Splunk On-CallのServiceNow双方向インテグレーション 🔗
注釈
古いXMLファイルからServiceNow App storeの新しいVictorOps双方向インテグレーションにアップグレードする場合、インストール前に以下のスクリプトを実行するか、サポートチームに連絡する必要があります: 初期のVictorOpsインテグレーションを非推奨にするスクリプト
最新のSplunk On-CallとServiceNowの双方向インテグレーションを使用して、インシデントに対応し、リアルタイムで共同作業を行い、より迅速な解決策を見つけることができます。
Splunk On-Call ServiceNow双方向インテグレーションは、インシデントとチケットの履歴を保持しますが、問題に対応している最中に気を散らすことはありません。詳細なインシデント履歴を使用して、インシデント発生後の徹底的なレビューを実施し、オンコールのインシデント管理を長期的に改善します。単一のアプリケーションで作業することで、コンテキストの切り替えをなくし、目の前の問題に集中し、チケットの整理に費やす時間を減らします。
インテグレーションによって以下のことができます。
リアルタイムのインシデント対応機能と詳細なチケットトラッキングを組み合わせ、オンコールのインシデント管理のための総合的なシステムを構築。
Splunk On-CallからServiceNowチケットを自動的に更新することで、リアルタイムの対応とコラボレーションを重視し、平均確認時間(MTTA)と平均修復時間(MTTR)を短縮します。
監視データ、オンコール・スケジュール、アラートを一元化し、インフラの健全性を可視化し、インシデント対応時に部門横断チームに情報を提供します。
Splunk On-CallからServiceNowに送信されるインシデント履歴の完全な記録により、インシデント発生後の徹底的なレビューを実施します
要件 🔗
対応するServiceNowのバージョン:Madrid、New York、Orlando、Paris、Quebec、Rome、San Diego、Tokyo、Utah、Vancouver、Washington DC、Xanadu
ServiceNowアカウント:アプリケーションレジストリを作成するためのServiceNow管理権限と、ITILロールを持つActive、Webサービスアクセスのみのユーザーが必要です。
必須Splunk On-Callバージョン:エンタープライズレベルのサービス
ServiceNowでSplunk On-Callを有効化する 🔗
ServiceNowストアからVictorOpsアプリケーションをダウンロードします。https://store.servicenow.com/sn_appstore_store.do#!/store/application/ad2abfc8db3ff7003e4af209af9619df を参照してください。ServiceNow StoreからGETを実行するには、HI認証情報が必要です。
「設定」内に次のプロンプトが表示されたら、Get Started を選択します。
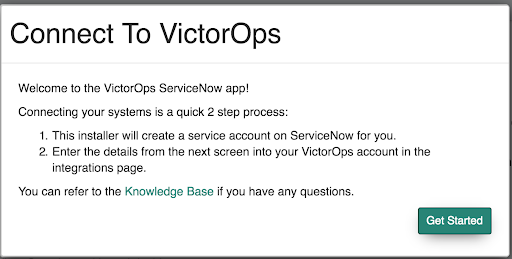
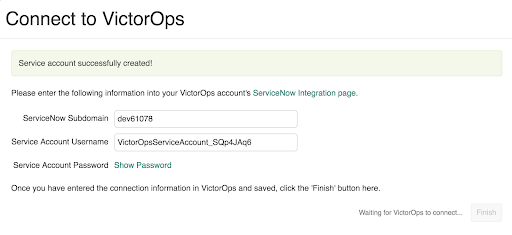
以下のダイアログボックスが表示され、Splunk On-Callで入力する必要がある情報が表示されます。Finish ボタンは、Splunk On-Callで認証情報を入力した後にのみ有効になります。
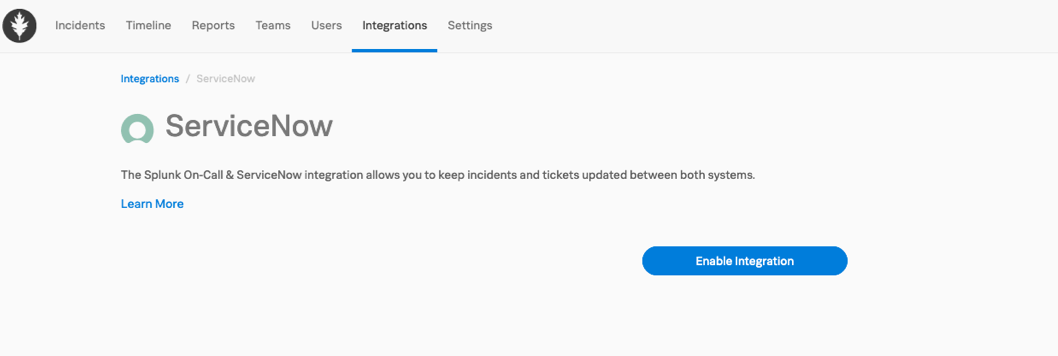
Splunk On-CallでServiceNowを有効化する 🔗
Integrations、ServiceNow の順に移動します。
Enable Integration を選択します。
ServiceNowインスタンスの認証情報を入力します。
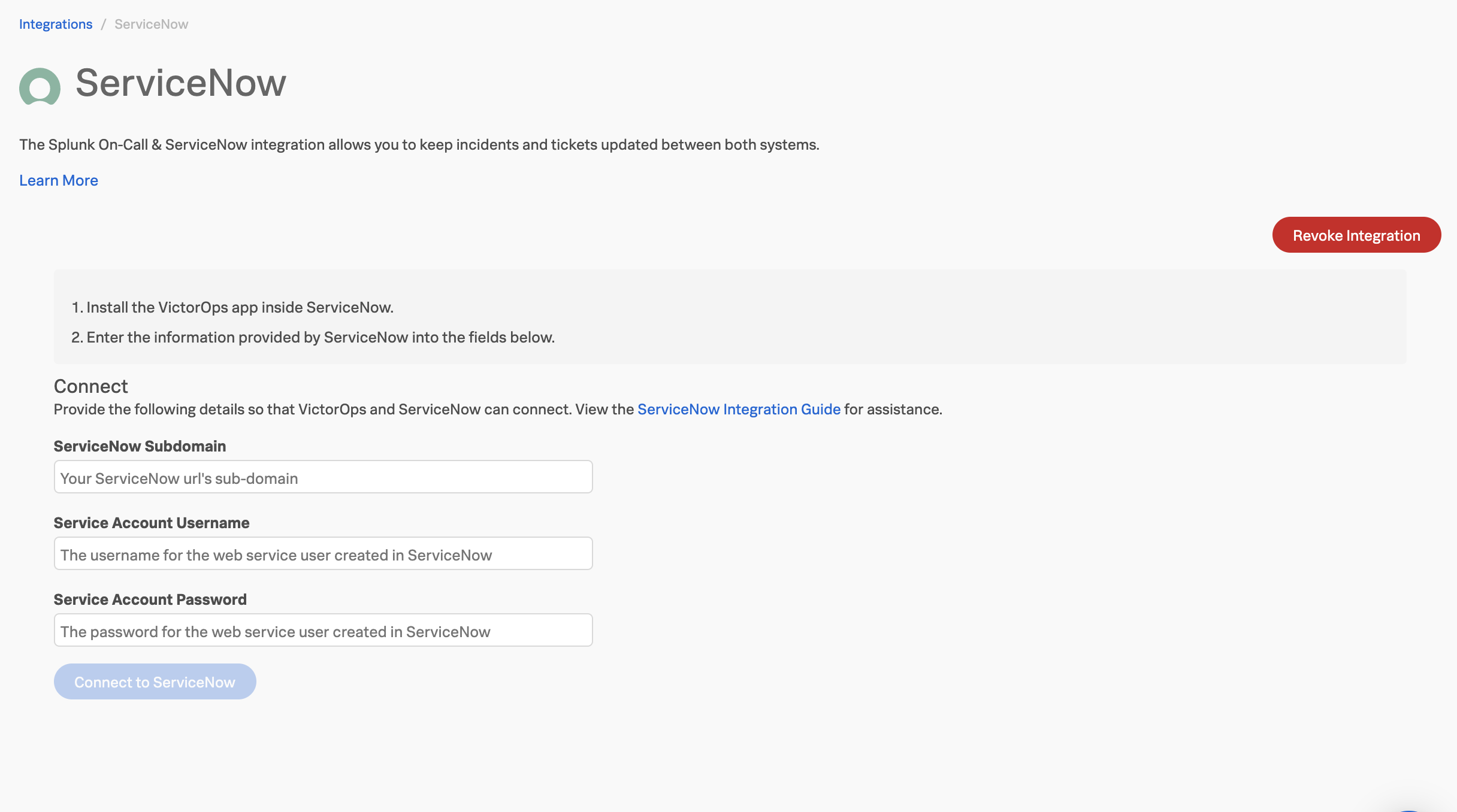
Connect to ServiceNow を選択します。接続が完了したら、ServiceNowに戻り、Finish を選択して認証を確定します。
マップインシデント状態 🔗
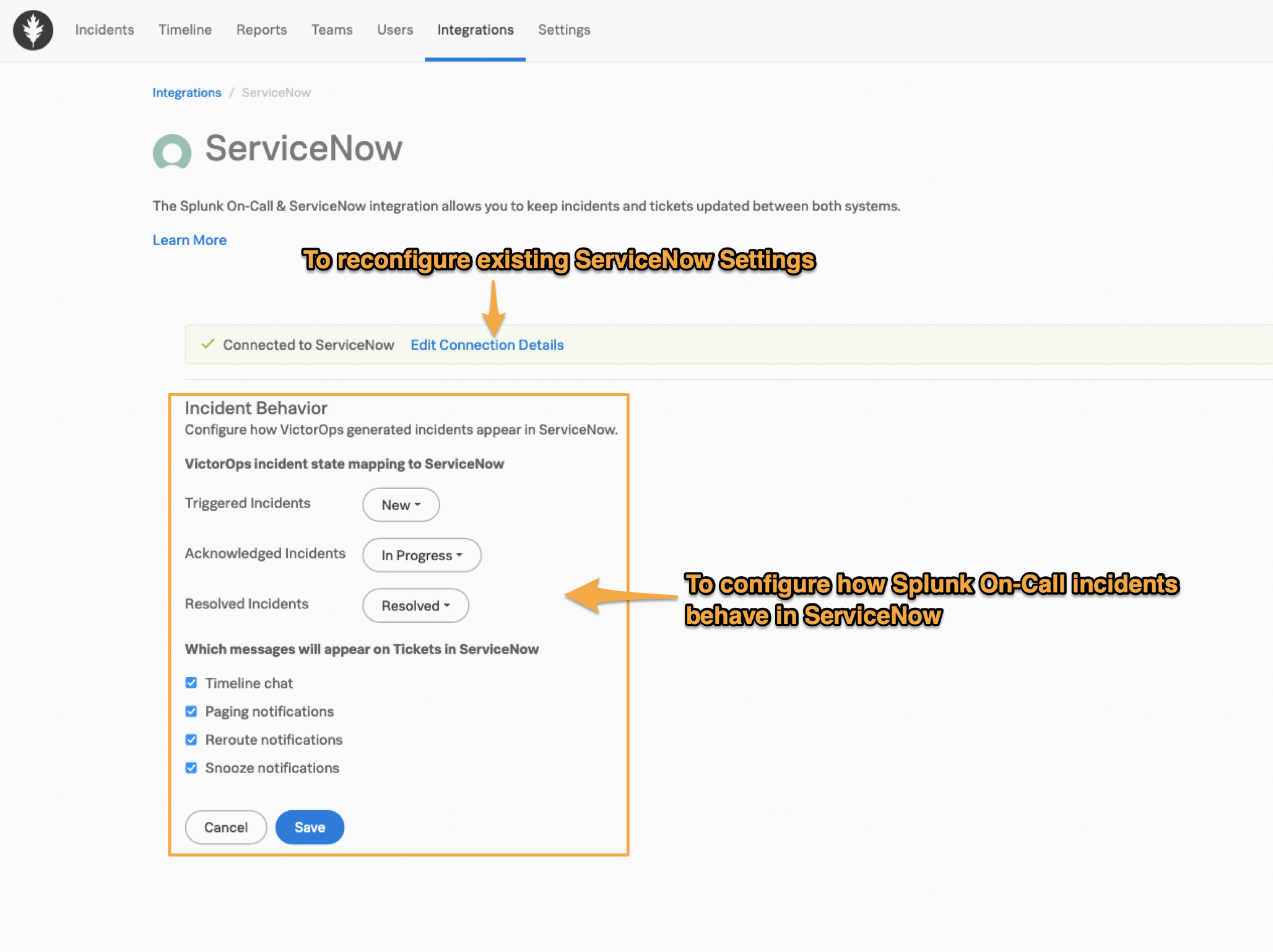
ServiceNowとSplunk On-Callは、インシデント状態マッピングを使用して同期を維持します。Splunk On-Callでインシデント状態マッピングを設定します。
Splunk On-Callインシデント状態を編集するには、Edit Integration ボタンを選択します。
ServiceNowの割り当てグループをマップする 🔗
認証情報を確認したら、Splunk On-CallエスカレーションポリシーをServiceNowの割り当てグループにマッピングします。このマッピングにより、Splunk On-Callからインシデントを送信する際にServiceNowの割り当てグループを更新したり、ServiceNowからインシデントを送信する際の送信先を決定したりすることができます。
マッピングが設定されると、ServiceNowの割り当てグループフィールドは、ページングされているエスカレーションポリシーに基づいて更新されます。このフィールドは、インシデントが別のエスカレーションポリシーに再ルーティングされた場合にも更新されます。インシデントが特定のユーザーに再ルーティングされた場合、割り当てグループはクリアされます。ServiceNowで割り当てグループを更新しても、Splunk On-Callのページング動作には影響しません。
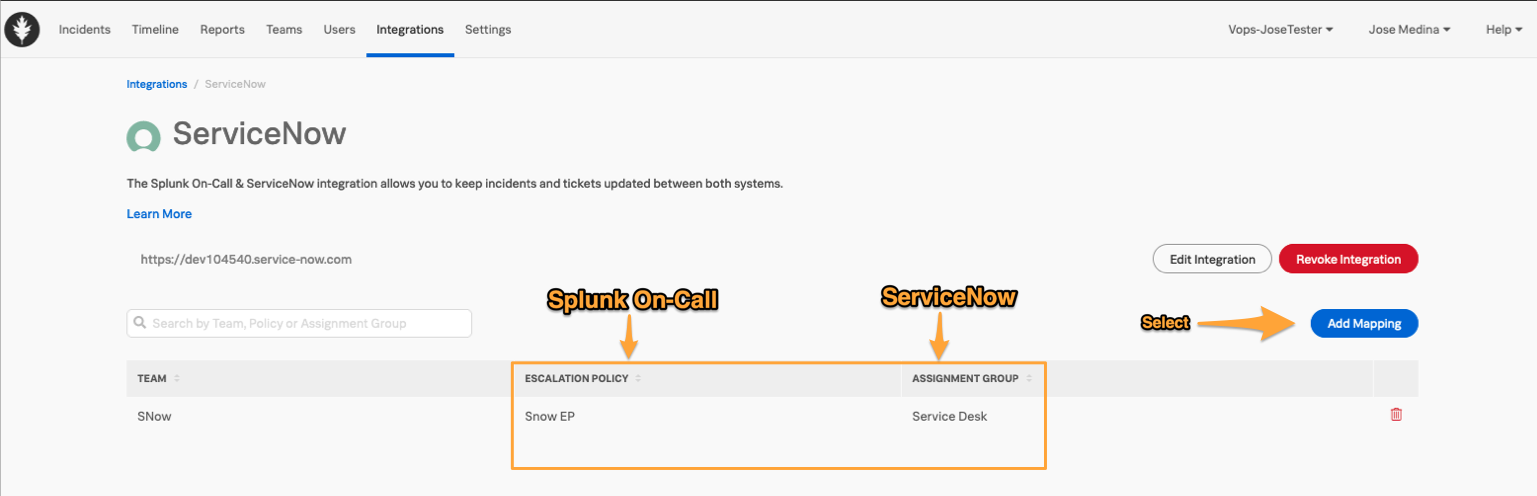
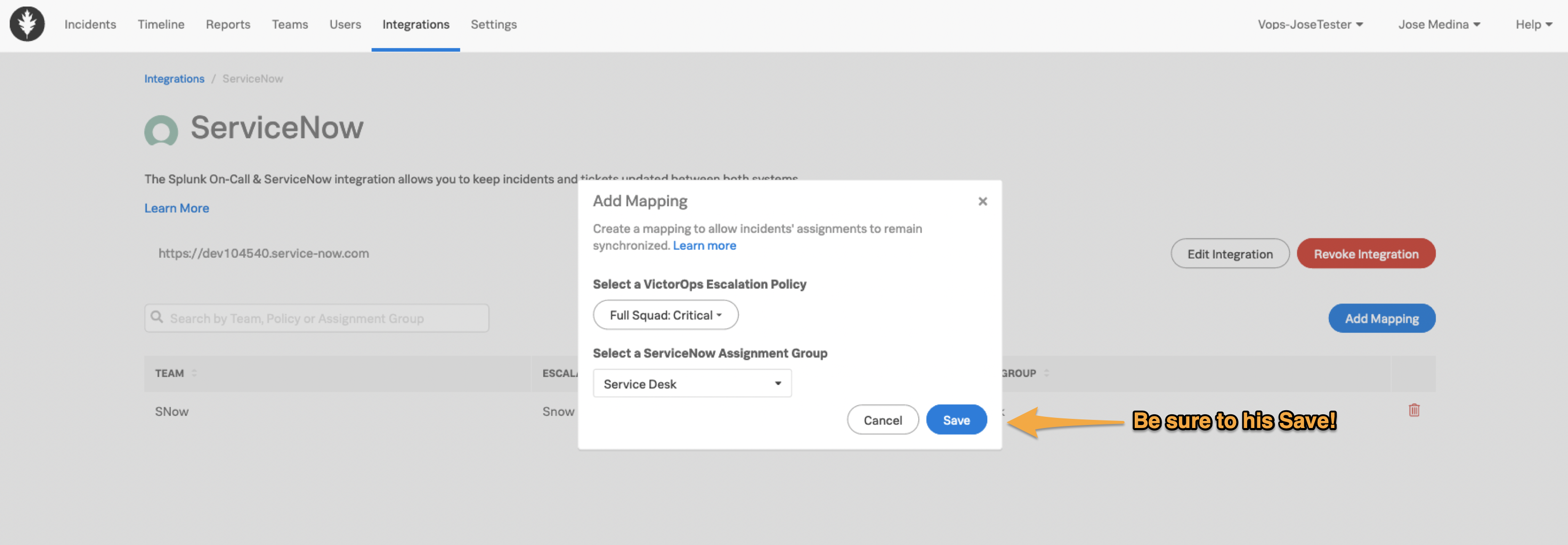
Add Mapping を選択して、利用可能な選択肢を確認します。
ServiceNow Assignment Groupについては、フィルターボックスに入力し、利用可能なさまざまなオプションを確認します。
マップユーザー 🔗
インテグレーションページを保存すると、メールの一致に基づいて、利用可能なすべてのユーザーがシステム間でマッピングされます。また、インシデントに対してアクションを実行する際にも、ユーザーがマッピングされます。
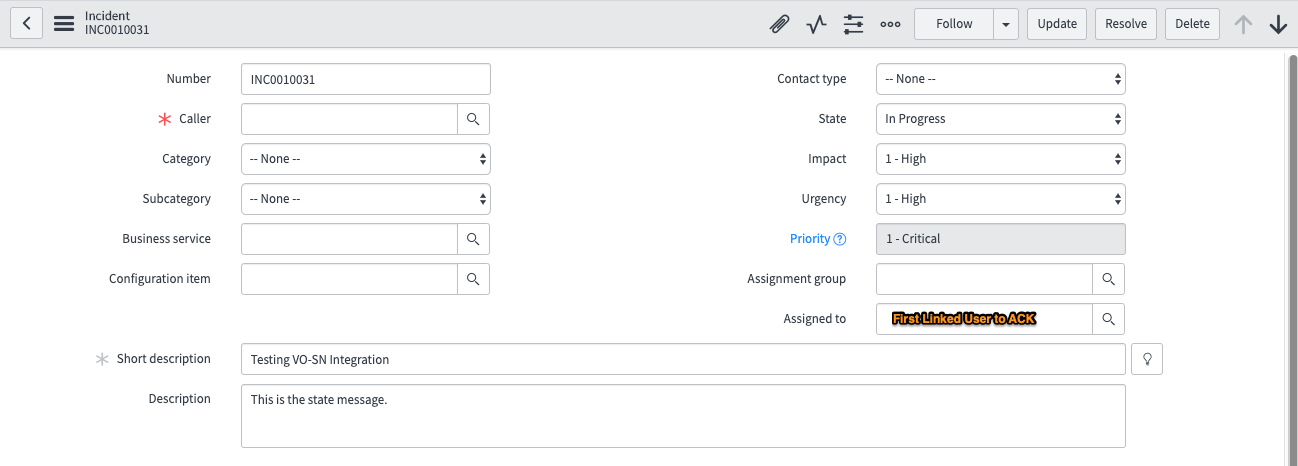
Splunk On-CallからServiceNow Assigned Toフィールドを更新する 🔗
ServiceNowのAssigned Toフィールドには、インシデントを最初に承認したユーザーが入力されます。Splunk On-Callインシデントがトリガー状態に戻った場合、次に確認したユーザーがフィールドに入力されます。
インシデントをリンクする 🔗
Splunk On-CallインシデントビューのサイドパネルでServiceNowインシデント番号を選択すると、ServiceNowチケットを開いて表示できます。
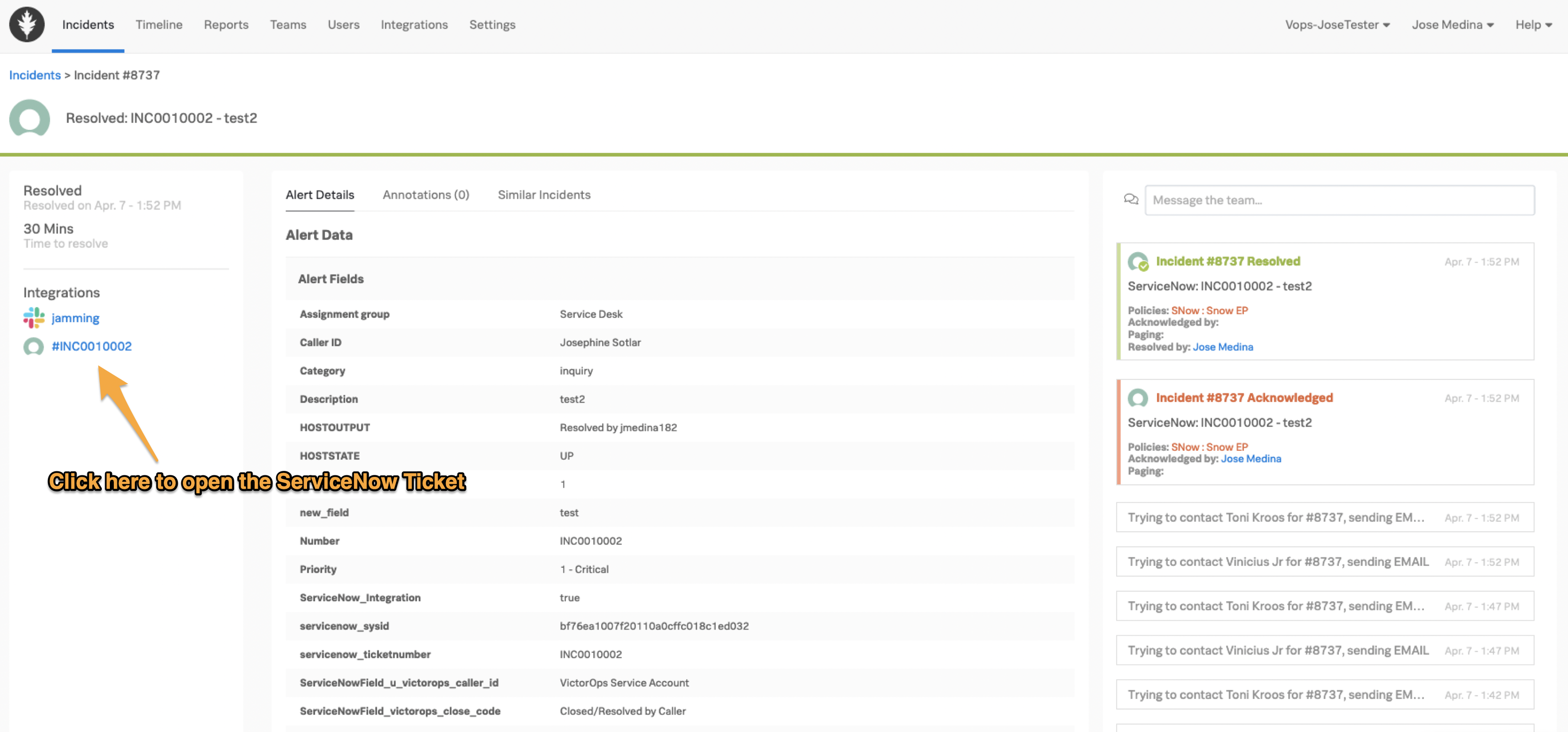
Splunk On-CallがServiceNowにインシデントを送信する場合 🔗
インテグレーションを完了するには、アラートルールを作成する必要があります。
Settings、Alert、Rules Engine の順に移動します。
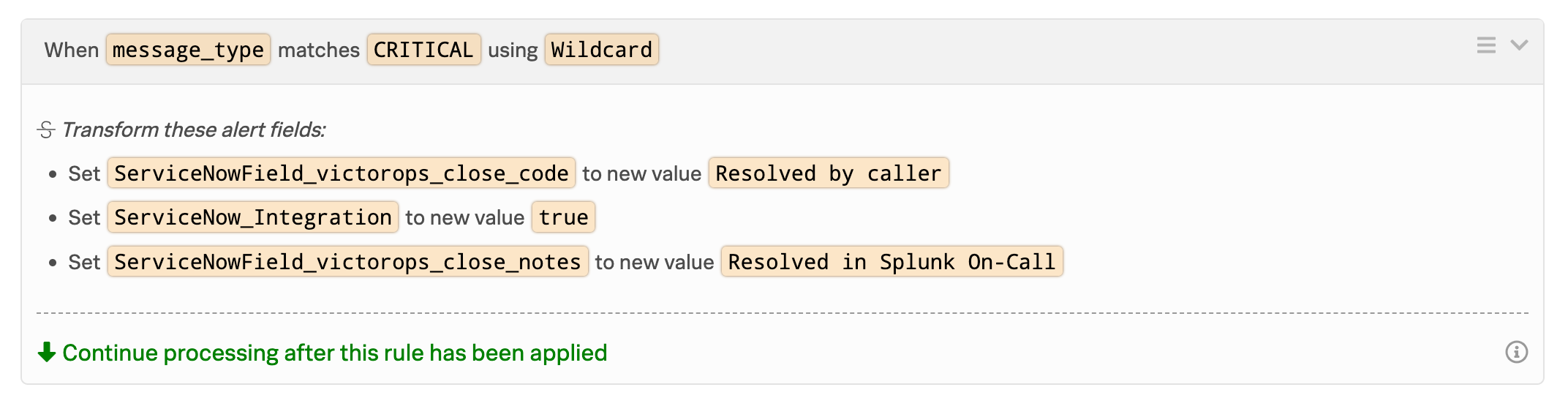
Splunk On-CallインシデントをServiceNowに送信するマッチング条件を定義するルールを追加します。ルールエンジンのマッチング条件 を参照してください。たとえば、すべての重要なインシデントをServiceNowに送信するには、次のようにします:
Wildcardを使用してmessage_typeがCRITICALに一致する場合ServiceNow_Integrationを新しい値trueに設定します。この例には、ServiceNowへのインシデントの自動解決を有効にするための解決フィールド情報も含まれています。
Splunk On-CallからServiceNowにフィールドをマッピングする 🔗
すぐに利用可能な設定済みフィールドは以下のとおりです:* close_code * close_notes * work_notes * short_description * description * state * assignment_group * assigned_to * resolved_by
ルールエンジンを使って、以下の構文ですべての事前設定フィールドを設定できます: ServiceNowField_victorops\_<field_name> または ServiceNowField_u_victorops\_<field_name>。特定の構文は特定のServiceNow環境のバージョンに依存し、テストが必要な場合があります。
以下のフィールドは、インテグレーションマッピングによって自動的に処理されます:
assignment_group
state、work_notes
short_description
description
assigned_to
resolved_by
必須カスタムフィールド 🔗
Splunk On-Callのアラートフィールドに基づいて値を動的に割り当てるには、次の構文」 ${{victorops_field_name}} を使用します。動的割り当てに関するヒントは ルールエンジンの変数展開 を参照してください。
一部のフィールドのみがVictorOpsアプリで事前に設定されているため、ServiceNowで追加のフィールドをマッピングするには追加の設定が必要です。
ServiceNowで、フィルターナビゲーターを使用して、」x_splu2_victorops_incident_import.list」を検索します。
空のフィールドがいくつかあるテーブルで、New を選択します。すべてのアクティブフィールドが表示されます。
Menu を選択し、Configure、Form Layout の順に確認します。
ルールエンジンで使用するフィールド名の新しいインポートテーブルフィールドを作成します。例えば、」VictorOps caller id」の場合、以下の構文が必要です:ルール用の
ServiceNowField_u_victorops_caller_id。#. Create New Field の下に、マッピングするフィールド名を追加します。Selected` 列に表示されているのと同じ形式を維持します:VictorOps <フィールド名>。#. フィールドの長さを Medium に変更します。#.guilabel:追加`を選択します。フィールドが「選択済み」列に追加されます。#. :guilabel:`Save を選択します。フィルターナビゲーターに戻り、System Import Sets の下にある「Transform Maps」を検索します。
その後、」VictorOps Incident」を検索してください。」テーブルトランスフォームマップ」ページ内の検索ボックスを使用できます。
VictorOps Incident` テーブルトランスフォームマップを開き、Field Maps までスクロールします。
Mapping assist を Field Maps` タブで選択します。
マッピングアシストのページには3つのボックスがあります。最初のボックスは Source Fields です。次のボックスはフィールドのマッピングです。最後のボックスは Target Fields です。#. まず、Source Field` で作成したフィールドの名前を検索します。それを選択し、追加矢印を選択します。#. 次に、Target Field で同じことを実行します。マッチさせたいターゲットフィールドを検索して割り当て、フィールドマップボックスに追加します。#. 最後に、Field Map フィールドで、2つのフィールドがマッピングされていることを確認します。#. Save を選択します。
これで、Splunk On-Callアラートルールエンジンを使用して、以前と同じ構文でフィールド値を供給できるようになりました: ServiceNowField_<field_name> または ServiceNowField_u_victorops\_<field_name> (ServiceNowのバージョンによる)を新しい値 <value> に設定します。
以下の例では、ServiceNowのSplunk On-Callインポートテーブルのフィールド値は victorops_custom_field です。
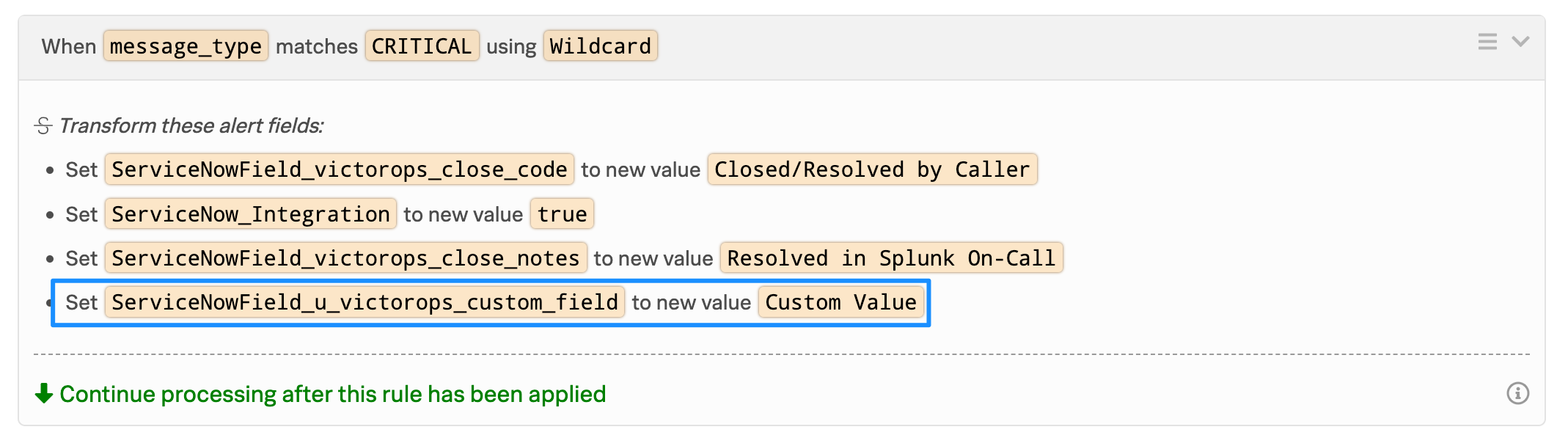
注釈
ServiceNowのフィールド名に大文字が含まれている場合は、Splunk On-Callでアラートルールを作成する際に小文字に置き換えてください。たとえば、A custom ServiceNow Field Test Field は、アラートルールでは ServiceNowField_test_field になります。
インシデントとフィールドをSplunk On-Callに送信するロジックを設定する 🔗
ServiceNowは以下のフィールドを自動的にSplunk On-Callに送信します:
assigned_to
assignment_group
caller_id
カテゴリ
description
数
優先順位
short_description
state
サブカテゴリ
sys_id
さらにフィールドを含めるには、カスタムフィールドをカンマ区切りで追加します。Splunk On-Call内のアラートペイロードで利用可能になります。
インシデントルールを使用してカスタムロジックを作成し、ServiceNowからSplunk On-Callにインシデントが自動的に送信されるタイミングに関するロジックを設定できます。
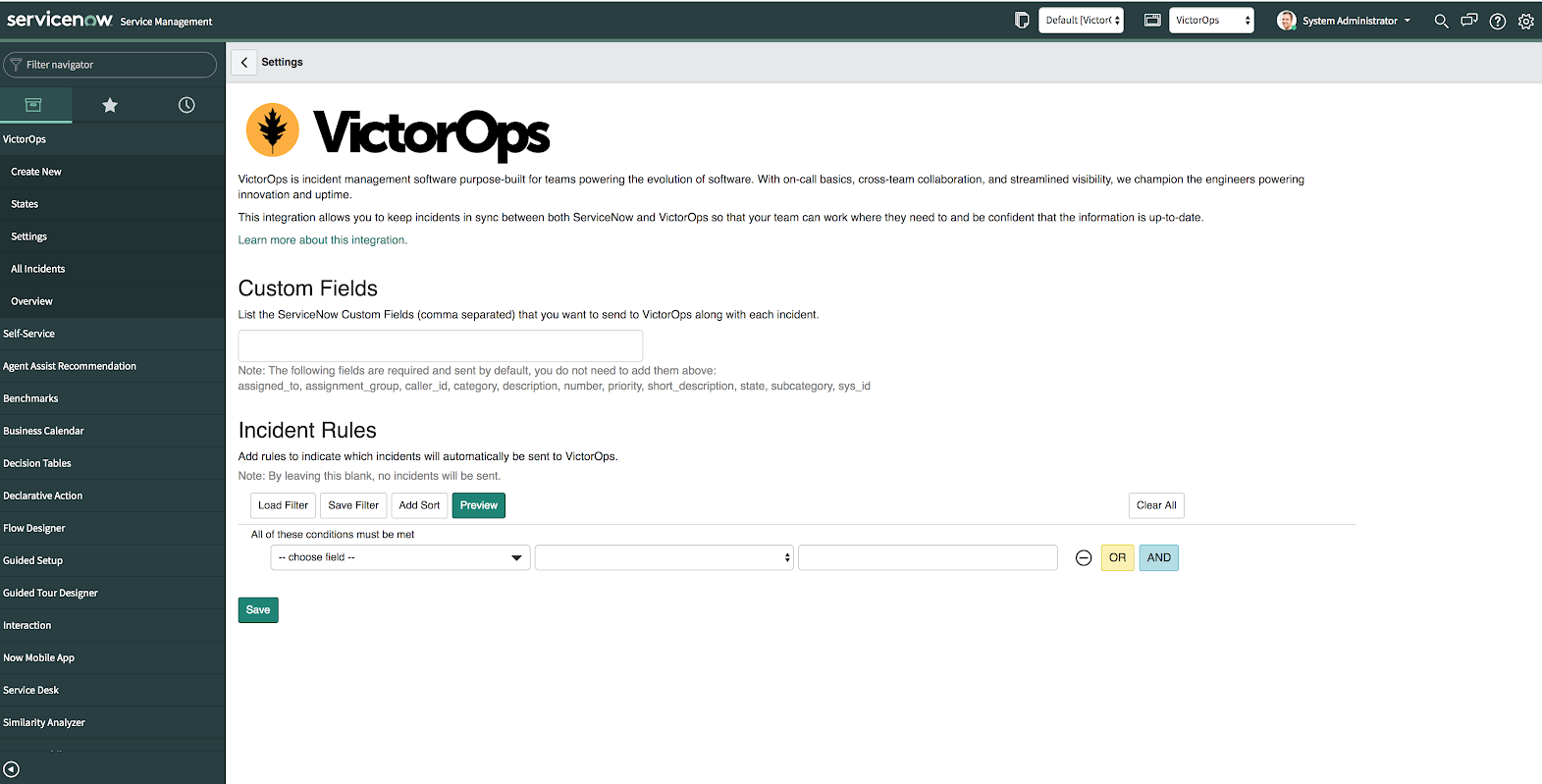
インシデントルールまたはカスタムフィールドの保存に問題が発生した場合は、Application Scope が現在 Splunk > VictorOps に設定されていることを確認してください。
ServiceNowからSplunk On-Callに手動でインシデントを送信する 🔗
インシデントルールが満たされていない場合でも、Send to VictorOps ボタンを選択して手動でインシデントをSplunk On-Callに送信することで、割り当てグループを含む必要な情報を添えてインシデントを送信できます。
Splunk On-Call and ServiceNow CMDB 🔗
VictorOpsアプリは、インシデントテーブルに存在するcmdbアイテムフィールドを設定することでServiceNow CMDBと対話できます。Splunk On-CallアラートルールエンジンとServiceNow トランスフォームマップを活用することで、これらのフィールドと対話することができます。Splunk On-CallからServiceNowにフィールドをマッピングする を参照してください
トラブルシューティング 🔗
アクセス許可エラーメッセージ 🔗
「ServiceNowは接続されていますが、インテグレーションを機能させるための適切なアクセス許可がありません」というメッセージが表示された場合、このアプリは、ServiceNowの初期設定に必要と思われるロールでサービスユーザーを構成します。ServiceNowのインスタンスに固有の追加のロールが必要になることはよくあります。インスタンスで必要なロールのサブセットを特定し、サービスユーザーアカウントに追加する必要があります。これが該当するかどうかを確認する1つの簡単な方法は、一時的にadminロールを追加することです。その後、インテグレーションをテストしてください。すべてが期待どおりに動作する場合、識別して追加する必要があるロールがいくつかあるか、ロールのサブセットがあります。
APIタイムアウトメッセージ 🔗
Splunk On-Callのインシデントとタイムラインに「ServiceNow APIコールがタイムアウトしました」というメッセージが表示された場合、Splunk On-CallはServiceNowからの応答を10秒待ってから試行されたリクエストをドロップします。多くの場合、ServiceNowはAPIコールをキューに入れますが、Splunk On-Callが時間内に応答を受信しなかったため、VictorOpsインシデントとServiceNowインシデント間のリンクは確立されません。リクエストを高速化するには、ServiceNowでインシデントテーブルのフィールド x_splu2_victorops_victorops_incident にインデックスを適用します。