ルールエンジンのマッチング条件 🔗
マッチング条件は、ルールが適用されるタイミングを決定します。アラートのペイロード内に存在する任意のフィールドを選択し、直接マッチ、ワイルドカードマッチング、または正規表現を使用して、そのフィールドの特定の値にマッチさせることができます。
デフォルトでは、ルールエンジンはワイルドカードマッチングのみを使用します。正規表現を有効にしたい場合は、Splunk On-Callサポートにお問い合わせください。
要件 🔗
このインテグレーションは以下のバージョンのSplunk On-Callと互換性があります:
エンタープライズ
すべてのユーザーは、Splunk On-Callサポートにいつでも質問することができます。
ライブチャット:Splunk On-Callインスタンスにログインしている場合、Splunk On-Callサポートチームとライブチャットを行うことができます。
フィールド名 🔗
タイムラインでインシデントを表示する場合、フィールド名は左に、値は右に表示されます:
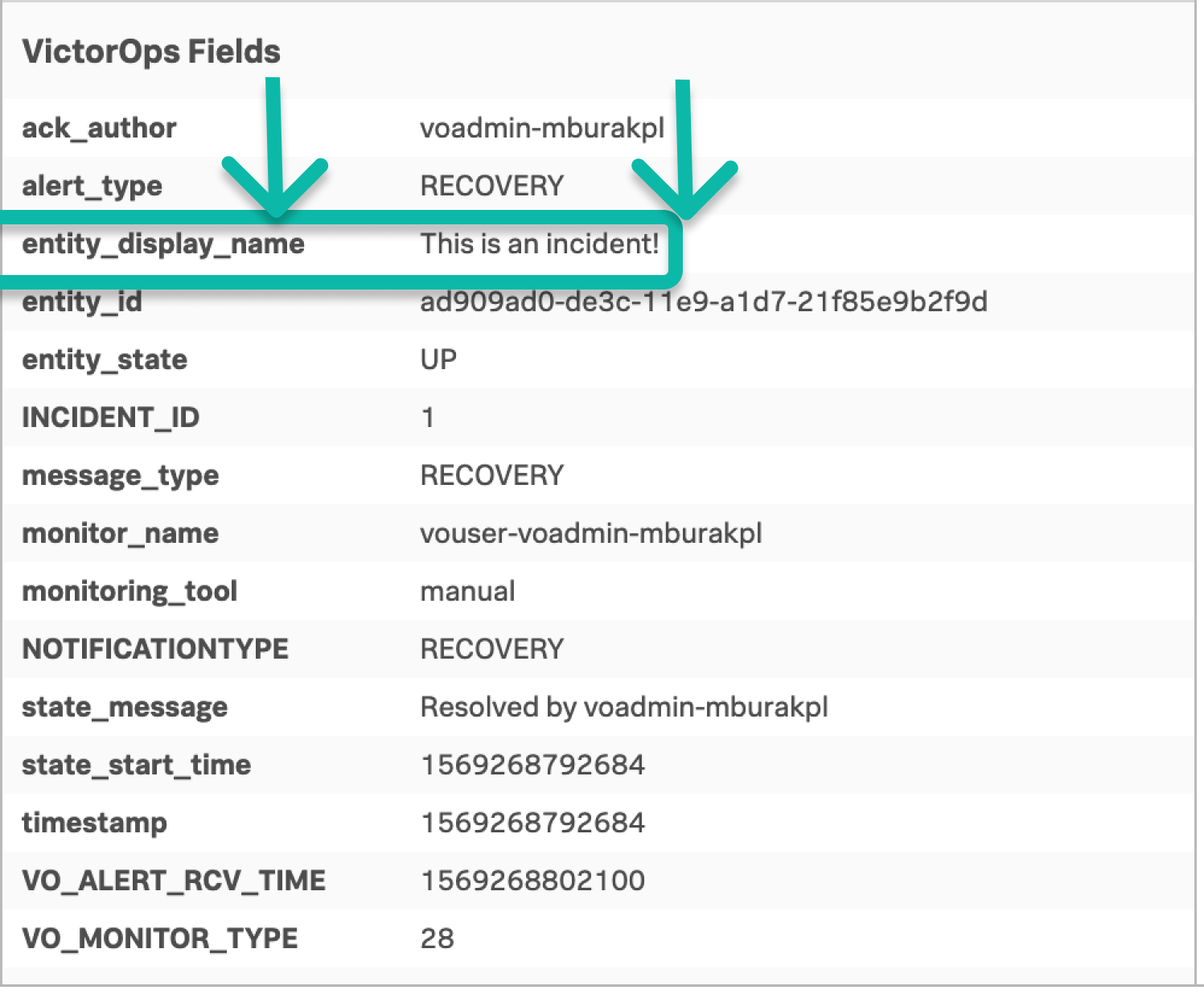
前述の例では、対象フィールドは entity_display_name フィールドで、重要な値はフレーズ This is an incident! です。マッチング条件は以下の通りです:

ワイルドカードマッチング 🔗
ルールは、簡略化されたワイルドカード構文を使用してアラートフィールド値にマッチし、文字列の一部またはすべてにマッチさせることができます。アスタリスク文字( * )は0文字以上にマッチし、マッチパターンのどこにでも使用できます。
ワイルドカードの例 🔗
Phrase |
マッチ |
一致しない |
|---|---|---|
|
|
|
|
|
|
|
|
|
正規表現によるマッチング 🔗
正規表現は、検索パターンを定義する文字です。正規表現を使用するルールを設定するには、メニューのオプションを に変更してください。オプションが表示されない場合は、サポートに連絡して高度な設定をオンにしてください。
注釈
正規表現ルールはタイムアウトの対象となり、細工された表現がSplunk On-Callインスタンスの安定性にリスクをもたらす場合は自動的に無効化されます。
以下の制限が適用されます:
Java正規表現に対応しています。
表現は現在128文字に制限されています。
大文字小文字を区別しない方法で複数行の入力にマッチさせるには、正規表現の先頭に
(?si)を追加します。前のテクニックは入力文字列全体にマッチするので、正規表現の最初と最後に
.*を追加する必要がある場合があります。
正規表現の例 🔗
Phrase |
マッチ |
一致しない |
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
ブーリアンロジック 🔗
異なるマッチング条件を持つルールを複製することで、ディスジャンクションロジック( OR )を使用することができます。
一連の連続したルールを正しく並べると、ルールエンジンで基本的な AND ロジックを実現することができます。スコープ制限ルールと同様に、最初のルールは、後続のルールが処理できる新しいフィールドを作成しなければなりません。
ANDロジックの例 🔗
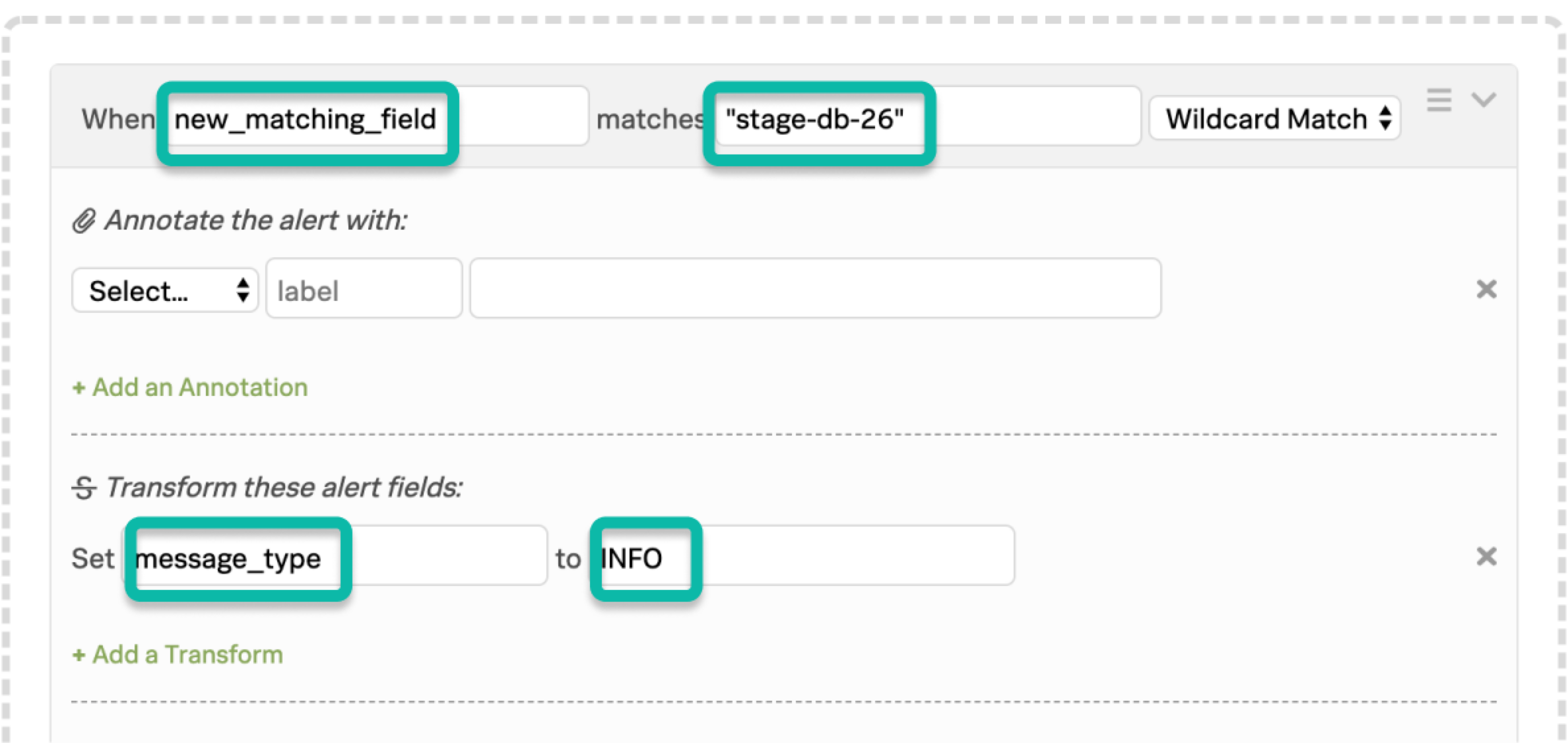
次の例では、entity_id フィールドの disk space と、host_name フィールドの stage-db-26 という名前をキャプチャし、両方の条件が満たされた場合にのみ、これらのアラートを INFO イベントに変換します。
最初のルールのマッチング条件は、最初の希望するフレーズをキャッチし、変数展開を使って2番目のフィールドの値を新しく宣言されたフィールドにインポートします。
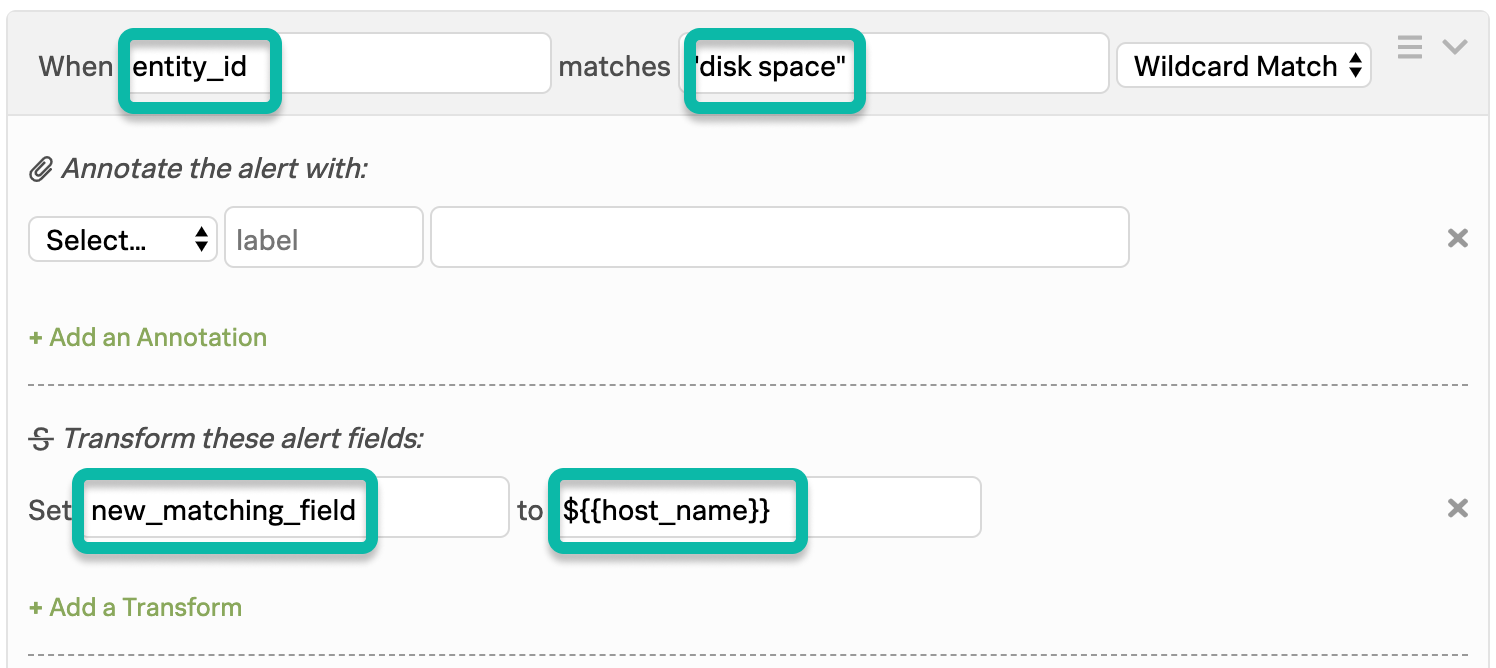
2番目のルールのマッチング条件は、1つ目のルールの下に置かなければならないが、新しく宣言されたフィールドの値 stage-db-26 をチェックし、適切なアクションを取ります。