Splunk On-CallのSSO ベータ版インテグレーション 🔗
免責事項 🔗
このドキュメントはSplunkの`Webサイト利用規約<https://www.splunk.com/en_us/legal/terms/terms-of-use.html>`__に従うものとします。本インテグレーションの使用は、Splunkとの契約およびSplunkのプライバシーポリシーに基づく、データプライバシーの義務を含むお客様の義務を条件として許可されていることをご了承ください。
これはベータリリースであり、不具合や欠陥が含まれている可能性があります。ご自身の責任においてご利用ください。Splunkは本機能について、商品性、特定目的への適合性、および取引の過程や慣習、または法令や法律に起因するその他の黙示的な保証を含め、一切の保証を放棄します。Splunkは、本機能がお客様の要求を満たすこと、エラーがないこと、正確であること、信頼できること、完全であること、中断されないことを保証しません。本機能は、サポート、アップデート、アップグレード、またはお客様との契約に基づくSplunkからのその他のコミットメントの対象ではありません。Splunkは本機能を評価目的でのみ利用できるようにしており、全機能を開発する、または将来のリリースに本機能を含める義務を負いません。
重要な注意事項 🔗
この記事では、SCIM/ULM設定を使用してSSOを設定する方法を説明します。代わりに SAML設定 を使ってSSOを設定する必要がある場合は、Splunk On-Call用のシングルサインオンを設定する を参照してください。
SCIM Single Sign-Onの設定と、Splunk On-Call(旧VictorOps)によるOktaプロビジョニングの初期アクティベーションは、現在セルフサービスプロセスではないため、サポートチームへのお問い合わせが必要です。
Oktaのアプリ名は**VictorOps (ベータ版)**であることにご注意ください。
警告 🔗
ユーザーをプロビジョニング解除すると、そのユーザーのSplunk On-Callから以下の属性が永久に削除され、ユーザーはログインできなくなります。
Oktaに存在しないSplunk On-Callユーザーの連絡方法
プッシュ通知のためのユーザーモバイルデバイス登録
ユーザーページングポリシー
ユーザーチームメンバー
ユーザーオンコールローテーションメンバー
オンコールのエスカレーションポリシーとスケジュールされたオーバーライドからユーザーを削除します。
以前にプロビジョニングを解除したユーザーを再割り当てしても、Splunk On-Callでは上記の属性は回復しません。
機能 🔗
SAMLとSCIM 2.0ユーザープロビジョニングを使用したシングルサインオン。
以下のプロビジョニング機能がサポートされています:
新規ユーザーをプッシュする
OktaでVictorOps (ベータ版)アプリに割り当てられたOktaユーザーには、Splunk On-Callユーザー名が作成され、プロビジョニングされます。
プッシュユーザーの無効化
ユーザーを非アクティブにするか、Oktaを介してユーザーのVictorOps (Beta)アプリケーションへのアクセスを無効にすると、Splunk On-Callのユーザーは非アクティブになります。
注意: このシナリオでは、ユーザーを無効化するとは、そのユーザーをSplunk On-Call組織から削除することを意味します。
そのユーザーはSplunk On-Callにログインできなくなります。
そのユーザーは、オンコールローテーションに参加できなくなります。
ユーザーを再有効化する
ユーザーアカウントはアプリケーションで再有効化できます。再有効化されたユーザーは、Splunk On-Callで手動による再設定が必要になります。
設定プロセスの概要 🔗
初期要件を満たします。詳しくは以下をご覧ください。
サポートがサポート側の処理を完了するのを待ちます。
OktaのVictorOps (ベータ版)アプリでSSOセットアップを完了します。詳細は以下をご覧ください。
OktaのVictorOps (ベータ版)アプリにユーザーまたはグループを割り当てます。
Splunk On-CallへのSSOサインオンをテストします。
顧客の初期要件 🔗
Splunk On-Call組織のグローバル管理者である必要があります。
Okta上でVictorOps (ベータ版)アプリの**全般**設定と**サインオン**オプションが構成されていることを確認してください。以下の手順を参照してください:初期セットアップ。
OktaのVops (ベータ版)アプリに割り当てられるユーザーのリストを提供してください。まだアプリにユーザーを割り当てないでください。
IDプロバイダーメタデータのURLを指定してください。
初期設定(Oktaの場合) 🔗
Okta User Homepageから**Admin**を選択します。
Adminを選択すると、Oktaダッシュボードが表示されます。Okta Adminダッシュボードから アプリケーション をクリックし、アプリケーションを追加する を選択します。
検索バーで“VictorOps (ベータ版)を検索します。検索結果の「VictorOps (ベータ版)」をクリックして開きます。
ページが読み込まれたら、」追加」ボタンをクリックします。
アプリケーションのラベルには、VictorOps (ベータ版)という名前が自動入力されますが、このラベルの名前を自由に変更して、次へ をクリックします。
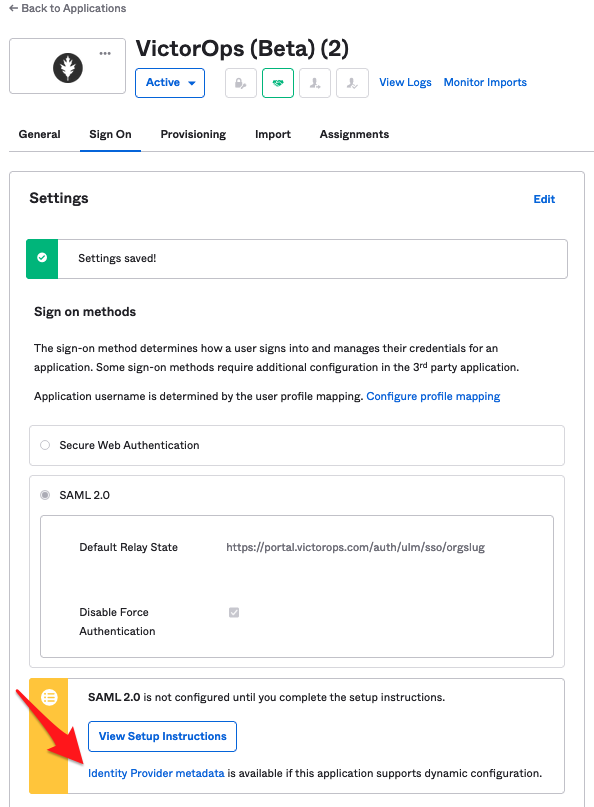
読み込まれたページで、SAML 2.0 ラジオボタンをクリックします。
6.このステップには**Splunk On-Call** (旧VictorOps)**organization identifier (またはOrg Slug)が必要です。識別子を見つけるには、Splunk On-Callアカウントにログインし、ブラウザのアドレスバーにURLを表示します。以下のスクリーンショットの例では、」Your Org Slug」が組織識別子です。

DefaultRelayState テキストボックスに以下を追加する:
https://portal.victorops.com/auth/ulm/sso/<your-org-identifier>組織識別子 には、組織識別子だけを入力します。
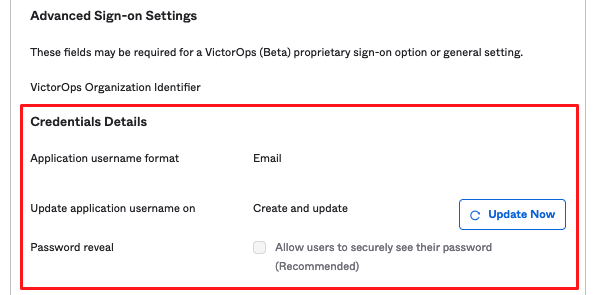
アプリケーションユーザー名の形式を選択してください:メール (これは現在サポートされている唯一のオプションです)
7. Copy the URL linked to the Identity Provider metadata link to your clipboard, and click Done.
8. Once you configure the General and Sign-On options, please open a support ticket with subject “Okta SCIM setup request” and ask to configure Okta SCIM SSO for your Splunk On-Call organization. Provide the URL link you copied from the Identity Provider metadata from step 7 above and the list of users you will be assigning to the VictorOps (Beta) App in Okta.
Splunkオンコールサポートチームからの返答を待ってから、以下の最終的な手順に従ってください。
SSOセットアップの確定 🔗
Splunk On-Callからベアラートークンを取得する
以下の手順を実行する前に、Splunk On-CallサポートチームがSSOを設定していることを確認してください。
1. Once Splunk On-Call support team configures SSO for your account, login as Global Admin to Splunk On-Call.
2. Navigate to Integrations >> API. If API Access is disabled, click on Activate API Access. More details on API access can be found here Splunk On-Call API.
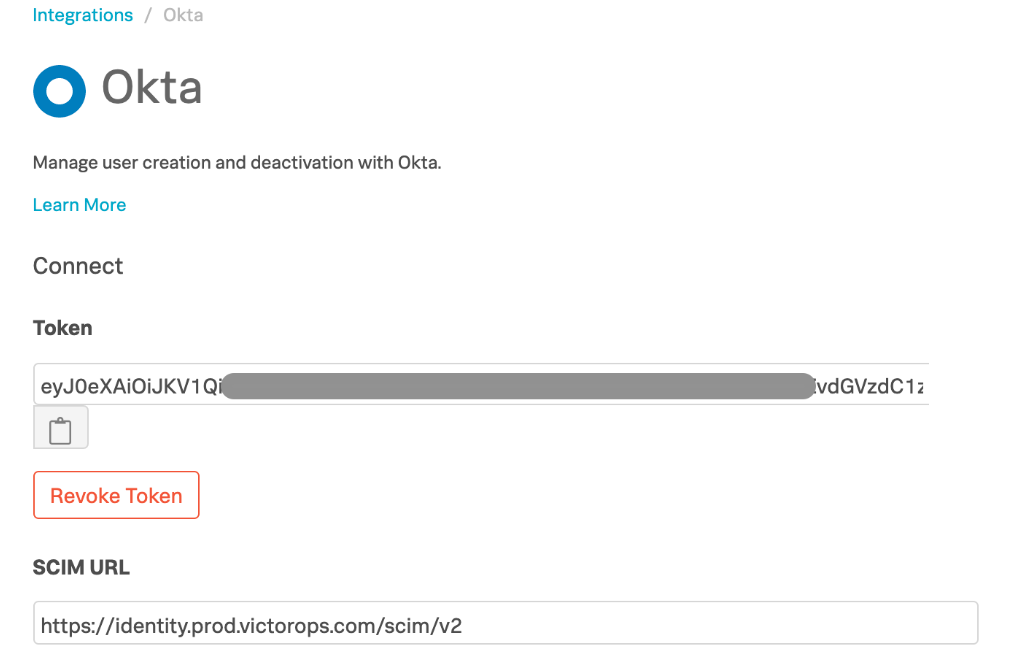
インテグレーション >> サードパーティインテグレーション をクリックします。検索バーで「Okta」を検索し、表示されたタイルをクリックします。
2. In the result page, click on Enable Integration which will generate a bearer token as shown below. If Okta is already enabled and you wish to generate a new token, click Revoke Token and reenable the integration.
5. Copy the token and save it in a temporary place as you will need it in subsequent steps.
プロビジョニングセットアップ(Oktaの場合)
以下の手順を実行する前に、Splunk On-CallサポートチームがSSOを設定していることを確認してください。
1.OktaのVictorOps (ベータ版)アプリケーションに移動し、Provisioning タブをクリックし、Configure API Integration をクリックします。
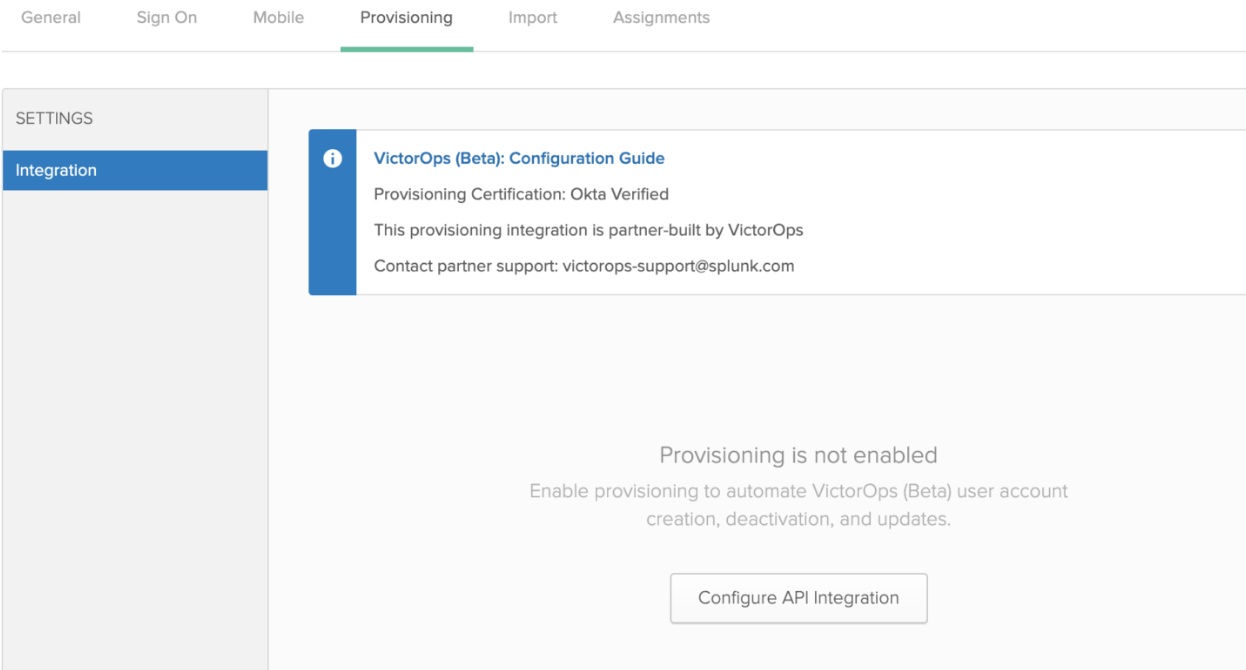
2. Select Enable API integration and paste the API token copied from Splunk On-Call (step 5 from In Splunk On-Call section above). Click Test API Credentials to verify the API communication is working correctly between Okta and Splunk On-Call. Click Save.
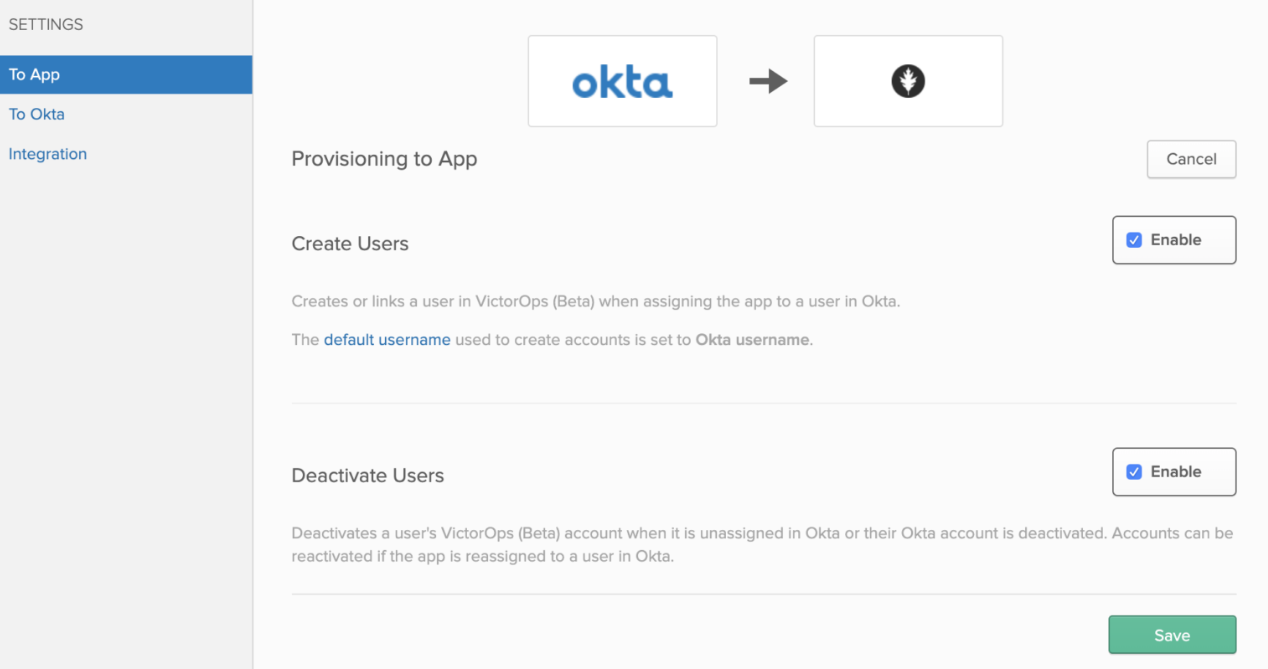
3. Click on To App under Provisioning tab. Click Edit and select Enable for Create Users and Deactivate Users. Click Save.
最終ステップ
上記の手順が完了したら、SSO SCIMの設定は完了です。** VictorOps (ベータ版)** アプリを任意のグループまたはユーザーに割り当てられるようになりました。 プロビジョニングされたユーザーは、Oktaアプリケーション(chiclet)を使用して、SSOを使用してSplunk On-Callにログインできます。
OktaのVictorOps (ベータ版)アプリは、On-Callインスタンスにも新しいユーザーをプロビジョニングできるようになりました。アプリに割り当てる新規ユーザーはすべてOn-Callにプロビジョニングされ、On-Callのユーザー名としてメールが使用されます。
ユーザープロビジョニングプロセス 🔗
このセクションでは、Okta-Splunk On-Callインテグレーションが有効になっている場合に、OktaユーザーアカウントがSplunk On-Callユーザーアカウントにどのようにリンクされるかについて説明します。
ユーザープロファイルは、2つのシステム間で以下のように接続されます:
OktaがSplunk On-Callに新規ユーザーのプロビジョニングリクエストを送信します
Splunk On-Callはリクエストからユーザーのプライマリメール属性を取得します。
Splunk On-Callは、同じメールアドレスを含むマッチするユーザープロファイルを検索します。
ユーザーが見つからない場合、Splunk On-Callに新しいユーザーが作成されます。
ちょうど1人のユーザーが見つかった場合、そのOktaユーザーはSplunk On-Callユーザーにリンクされます。
複数のユーザーが見つかった場合、Oktaにエラーが返され、プロビジョニングリクエストは失敗します。このエラーを修正するには、OktaプロファイルのメールアドレスがSplunk On-Callの1つのユーザープロファイルにのみ存在することを確認します。
ユーザーが見つかっても、アカウントが以前にすでにリンクされている場合は、エラーが返されます。この問題を解決するには、Splunk On-Callサポートにご連絡ください。
ユーザーのプロビジョニング解除プロセス 🔗
Splunk On-Callからユーザーを無効化するOktaリクエストは、以下のように処理されます:
オンコールローテーション、エスカレーションポリシーの一部であるユーザー、またはスケジュールされたオーバーライドで他のユーザーのオンコールをオーバーライドしているユーザーが削除される場合
1.ユーザーが所属するすべてのチーム、またはユーザーがスケジュールされたオーバーライドまたは手動オンコールを行ったチームを検索します。2.各チームについて:
そのユーザーがチーム内のオンコールローテーションまたはエスカレーションポリシーに属していない場合、そのユーザーはチームから削除されます。そうでない場合は、次のステップに進みます。
チーム内の管理者をこの順番で探してください:チーム管理者、アラート管理者、グローバル管理者、非管理者。
プッシュ通知用の携帯端末を登録しているユーザー、またはプロファイルに電話番号の確認が取れているユーザーが優先されます。
上記の2つのステップの結果、複数のユーザーが存在する場合、ユーザー名A->Zでソートした後、最初のユーザーを選択します。
オンコールローテーションとエスカレーションポリシーにおいて、削除されたユーザーの代わりとなるユーザーを配置します。
代替ユーザーにはメールで通知されます。メールでは、ローテーションのリスト、変更されたエスカレーションポリシー、およびオーバーライドが変更されたかどうかも通知されます。
3. If the user to be removed is the only member in a team, then an error message is returned to Okta and the remove-user operation is not completed in Splunk On-Call.
他のユーザーから手動でオンコールを受け、現在オンコール中のユーザーの場合
上記と同じプロセス。
Splunk On-Call orgで唯一のグローバル管理者であるユーザーを削除する場合 🔗
この操作はサポートされていないため、Oktaにエラーが返されます。
上記のチェックと置換が完了すると、そのユーザーはSplunk On-Callの所属組織から削除され、ログインできなくなります。
トラブルシューティング 🔗
OktaでAPI資格情報のテストに失敗する
Splunk On-Callからコピーしたトークンに先頭または末尾にスペースがないことを確認してください。このエラーが表示され続ける場合は、Splunk On-Callサポートチームまでお問い合わせください。
Oktaのユーザープロファイル属性の更新がSplunk On-Callに反映されません。
ユーザー名を含むSplunk On-Callのユーザープロファイル属性の更新は現在サポートされていません。特定のユーザーのプロファイルの更新が本当に重要な場合は、Oktaからそのユーザーを削除することで回避できます。そして Oktaで新しいユーザーを作成し、Splunk On-Callアプリケーションに割り当てます。これにより、Splunk On-Callに必要なユーザープロファイル属性を持つ新しいユーザーが作成されます。
エラー:このOktaユーザーは、Splunk On-Callの別のユーザーとメールアドレスが既にリンクされています
OktaユーザーがSplunk On-Callのユーザーにすでにリンクされている場合、このエラーが表示されることがあります。Splunk On-Callサポートにお問い合わせください。
エラー:Oktaユーザーのメールアドレスで複数のSplunk On-Callユーザーが見つかりました
指定したメールアドレスを持つユーザーがSplunk On-Call組織に1人しか存在しないことを確認します。
エラー:このユーザーは、この組織の最後のSplunk On-Call グローバル管理者であるため、Splunk On-Callから削除できません
アクティブなSplunk On-Callアカウントに少なくとも1人のグローバル管理者が存在する必要があります。Splunk On-Callにログインし、グローバル管理者ロールを別のユーザーに割り当てて、この操作を再試行してください。
エラー:このユーザーは、オンコールローテーションまたはエスカレーションポリシーの一部であり、代替ユーザーが見つからないため、Splunk On-Callから削除できませんでした
Splunk On-Callにログインし、依存するオンコールローテーション、エスカレーションポリシー、またはチームを削除してから、この操作を再試行してください。
エラー:別のOktaユーザーが、このメールアドレスでSplunk On-Callのユーザーに既にリンクされています
指定したメールアドレスでOktaユーザーが1人しか存在しないことを確認します。
あるいは、マッチするSplunk On-Callユーザーに2つのメールアドレスがあり、それぞれが異なるOktaユーザーを指していないか確認してください。このようなマッピングは避けるべきです。