ルールエンジンの変数展開 🔗
ルールエンジンは、アラートフィールドの内容をルールに取り込むことができるため、ユーザーはアラートのデータで注釈や変換を動的に更新することができます。これは、ペイロードフィールドを使用して `{{field\_name}} で行うことができます。または、次の構文で正規表現(RegEx)キャプチャグループを使用することもできます: \ {{\\n}} (nはキャプチャグループの番号です)。
ペイロードフィールドによる変数展開 🔗
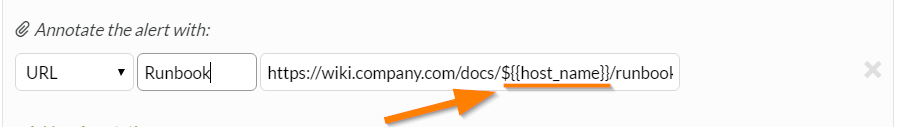
アラートから影響を受けたホストの名前を取り出し、wikiドキュメントのURLリンクに追加します。この情報を含むアラートのフィールドは`host_name`です
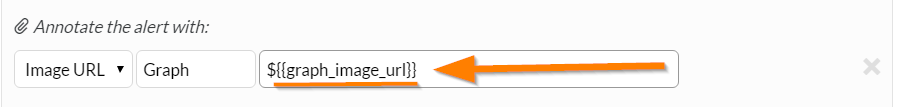
モニタリングツールから提供された画像リンクを注釈に変えます。
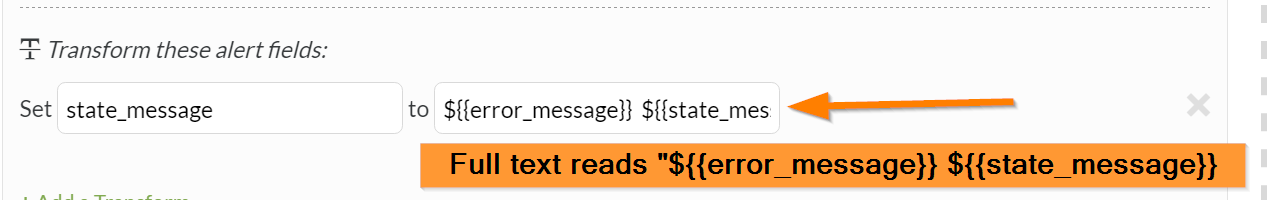
複数のフィールドを
state_messageに結合することで、ユーザーはそのフィールドの元の情報を失うことなく、通知により多くの情報を得ることができます。これは、含めたいフィールドがerror_messageであると仮定しています。
RegExキャプチャグループを使用した変数展開 🔗
正規表現キャプチャグループは括弧の中で定義されます。これらのキャプチャグループは、ペイロードフィールドと同じように変数展開に使用することができます。唯一の違いは、以下のようにキャプチャグループ番号で値を参照する必要があることです。
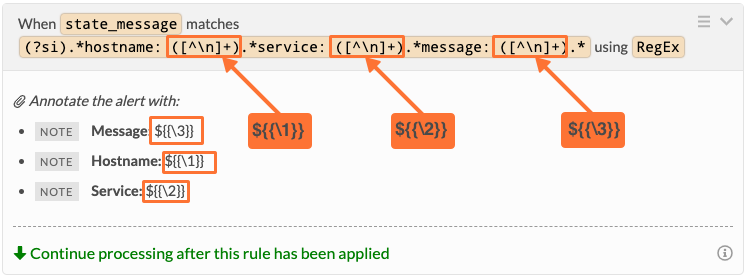
“([^\n]+)”は、改行文字でない1つ以上の文字をキャプチャします。