Splunk On-CallのWavefrontインテグレーション 🔗
Wavefrontはクラウドホスティングサービスであり、CollectD、StatsD、JMX、Rubyのロガー、AWSなど、時系列(メトリック)データを送ることができます。そして、それらの時系列データに対して任意の数の数学演算を実行し、異常値やKPIダッシュボードを見るためのチャートをレンダリングし、最終的にはスタック全体をプロアクティブに監視するための真にインテリジェントなアラートを作成することができます。以下のガイドでは、このインテグレーションについて説明します。
In VictorOps
VictorOps Webポータルから、設定、アラート動作、インテグレーション の順に選択します。
Wavefront インテグレーションオプションを選択します。
インテグレーションを有効にする をクリックします。
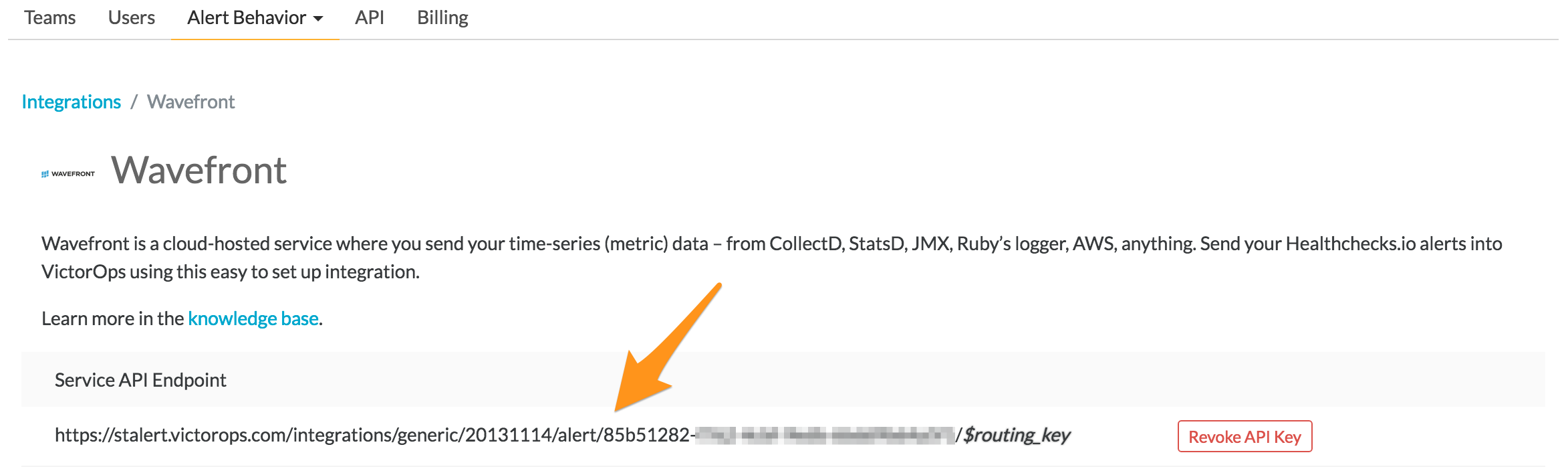
サービスAPIエンドポイント をクリップボードにコピーします。必ず、」$routing_key」セクションを、使用する実際のルーティングキーに置き換えてください。(VictorOpsでルートキーを表示または設定するには、アラート動作、次に ルートキー をクリックします)
In Wavefront 🔗
Wavefront Webインターフェイスにログインし、Browse、Alert Targets の順に選択します。
アラートターゲットを作成する をクリックします。
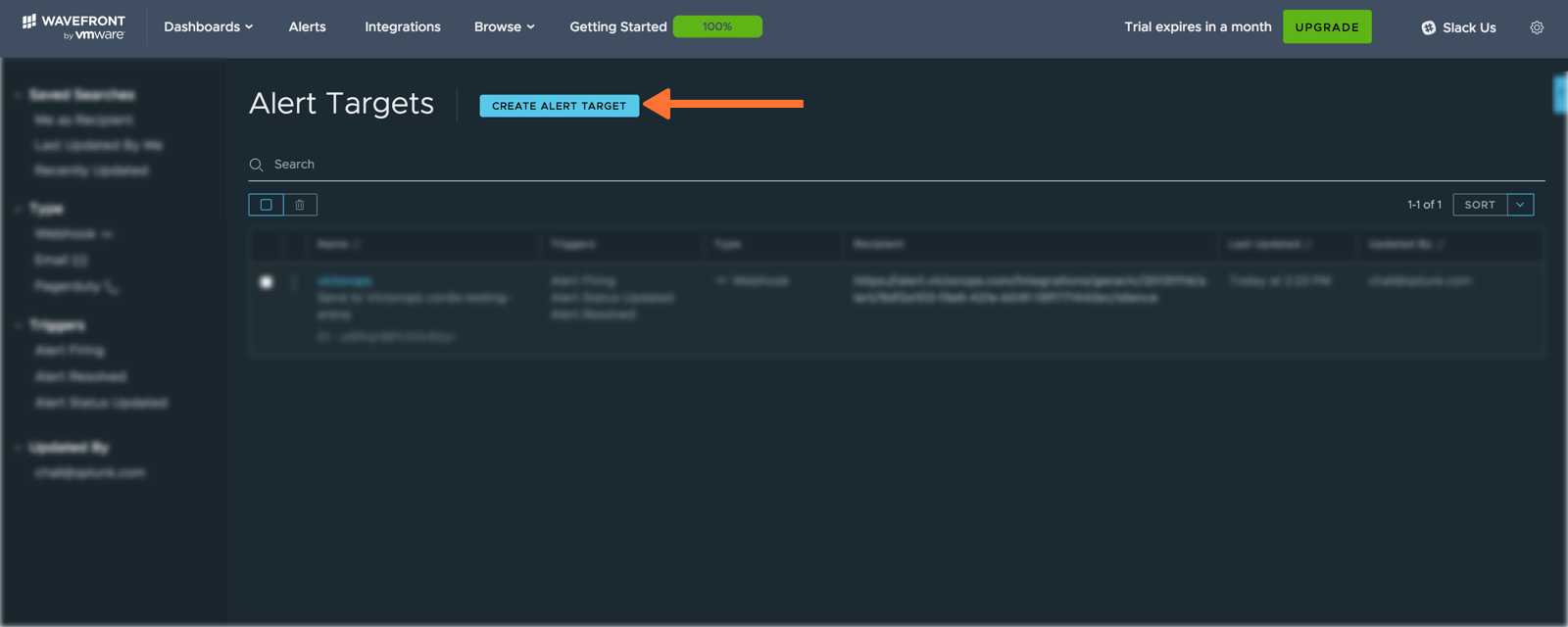
「名前」フィールドにWebhookの名前を短い説明とともに入力します。」Triggers」セクションで Alert Opened、Alert Status Updated、Alert Resolved を選択します。「URL」フィールドに、前の」In VictorOps 「セクションの」通知するURL」を貼り付けます。「Content Type」ドロップダウンメニューから application/json を選択します。最後に」Alert Target POST Body Template」から VictorOps を選択します。保存 をクリックします。
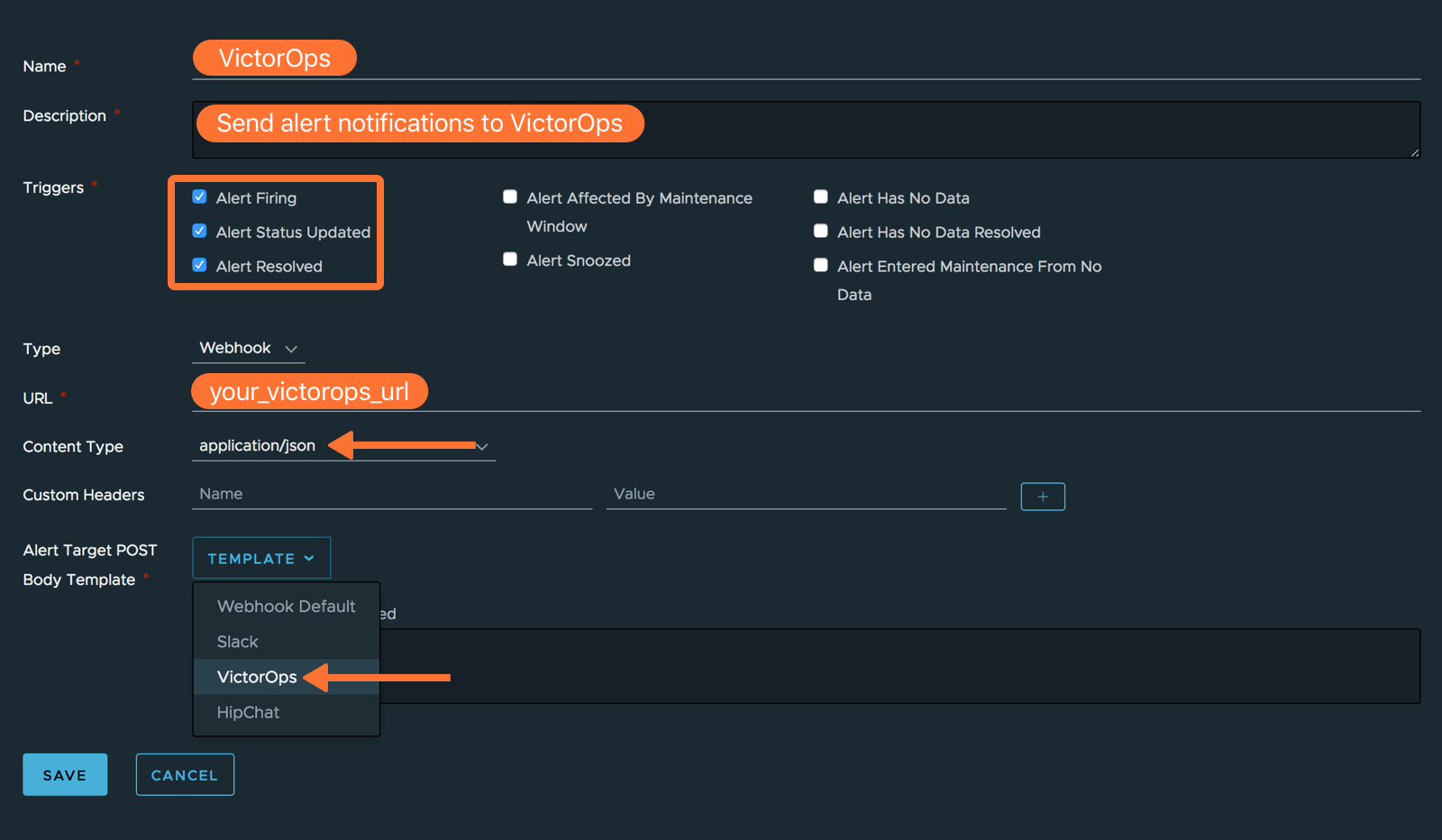
便宜上、テンプレートも以下に貼り付けておきます:
{ "message_type": "{{#endedTime}}recovery{{/endedTime}}{{^endedTime}}{{#severitySmoke}}info{{/severitySmoke}}{{#severityInfo}}info{{/severityInfo}}{{#severityWarning}}warning{{/severityWarning}}{{#severitySevere}}critical{{/severitySevere}}{{/endedTime}}", "entity_id": "{{#trimTrailingComma}}{{^endedTime}}{{#failingHosts}}{{{.}}},{{/failingHosts}}{{/endedTime}}{{#endedTime}}{{#recoveredHosts}}{{{.}}},{{/recoveredHosts}}{{/endedTime}}{{/trimTrailingComma}}", "state_message": "{{{name}}}\n{{{url}}}\n{{#jsonEscape}}{{{additionalInformation}}}{{/jsonEscape}}", "monitoring_tool": "Wavefront", "entity_display_name": "{{#jsonEscape}}{{{hostsFailingMessage}}}{{/jsonEscape}}" }
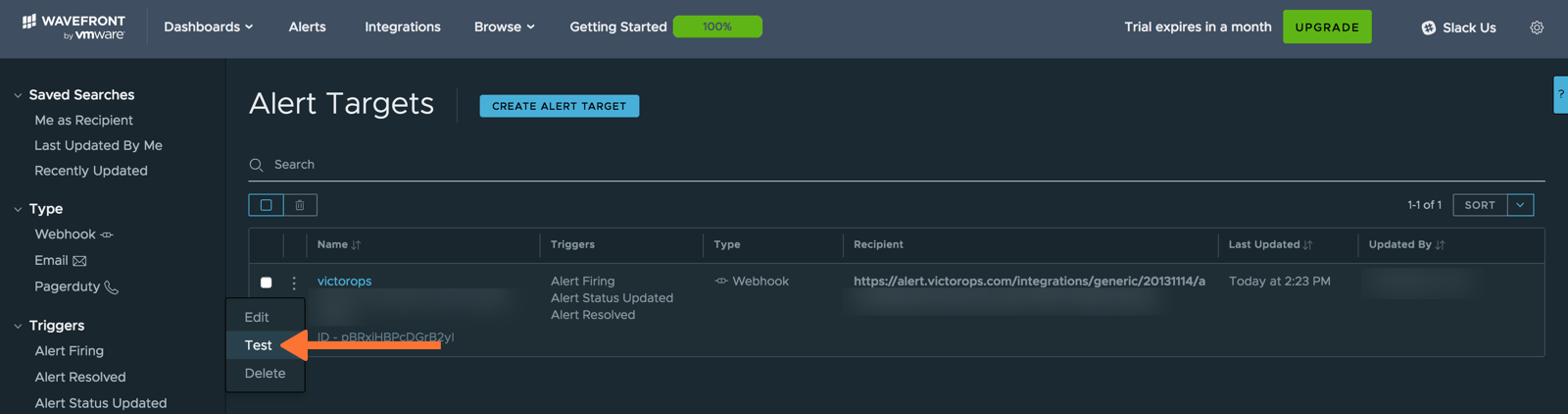
VictorOps Alert Targetが表示されます。左側のドロップダウンメニューをクリックし、Test を選択します。
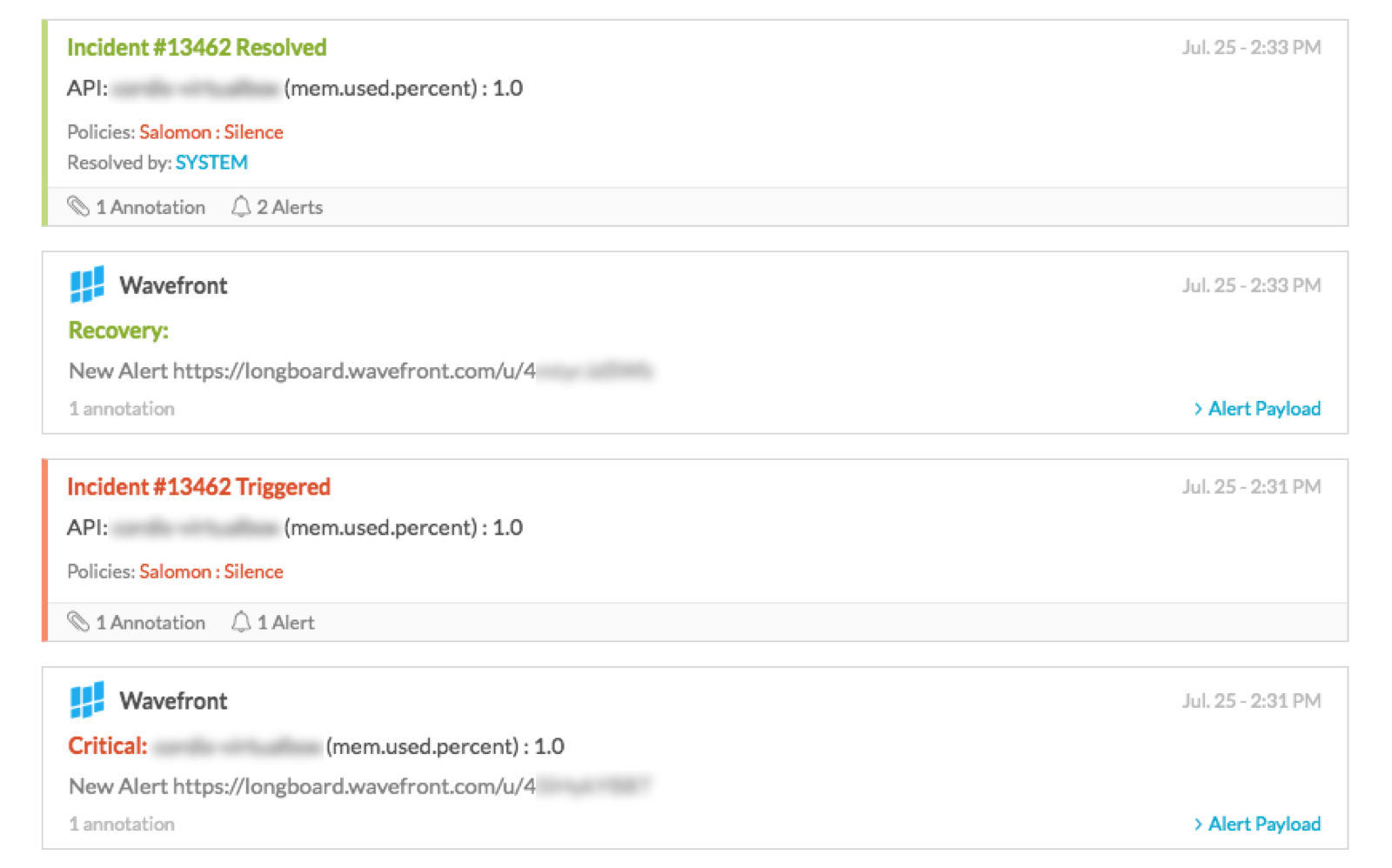
VictorOpsで通知を確認します。
最後に、アラートターゲットを実際のアラートにアタッチします。アラートを作成する場合も編集する場合も、以下の例を参考にVictorOpsをアラートに接続してください。まず、アラートを編集(または作成)します。
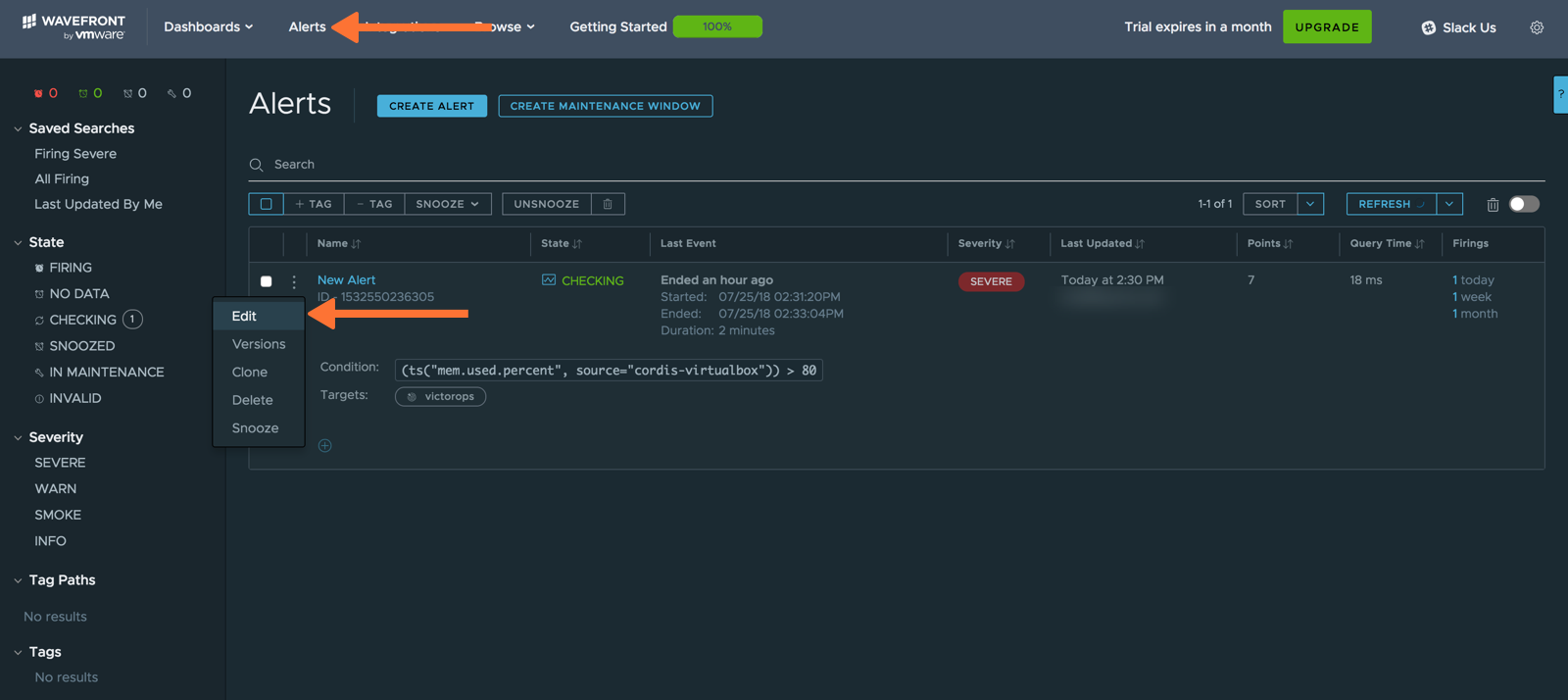
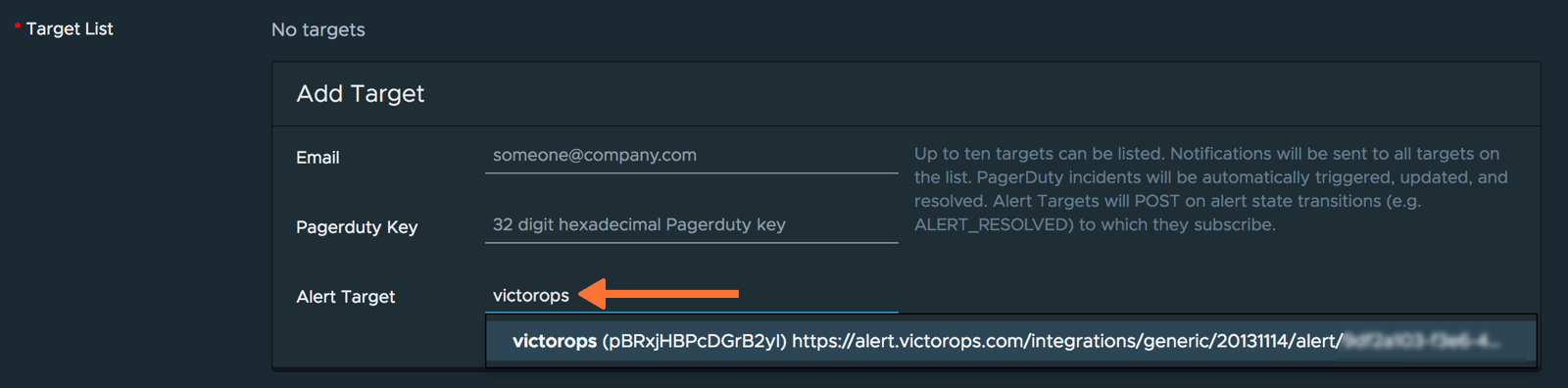
新しいアラートを作成する場合は、必要なアラート条件を指定します。「ターゲットリスト」の下に、VictorOpsアラートターゲットの名前を入力し始めます。VictorOpsアラートターゲットが選択できるように下に表示されます。Save をクリックします。
これでこのインテグレーションの設定は完了です。ご不明な点がございましたら、VictorOpsサポート までお問い合わせください。