Splunk On-CallのZendeskインテグレーション 🔗
Splunk On-CallのZendeskインテグレーションを使用すると、Splunk On-Callでインシデントを自動的にトリガー、確認、解決できます。また、このインテグレーションを使用してSplunk On-Call側でインシデントを承認して、Zendeskでステータス変更をトリガーすることもできます。
要件 🔗
Zendeskインテグレーションは、Splunk On-Callのエンタープライズバージョンと互換性があります。
このオプションの「応答を確認」ステップは、アウトバウンドWebhookを利用します。
Splunk On-CallでZendeskインテグレーションを有効にする 🔗
ルーティングキーを使用するようにエンドポイントURLをカスタマイズする 🔗
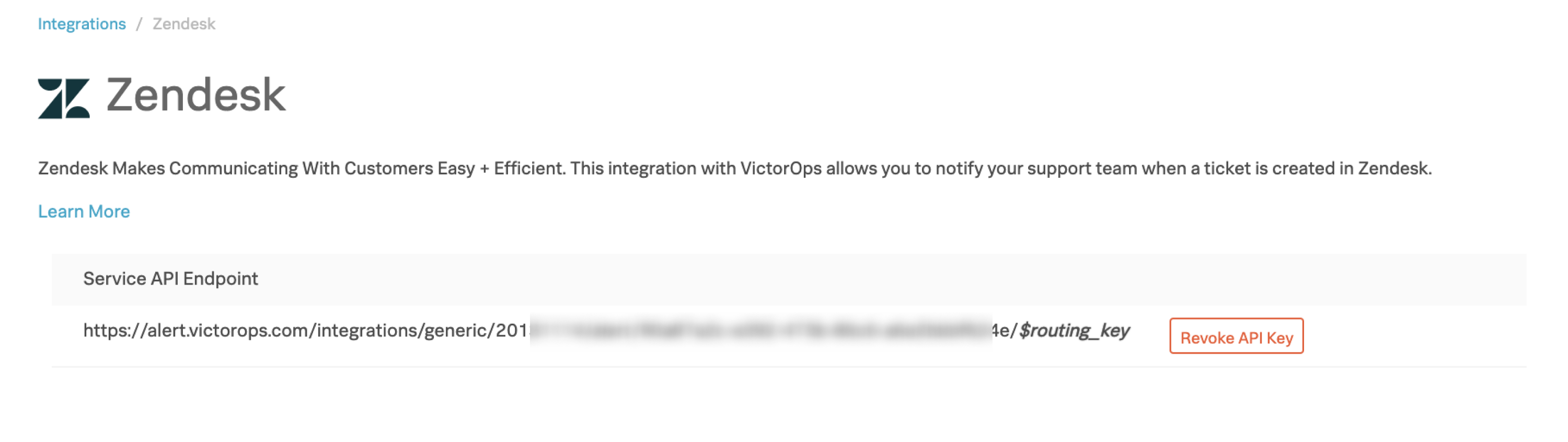
サービスAPIエンドポイントURLをカスタマイズして、Zendeskインテグレーション用のルーティングキーを使用します。そのためには、$routing_key をルーティングキーに置き換えます。たとえば、routing_keyの値が」database」の場合: .....36437/$routing_key` becomes ``......36437/database
ルーティングキーは、Splunk On-Callの Settings、Routing Keys の順に移動して設定できます。ルーティングキーの詳細とベストプラクティスについては、以下を参照してください。Splunk On-Callでルーティングキーを作成する
Zendeskでターゲットを作成する 🔗
Zendeskポータルから、サイドメニューの Settings を選択します。
Settings セクションで、Extensions. を選択します
表示されるメニューで、add a target を選択します。
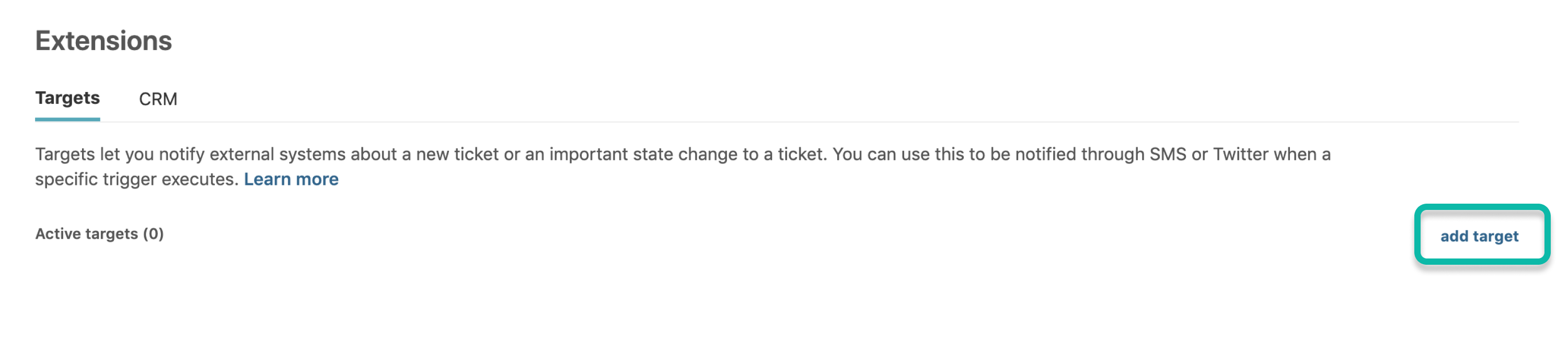
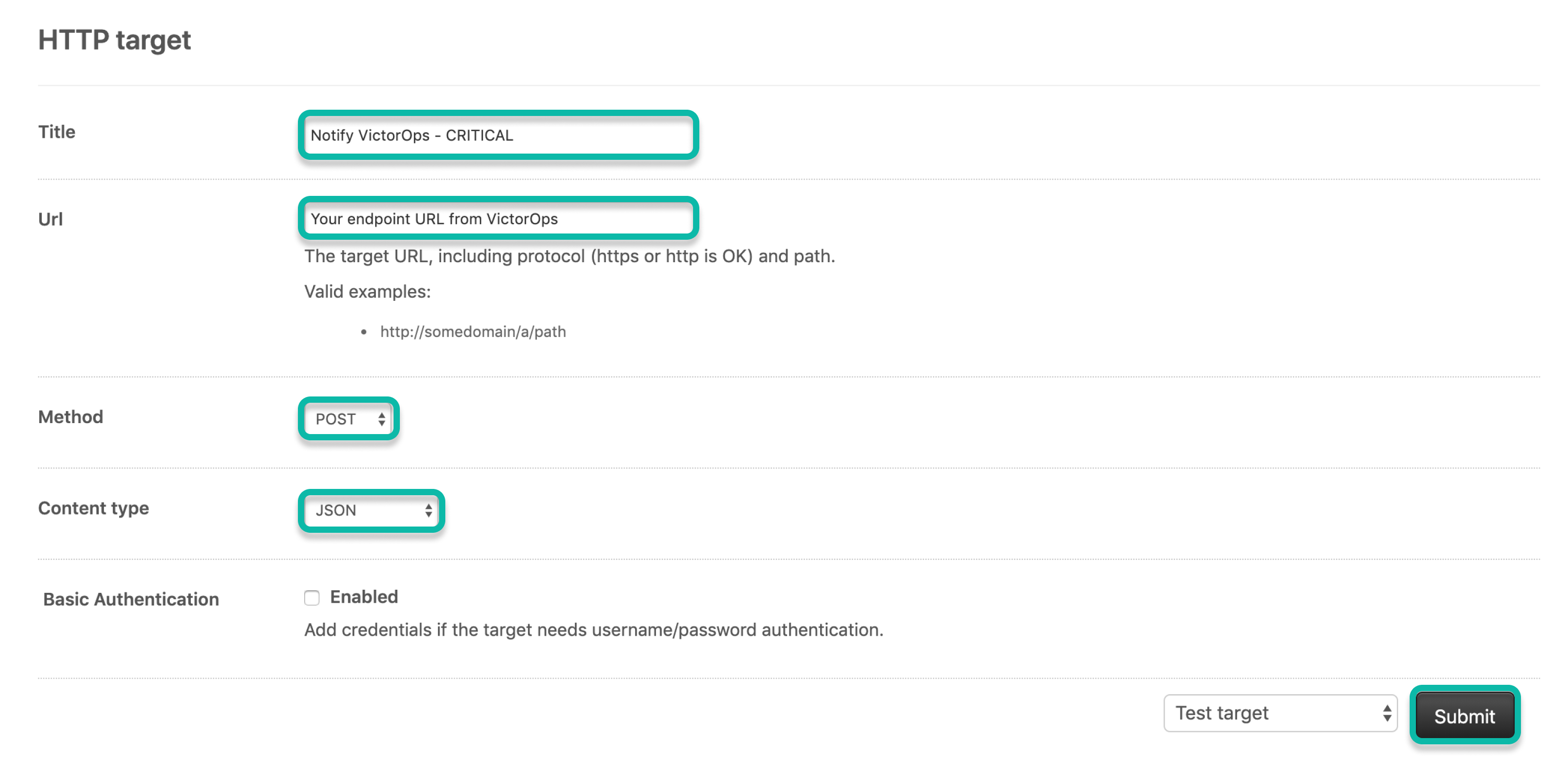
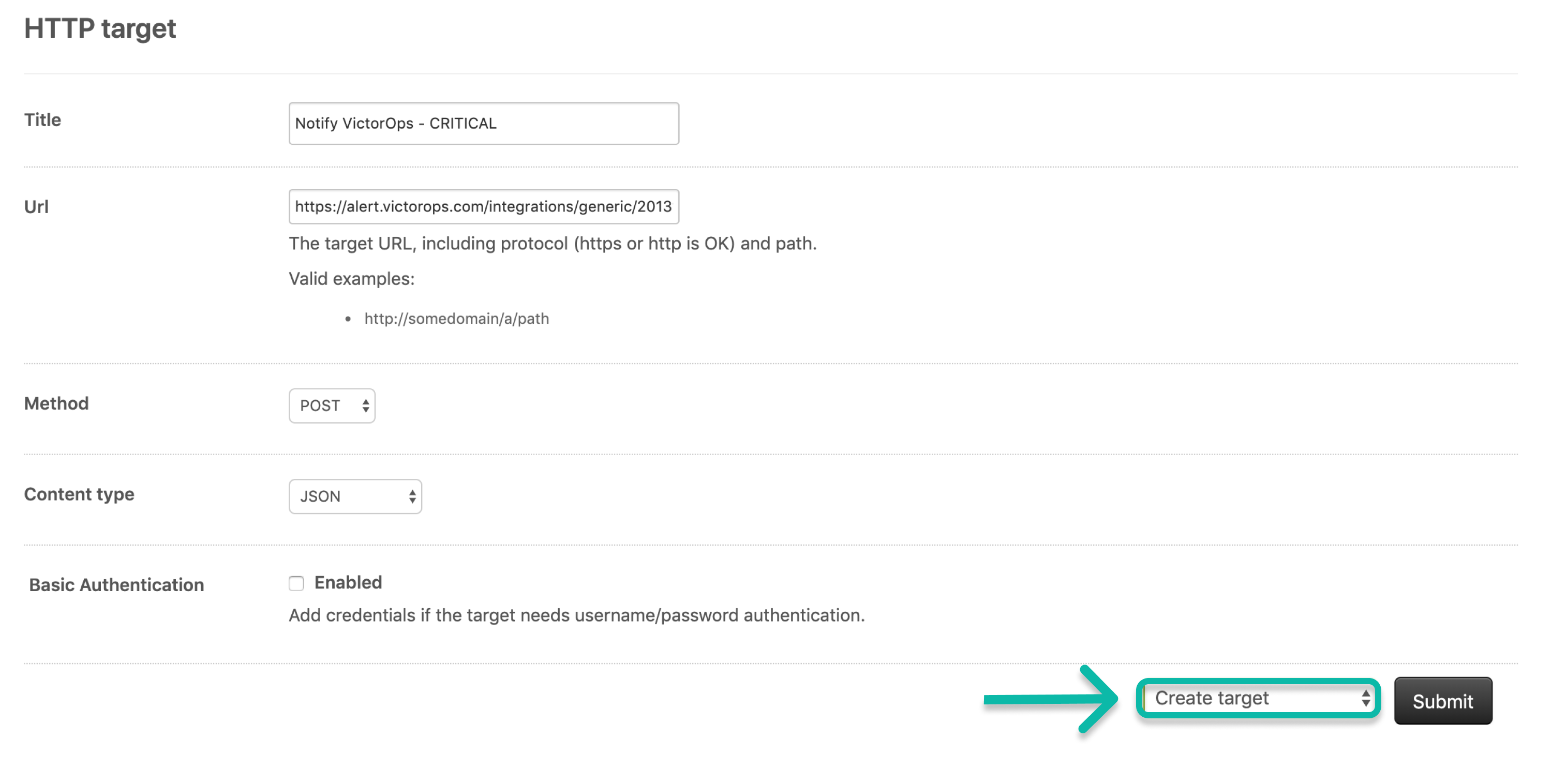
HTTP Target オプションを選択します。

HTTPターゲットに名前を付けます。
Splunk On-CallからコピーしたエンドポイントURLと有効なルーティングキーを貼り付けます。
Method で POST を選択します。
Content type で JSON を選択します。
Basic Authentication は未選択のままにしておきます。
Test target オプションを選択します。
Submit を選択します。
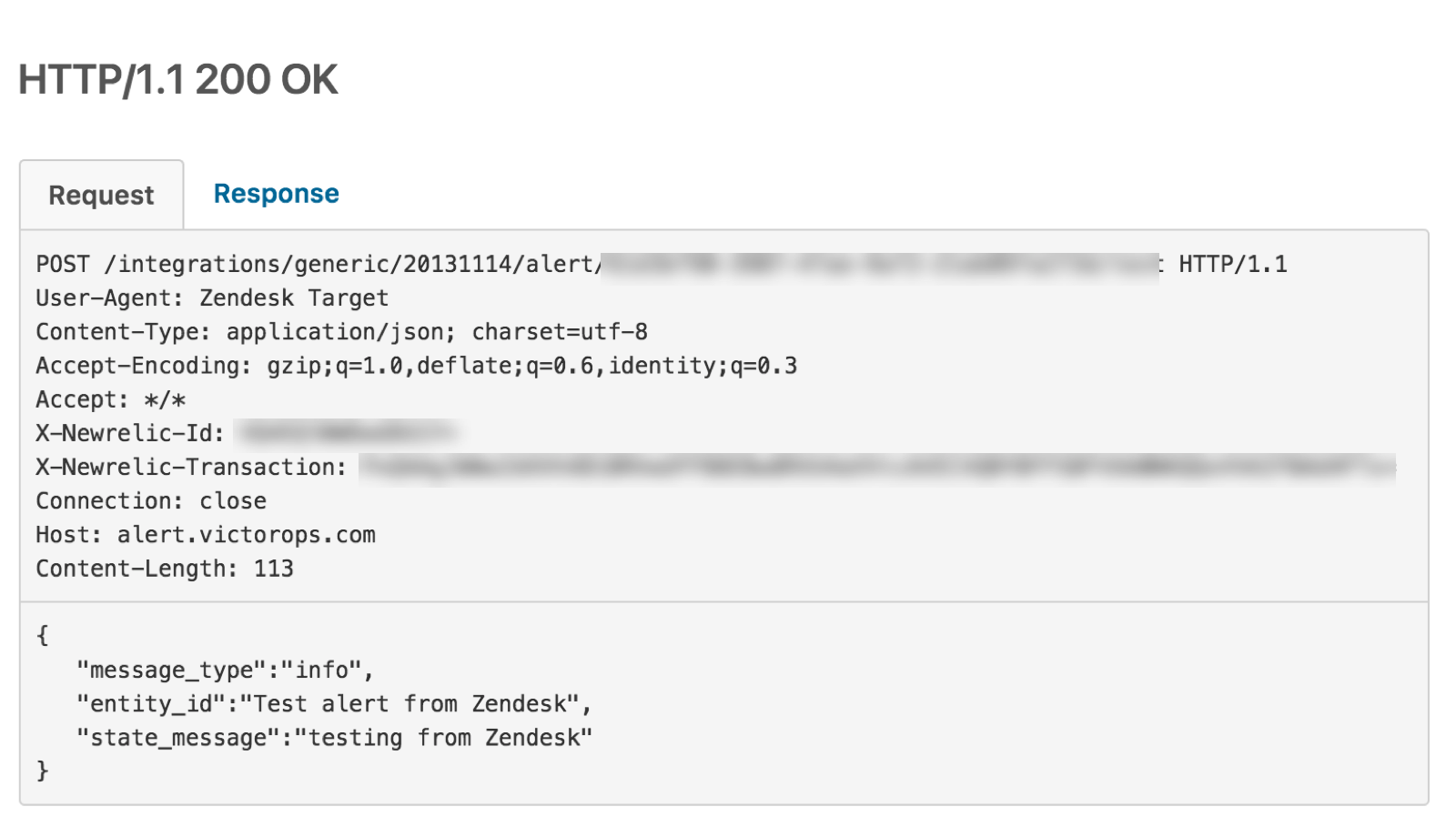
以下のJSON本文をコピー&ペーストします。
Submit を選択します。
{ "message_type":"info", "entity_id":"Test alert from Zendesk", "state_message":"testing from Zendesk" }
インテグレーションが正しく設定されていれば、このような200の成功レスポンスが表示されます。
15. Check your Splunk On-Call timeline for a new event. This is an INFO message which, doesn’t create a new incident in Splunk On-Call. It is intended only to confirm that Zendesk can successfully send events to Splunk On-Call.
成功メッセージを終了します。
オプションを Create target に変更し、Submit を選択します。
ZendeskからSplunk On-Callへのアラートを設定する 🔗
Zendeskのサイドメニューから、Business Rules のセクションを探し、Triggers を選択します。
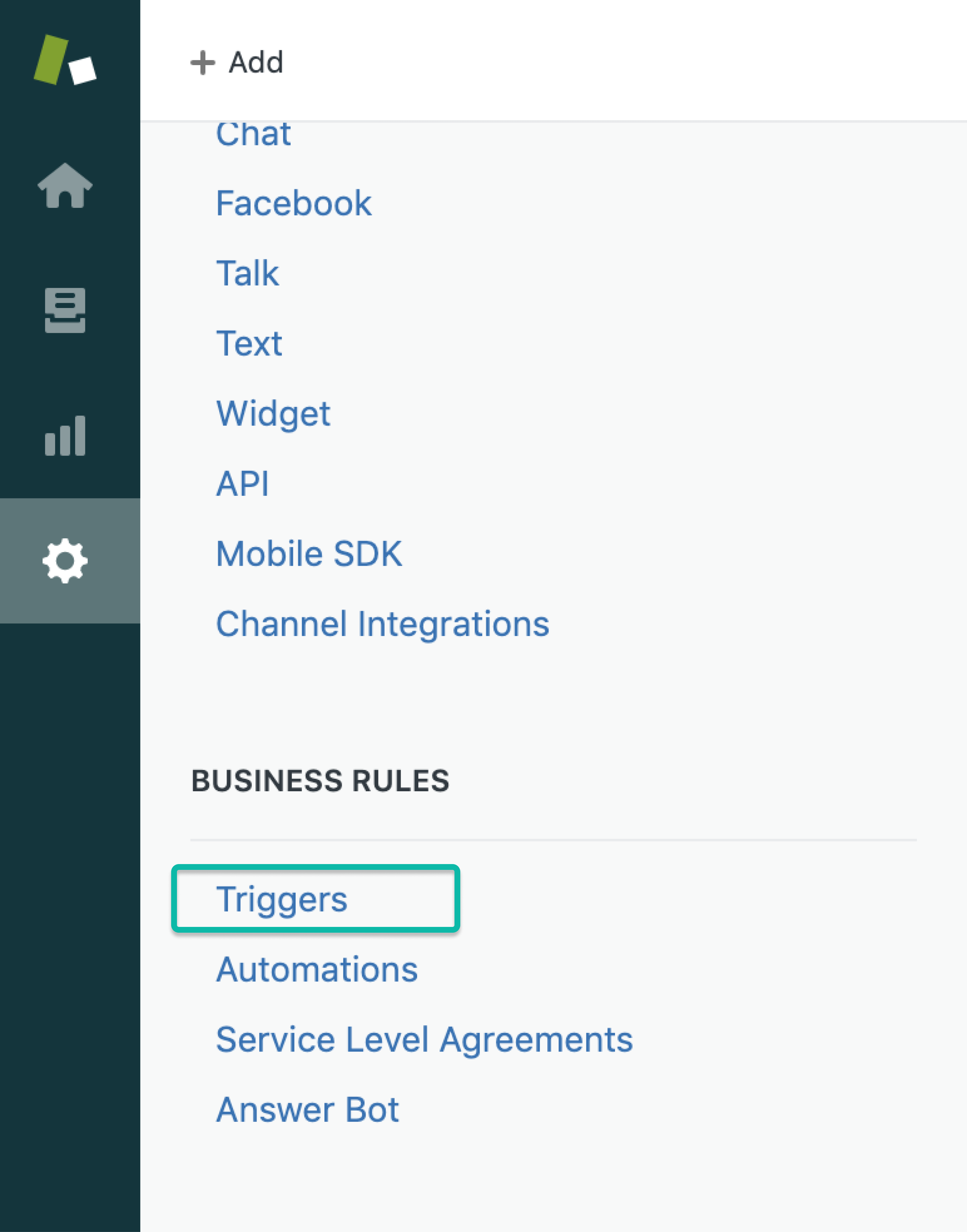
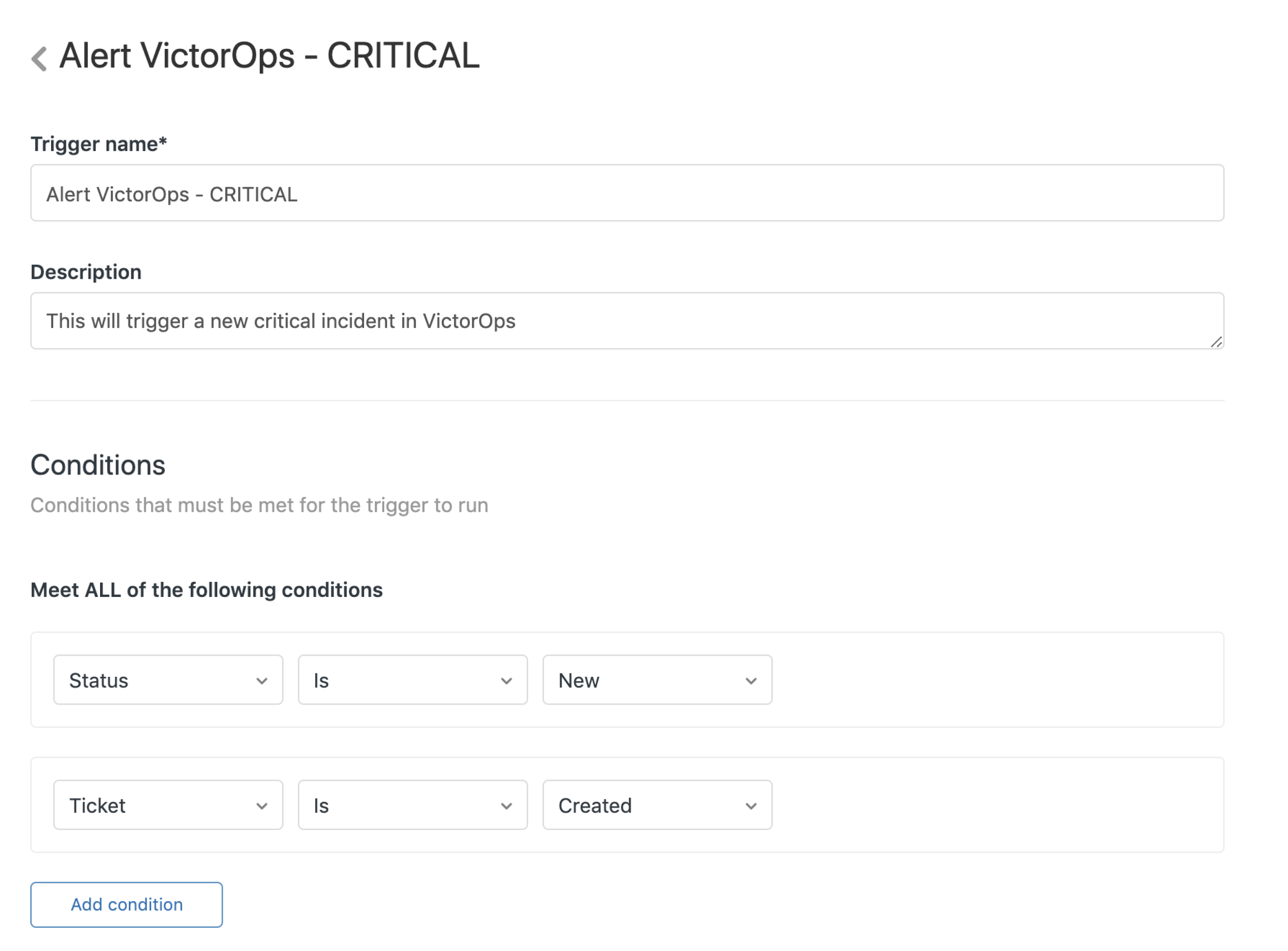
Triggers メニューから、Add trigger を選択します。
名前と説明を入力します。Add condition を選択し、以下の2つの条件を追加します。この2つの条件は、Zendeskの新しいケースごとにSplunk On-Callインシデントを作成します。これらの条件を変更することで、Splunk On-Callを警告する条件をさらに絞り込み、特定のワークフローに適合させることができます。
条件:
ステータスは新規である
チケットが作成されている
Actions セクションの下で、Add Action を選択します。最初のドロップダウンメニューで、Notifications セクションまでスクロールし、Notify target を選択します。2番目のドロップダウンメニューで、先ほど作成したSplunk On-Callターゲットを選択します。
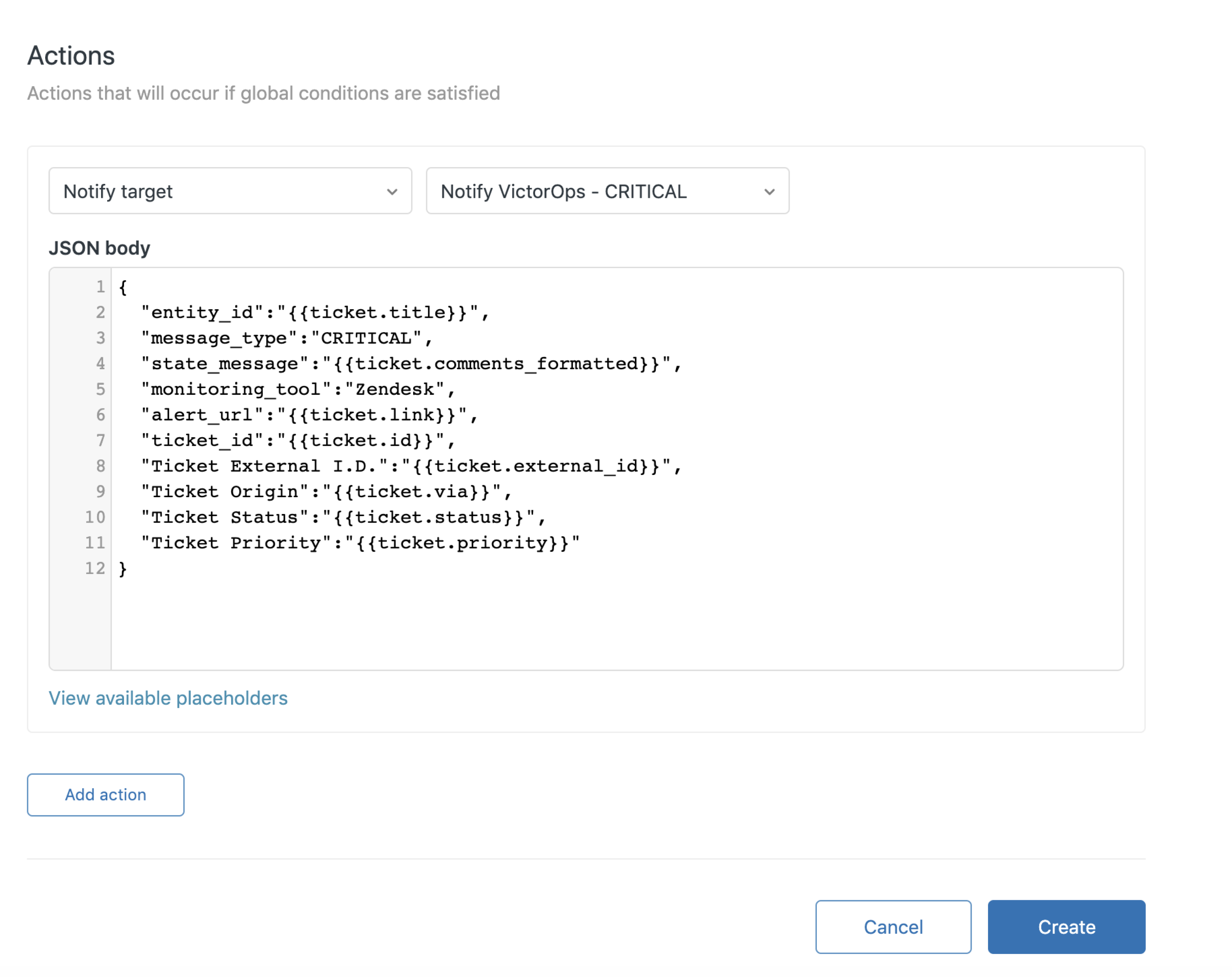
以下のJSONペイロードをコピーし、JSON body フィールドに貼り付け、Create を選択します。
クリティカルアラート 🔗
このトリガーはSplunk On-Callで新しいインシデントを開きます。
{
"entity_id":"{{ticket.id}}",
"message_type":"CRITICAL",
"state_message":"{{ticket.comments_formatted}}",
"monitoring_tool":"Zendesk",
"alert_url":"{{ticket.link}}",
"ticket_id":"{{ticket.id}}",
"Ticket External I.D.":"{{ticket.external_id}}",
"Ticket Origin":"{{ticket.via}}",
"Ticket Status":"{{ticket.status}}",
"Ticket Priority":"{{ticket.priority}}"
}
このプロセスを複製して、Zendeskでケースが割り当てられたり閉じられたりしたときに、Splunk On-Callに承認とリカバリイベントのアラートを送信するトリガーをさらに2つ作成する必要があります。それぞれの新しいトリガーには、先ほど作成した同じターゲットを再利用します。トリガーの条件は、必要に応じて変更できます。
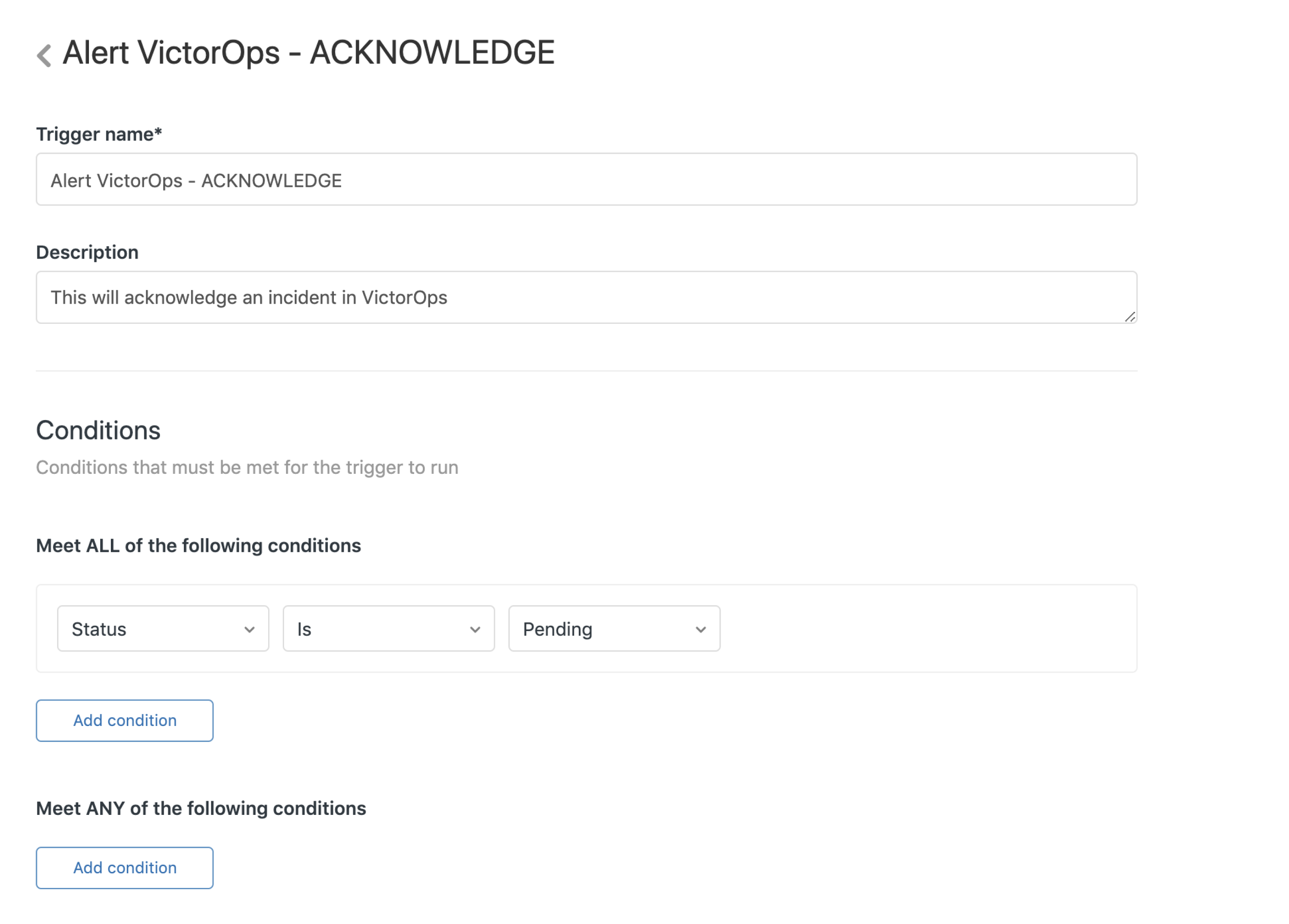
承認アラート 🔗
このトリガーは、Splunk On-Callに承認アラートを送信し、インシデントを承認してページングとエスカレーションを停止します。
条件:ステータスは保留中
JSONペイロード:
{
"entity_id":"{{ticket.id}}",
"message_type":"ACKNOWLEDGEMENT",
"state_message":"{{ticket.comments_formatted}}",
"monitoring_tool":"Zendesk",
"alert_url":"{{ticket.link}}",
"ticket_id":"{{ticket.id}}",
"Ticket External I.D.":"{{ticket.external_id}}",
"Ticket Origin":"{{ticket.via}}",
"Ticket Status":"{{ticket.status}}",
"Ticket Priority":"{{ticket.priority}}"
}
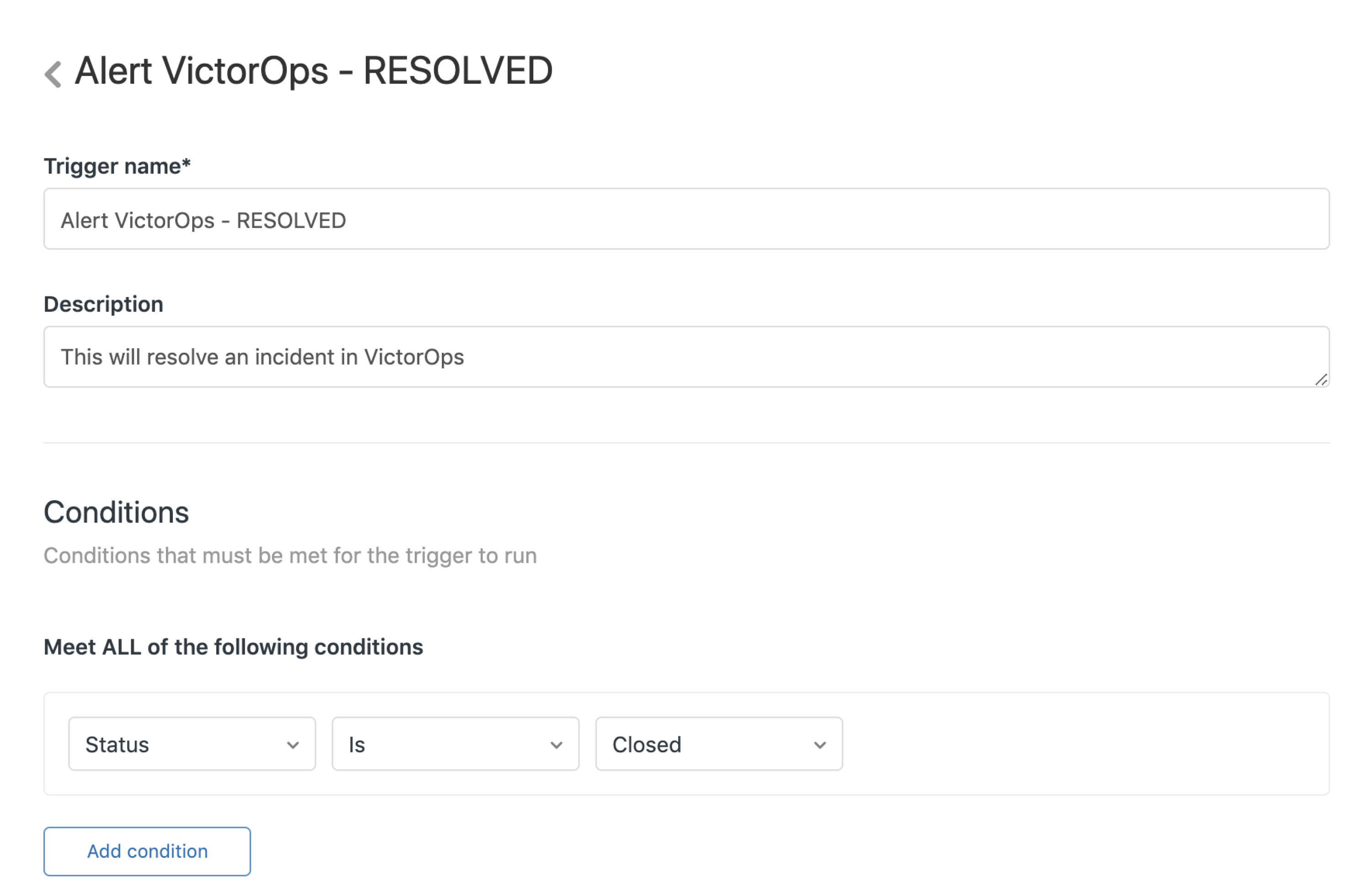
解決済みのアラート 🔗
このトリガーは、Splunk On-Callにリカバリ通知を送信し、インシデントを終了させます。
条件:ステータスはクローズ済み
JSONペイロード:
{
"entity_id":"{{ticket.id}}",
"message_type":"RECOVERY",
"state_message":"{{ticket.comments_formatted}}",
"monitoring_tool":"Zendesk",
"alert_url":"{{ticket.link}}",
"ticket_id":"{{ticket.id}}",
"Ticket External I.D.":"{{ticket.external_id}}",
"Ticket Origin":"{{ticket.via}}",
"Ticket Status":"{{ticket.status}}",
"Ticket Priority":"{{ticket.priority}}"
}
(オプション)発信Webhookを使用して、応答を確認する 🔗
Splunk On-Call Custom Outgoing Webhooksを使用すると、Splunk On-CallでZendeskインシデントが承認されたときに関連するZendeskケースが指定したステータスに自動的に遷移します。
宛先URLを作成する 🔗
まず、Zendeskアカウントの適切な送信先URLを作成する必要があります。URLの一部はURLエンコードされていないと正しく機能しないため、URL 構造に正確に従うようにしてください。
以下の例では、以下を想定しています:
Zendeskのサブドメインはbuttercupgames.zendesk.comです。
Zendeskユーザーのメールアドレスはalex@buttercupgames.comです。
Zendeskが生成したAPI トークンはabc123efg456hij789です
URLの構造は以下の通りです:
https://<email-address>/token:<yourAPI-token>@<your-subdomain>.zendesk.com/api/v2/tickets/${{ALERT.ticket_id}}.json
例のデータを考えると、最終的なURLは以下のようになります:
https:/alex%40buttercupgames.com%2Ftoken:abc123efg456hij789@company.zendesk.com/api/v2/tickets/${{ALERT.ticket_id}}.json
以下は、エンコーディングの重要な要素の要約です:
メールアドレスの@マークは、
%40としてエンコードされます。単語トークンの前のスラッシュは
%2Fとしてエンコードされます。サブドメインの前の@マークがエンコードされていません。
${{ALERT.ticket_id}}は一切変更されません。この構文は、WebhookがトリガーされたときにZendeskチケットIDをURLに動的に挿入するために必要です。
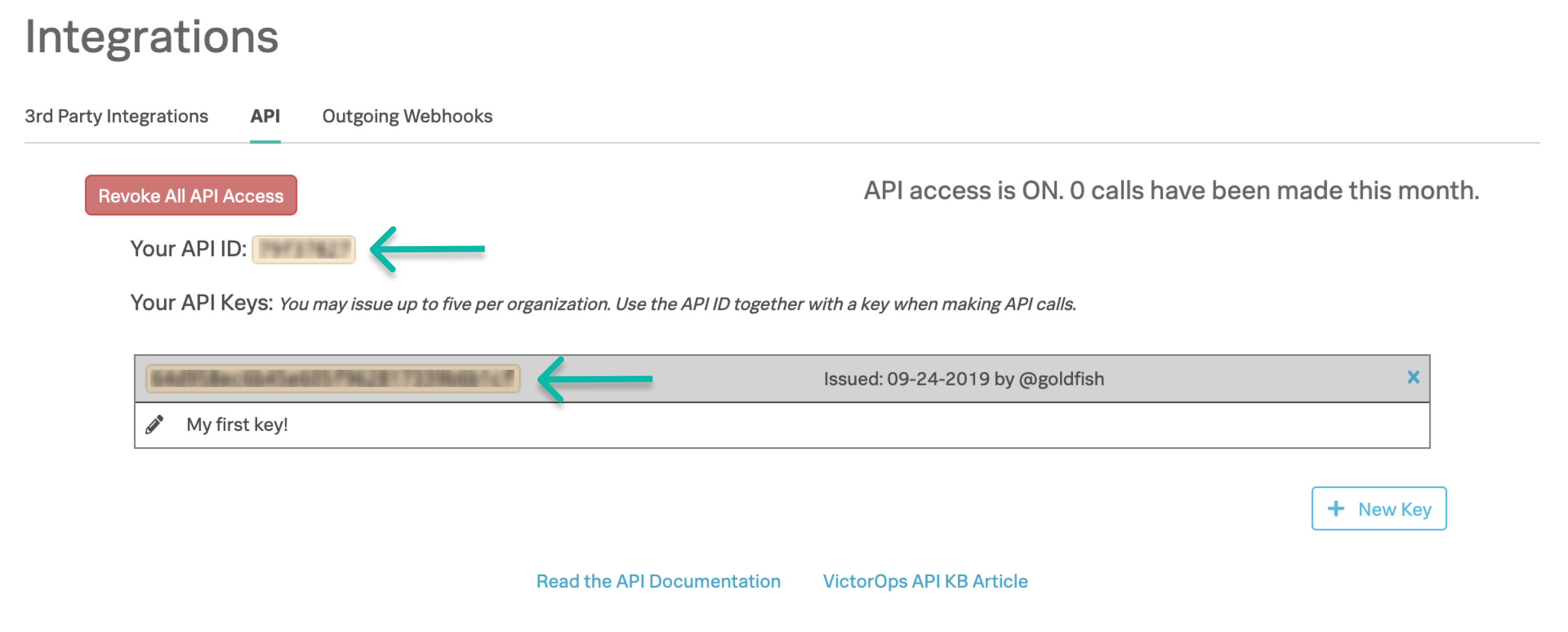
Zendesk APIトークンを生成する 🔗
発信Webhookをセットアップする 🔗
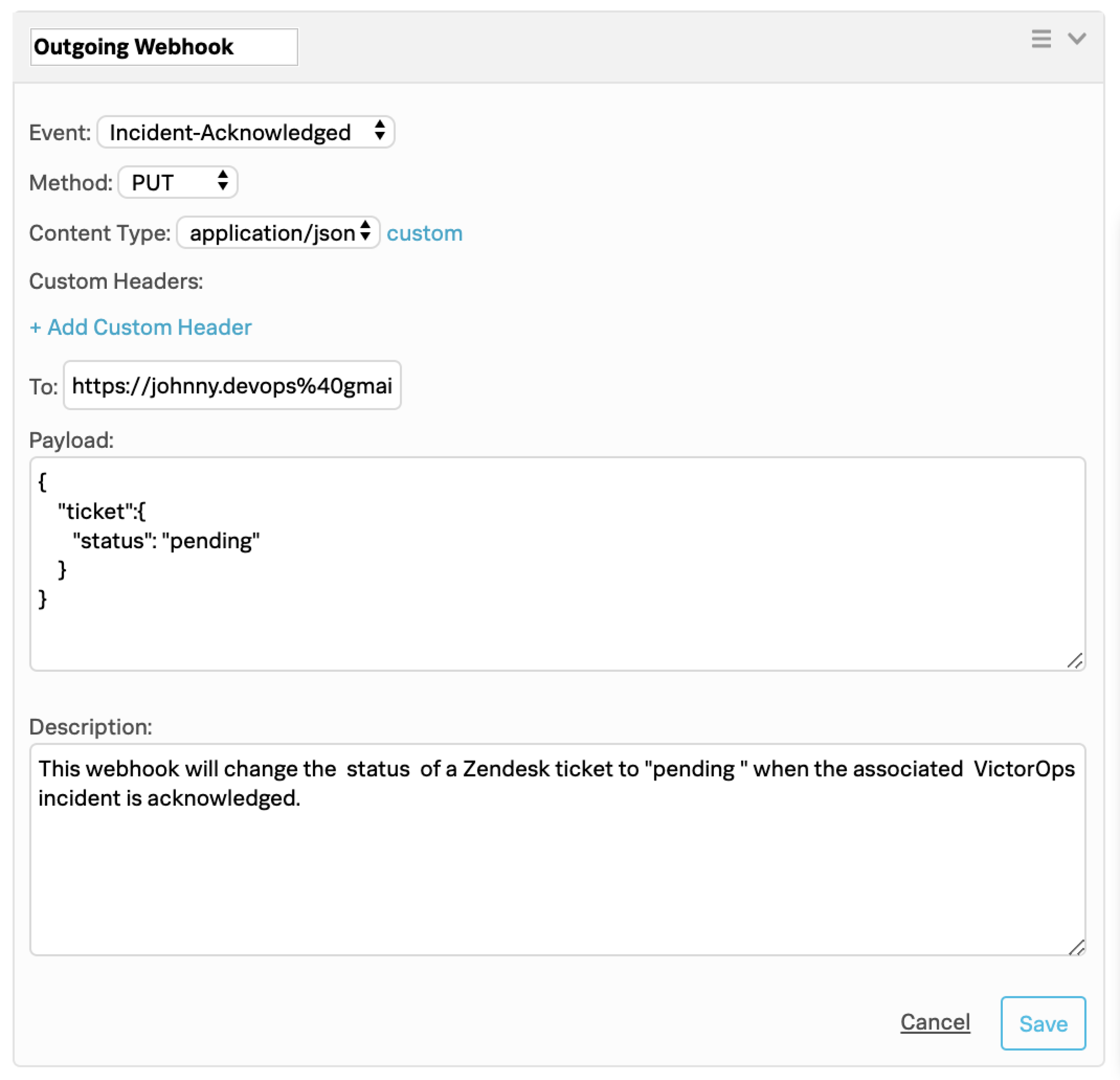
Splunk On-Callで、Integrations、Outgoing Webhooks の順に選択します。
「発信Webhook」で、Add Webhook を選択します。
Event の場合は、Incident-Acknowledged を選択します。
Method の場合は、PUT を選択します。
Content Type の場合は、application/json を選択します。
To フィールドに、前述した宛先URLの全文を貼り付けます。
Payload フィールドに、以下のペイロードを貼り付けます。ステータスの値はお好みのステータスに変更できます。
{ "ticket":{ "status": "pending" } }
Webhookの説明を入力し、Save を選択します。