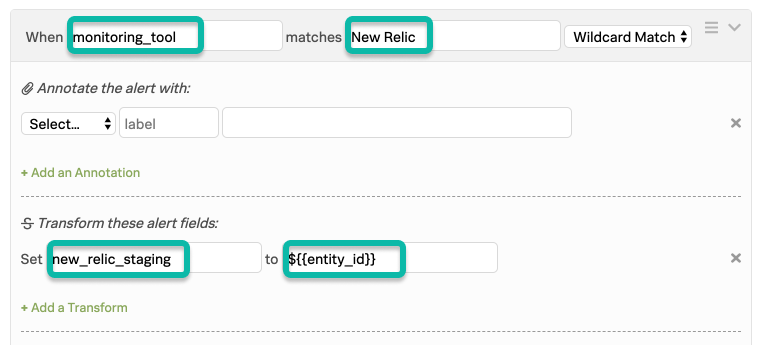
このルールのマッチング条件は、New Relicからのすべてのアラートをキャッチします。その後、変換アクションを使用して新しいフィールド (new_relic_staging)を宣言し、変数展開を使用して`entity_id`フィールドの値をその新しいフィールドにインポートします。これにより、New Relicからのすべてのアラートは、New Relicだけに固有の新しいフィールドを持つことになります。後続のルールは、この新しいフィールドに対してワイルドカードによるマッチングを使用します。
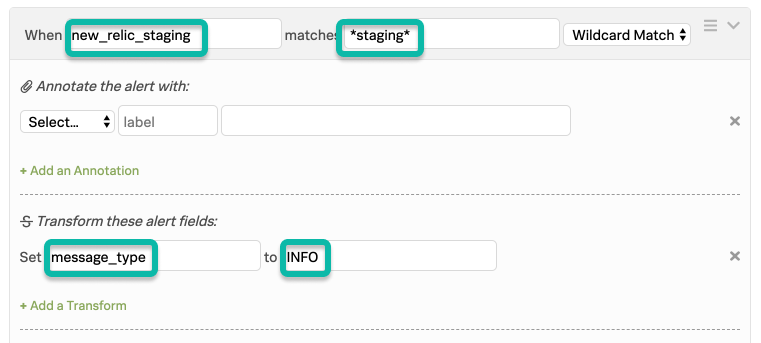
この2つ目のルールは、1つ目のルールの下に配置する必要があり、1つ目のルールによって作成された新しいフィールドにマッチし、ワイルドカードマッチングを使用して」staging」というフレーズをキャッチし、適切なアクションを実行します。これにより、ワイルドカードマッチングルールのスコープがNew Relicからのアラートのみに限定されます。
停止フラグ 🔗
ルールセットアップウィンドウの下部には、ルール適用後に処理を停止するオプションがあります。

Splunk On-Callに送信されるすべてのアラートは、タイムラインに到達する前に、ルールのリストを上から下へと通過します。このチェックボックスを使用すると、アラートが後続のルールの処理を続けないようにすることができます。これにはパフォーマンス上の利点(アラート処理の高速化)と、アラート処理後に後続のルールが現在のルールを上書きするのを防ぐことができます。