Splunk On-CallのCoralogixインテグレーション 🔗
以下の手順でCoralogixをSplunk On-Callと統合できます。
要件 🔗
このインテグレーションは以下のバージョンのSplunk On-Callと互換性があります:
Starter
Growth
エンタープライズ
Splunk On-Callの設定 🔗
Splunk On-Callの以下の手順に従って、インテグレーションを設定します:
メインのタイムラインから、Integrations、3rd Party Integrations、 を選択します。インテグレーションが有効になっていない場合は、Enable Integration を選択します。
URL to notify フィールドの値をクリップボードにコピーします。
#. After you’ve copied the URL, select Settings, Routing Keys to find your routing key configuration.
インテグレーションで使用するルーティングキーを決定し、それが正しいエスカレーションポリシーに関連付けられていることを確認します。ルーティングキーの詳細や新規作成方法については、Splunk On-Callでルーティングキーを作成する を参照してください。
Coralogixの設定 🔗
Coralogixの以下の手順に従って、インテグレーションをセットアップしてください。
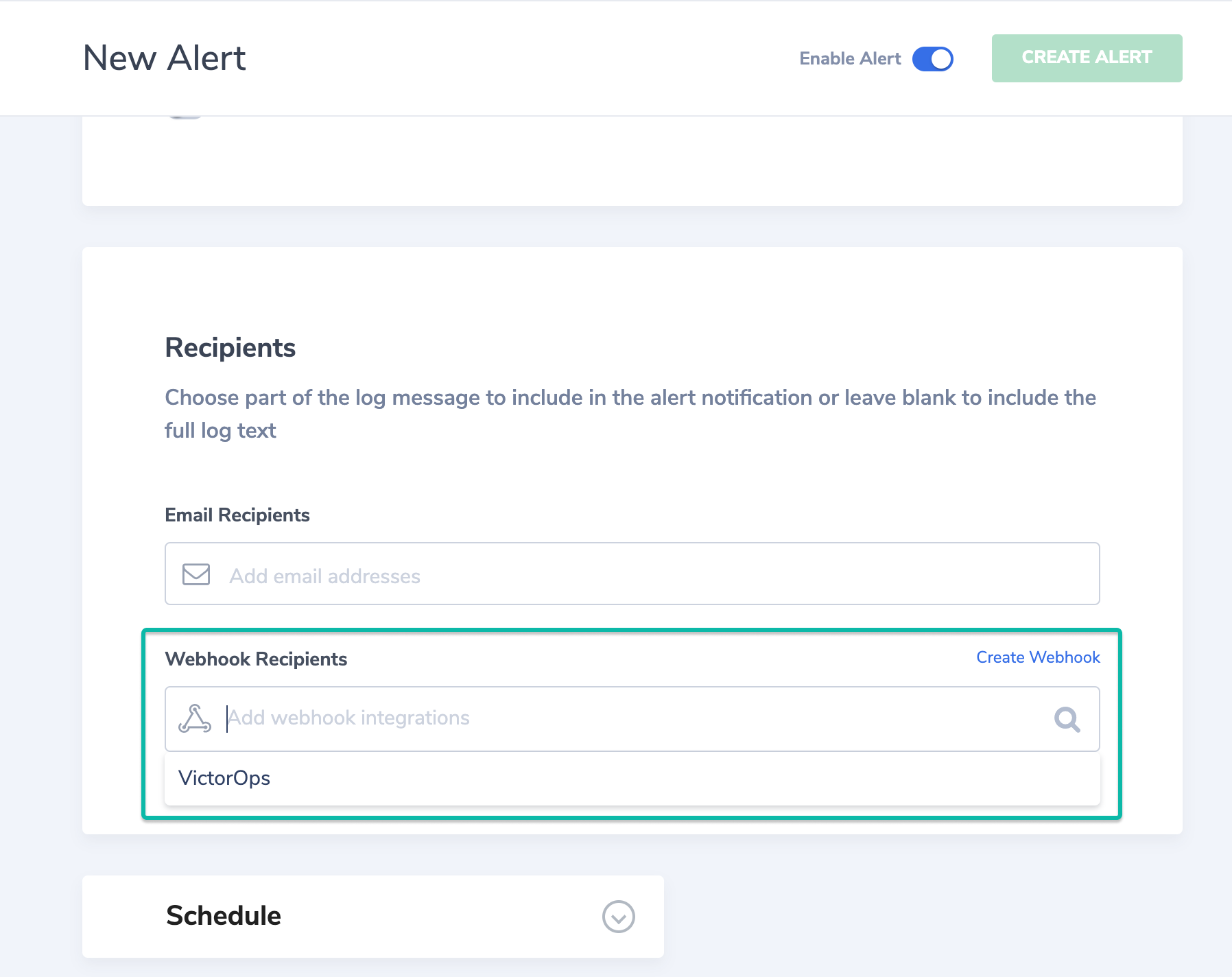
Webhookを作成する 🔗
メインダッシュボードから、右上隅のユーザー名のマークを選択し、Settings を選択します。
Webhooks に移動し、画面右側の青い + ボタンを選択します。
Webhookのエイリアスを指定し、タイプを`Slack`から`WebHook`に変更します。
Splunk On-CallからコピーしたURLを貼り付けます。
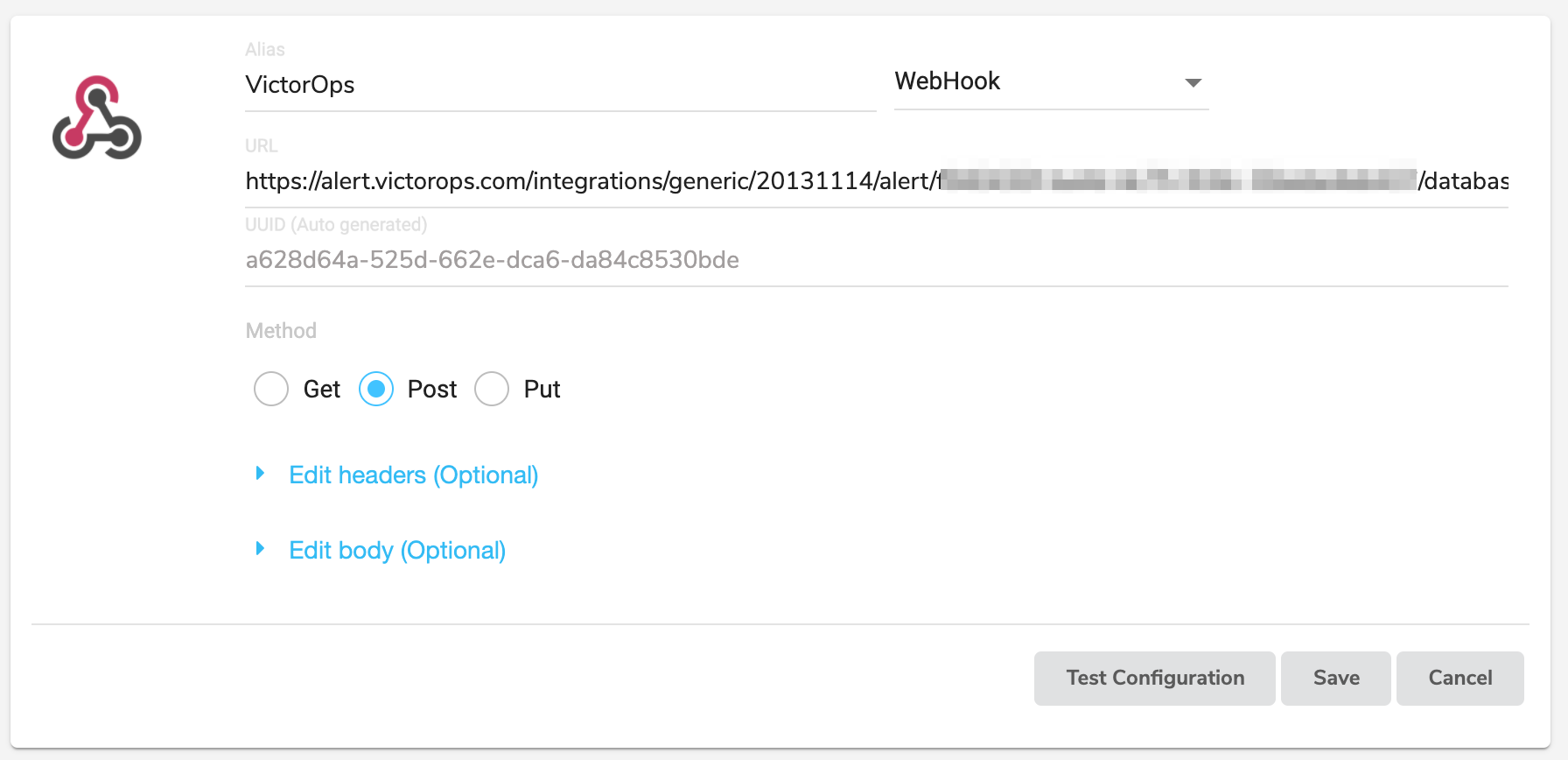
Edit body に以下のペイロードを貼り付けます:
{ "message_type": "CRITICAL", "entity_id": "$ALERT_ID", "entity_display_name": "$ALERT_NAME", "alert_severity": "$EVENT_SEVERITY", "state_message": "$LOG_TEXT", "description": "$ALERT_DESCRIPTION", "alert_action": "$ALERT_ACTION", "alert_url": "$ALERT_URL", "log_url": "$LOG_URL", "monitoring_tool": "Coralogix", "team": "$TEAM_NAME", "application": "$APPLICATION_NAME", "subsystem": "$SUBSYSTEM_NAME", "ipAddress": "$IP_ADDRESS", "timestamp": "$EVENT_TIMESTAMP", "hitCount": "$HIT_COUNT" }
message_typeの値は、アラートのタイプを識別するのに役立ちます。有効な値は以下の通りです:CRITICALWARNINGACKNOWLEDGEMENTINFORECOVERY
希望するクリティカリティのアラートを適切にSplunk On-Callに送信するためには、Coralogixの異なるアラートに関連付けられた複数のWebhookを作成する必要があるかもしれません。デフォルトのペイロードに従った場合、CoralogixのALERT_IDフィールドから引き出される entity_id の値が、さまざまなクリティカリティのアラートで一貫していることを確認してください。
カスタムアラートWebhookの詳細については、Coralogixの公式ドキュメントをご覧ください。
Webhookをテストする 🔗
Webhookのペイロードを入力した後、Coralogixで設定をテストしてください。
アラートをWebhookに割り当てる 🔗
Splunk On-Callを指すWebhookを作成したら、それをCoralogix Alertに割り当て、Webhookが適切なイベントでトリガーされるようにします:
Coralogixで、Alerts に移動し、既存のアラートを選択するか、New Alert を選択します。
目的のアラート設定を適用し、recipients セクションまでスクロールダウンします。
以前に作成したSplunk On-Call webhookを選択します。
アラートを保存します。