通知の集約 🔗
通知は、短時間に大量のアラートを受信すると集約され始めます。Splunk On-Callはアラートストームを検出すると自動的にこのプロセスを開始し、ページング出力される通知の数を制限します。すべてのアラートまたは特定のアラートを完全にミュートするには、アラートルールエンジン:変換 を参照してください。
通知集約は、60秒のウィンドウ内に3つの固有のインシデントが開かれた場合にのみトリガーされます。通知集約がトリガーされると、新しいインシデントの通知は、インシデントが開いたときにすぐに送信されるのではなく、1分間隔で送信されます。1つの通知には、各インシデントではなく、ユーザーがページングされているインシデントの数が表示されます。送信される通知の媒体は、ユーザーのパーソナルページングポリシーで指定されている方法に合わせられます。さらに、新しいインシデントが到着せず、トリガーされたアラートが未確認のままである場合、次のページはユーザーのページングポリシーに従います。
通知の集約がトリガーされない場合、複数のインシデントは、ユーザーのパーソナルページングポリシーに概説されているとおりに、従来の方法でページングされます。
通知集約を終了するには、プロセスでいつ開かれたかに関係なく、ユーザーに関連するすべてのインシデントを確認する必要があります。別の言い方をすると、トリガーされた状態において、ユーザーに関連するインシデントがゼロでなければなりません。
以下は、いくつかの異なるシナリオについての説明です。
タイムラインのアクション |
集約 |
期待される応答 |
|---|---|---|
60秒以内にタイムラインに2つのインシデントが作成されます。 |
いいえ |
両方のインシデントについて、オンコールのユーザーに通知を送信します。 |
タイムラインに4つのインシデントが60秒以内に作成されます。 |
はい |
最初の1分間に3回、次の1分間に1回の通知が送られます。 |
タイムラインでは、毎分10件のインシデントが5分間発生します |
はい |
最初の1分間に3回、その後の4分間に1回、通知が送られます。 |
アラート集約 🔗
Splunk On-Callは、インシデントペイロード内のentity_idフィールド値に基づいてアラートを集約します。
次の画像では、タイムラインにインシデント#642とそれに続く4つのアラートが表示されています。インシデントがAck’dまたはCriticalの状態にあり、同じentity_idを持つ複数のアラートがタイムラインに到着し続ける場合、アラートはインシデントの下にロールアップされ、元のアラートに基づいてページアウトされます。
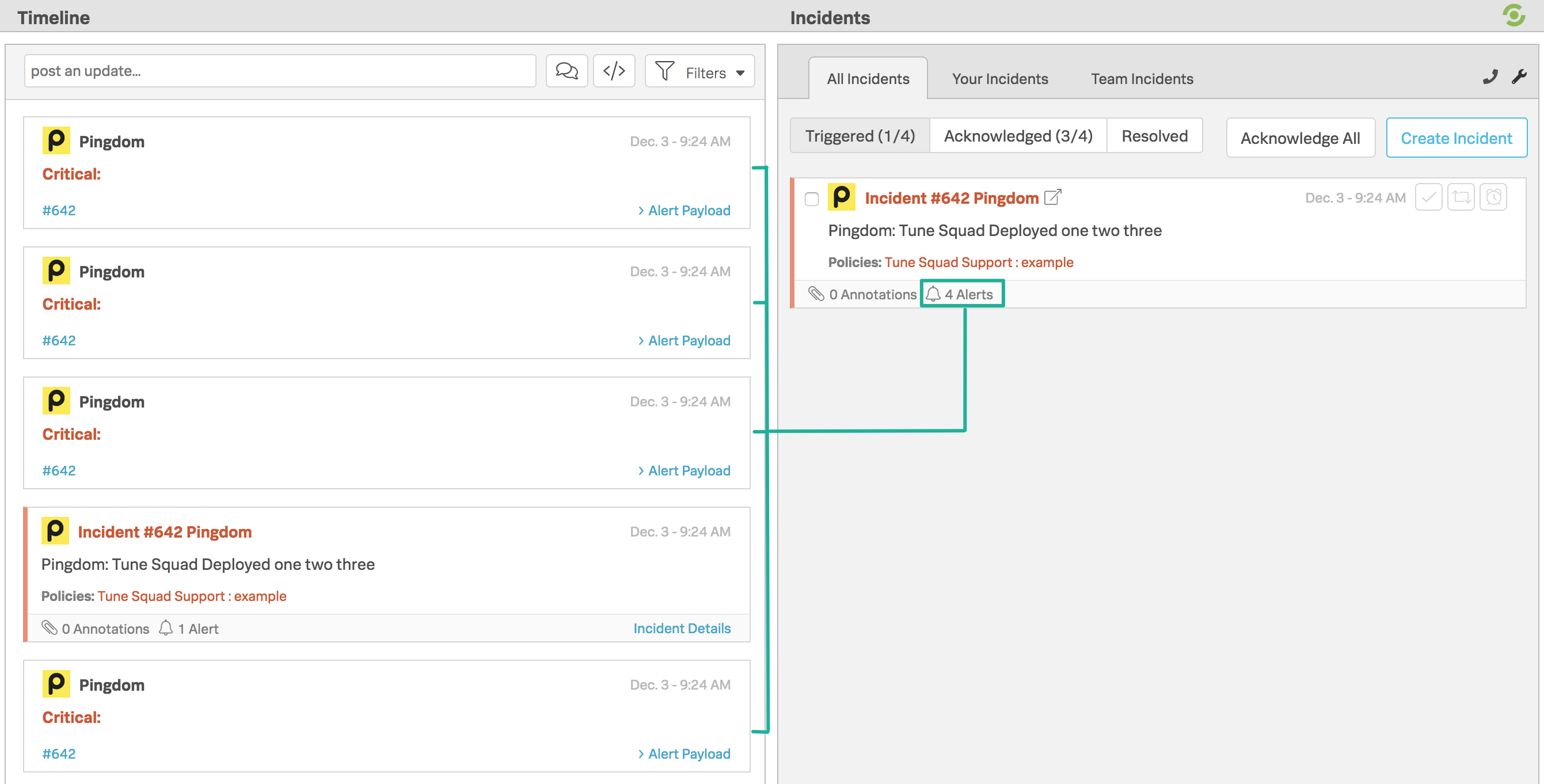
このアラート集約は、entity_idがイベント間で共有されている限り、クリティカル、警告、確認メッセージタイプで機能します。entity_idやmessage_typeなどのフィールドの詳細については、インシデントフィールド 用語集 を参照してください。
注釈
アラートのmessage_type値が警告からクリティカルにステータスが変更されない限り、Warning message_typeの下に集約されるアラートは正常に集約されます。この値がソースからステータスを変更した場合、確認されたインシデントは確認からポップオフし、オンコールユーザーにページングを開始するトリガー状態に戻ります。