Splunk On-CallのDatadogインテグレーション 🔗
DatadogとSplunk On-Callのインテグレーションを使用し、Datadogイベントストリーム内の@メンションを使用して、Datadogからのコンテンツをタイムラインに送信します。
要件 🔗
必須Splunk On-Callバージョン:** Starter、Growth、またはエンタープライズ
Datadogが提供するインシデントへのリンクに注釈を付けるには、エンタープライズ機能であるSplunk On-Callルールエンジンを使用する必要があります。
Splunk On-Callでインテグレーションを有効にする 🔗
Integrations、3rd Party Integrations、Datadog の順に移動します。
Enable Integration を選択します。
Service API Key をクリップボードにコピーします。
Datadogを設定する 🔗
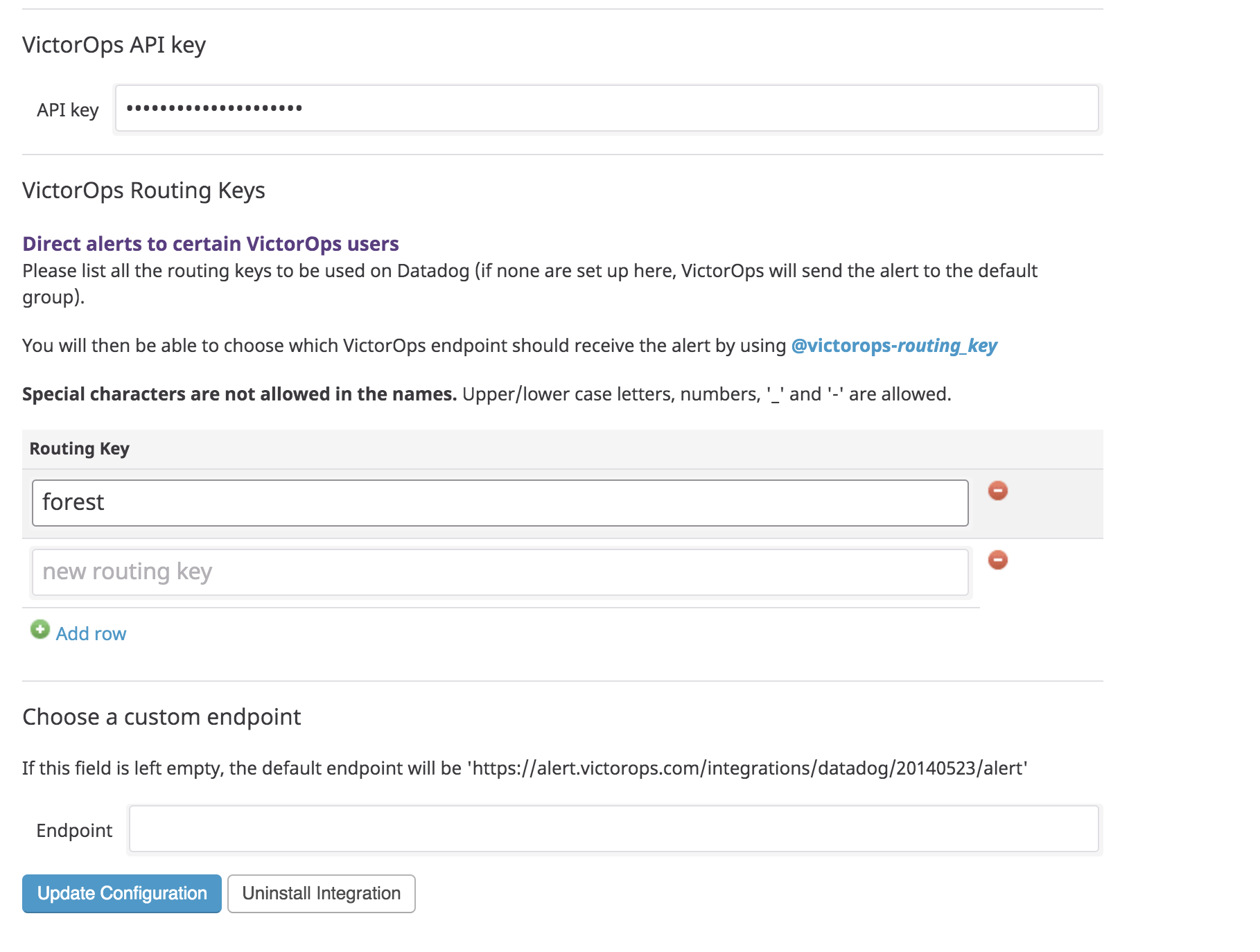
サイドバーメニューで Integrations を選択し、VictorOpsインテグレーションを見つけ、Available を選択し、Install を選択します。

ダイアログボックスで、設定タブを選択します。
Splunk On-Callから取得したサービスAPIキーと、使用するSplunk On-Callルーティングキーを貼り付け、Update Configuration を選択します。
@victoropsをDatadogメトリクスモニターに追加します。モニターが対応するVictorOpsインシデントを確実に自動解決するには、モニターの通知ステップで @victoropsが選択されていることを確認します。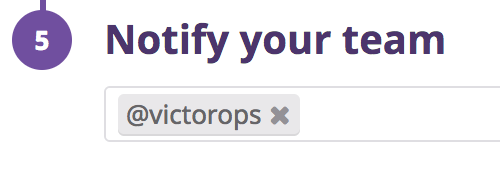
Splunk On-CallからDataDogモニターを解決する 🔗
通常、インシデントの発生元であるDatadogにモニターインシデントを解決させるのが最善です。しかし、Splunk On-Callからインシデントを解決したい場合は、以下の手順で行います。
要件 🔗
カスタム発信Webhookとアラートルールエンジンはエンタープライズ機能です。
ステップ 🔗
Integrations にアクセスし、Splunk On-Callの Outgoing Webhooks にアクセスします。
- 以下の詳細で新しいカスタム発信Webhookを作成します。例のように、URLの末尾に特定のDatadog API認証情報を追加します。
Event フィールドで、Incident-Resolved を選択します。
Method に POST を選択します。
Content Type に application/json を選択します。
To フィールドに、この例のようにDatadog API認証情報を入力します:
https://api.datadoghq.com/monitor/bulk_resolve?api_key=<datadpg_api_key>&application_key=<datadog_app_key>以下のペイロードを貼り付けます:
{ "resolve": [ { "${{ALERT.datadog_monitor_id}}": "ALL_GROUPS" } ] }
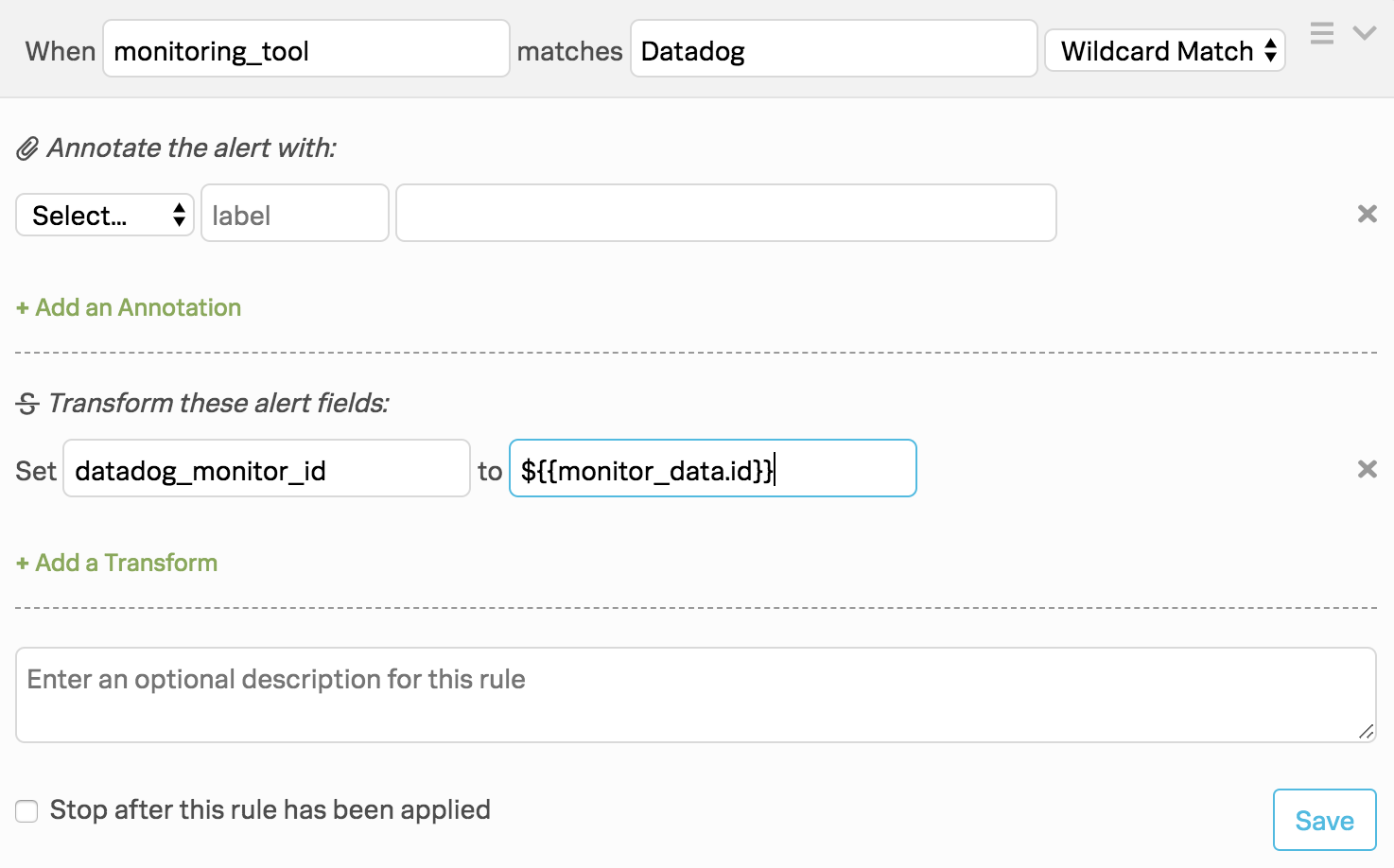
次に、作成したWebhookを条件付きで起動するアラートルールエンジンルールを作成します。そのためには、Settings、Alert Rules Engine の順に移動して、以下のルールを作成します:#. monitoring_tool が Datadog に一致する場合#.:guilabel:Transform these alert fields で以下の変換を設定します: datadog_monitor_id を選択し、次に ${{monitor_data.id}} を選択します。
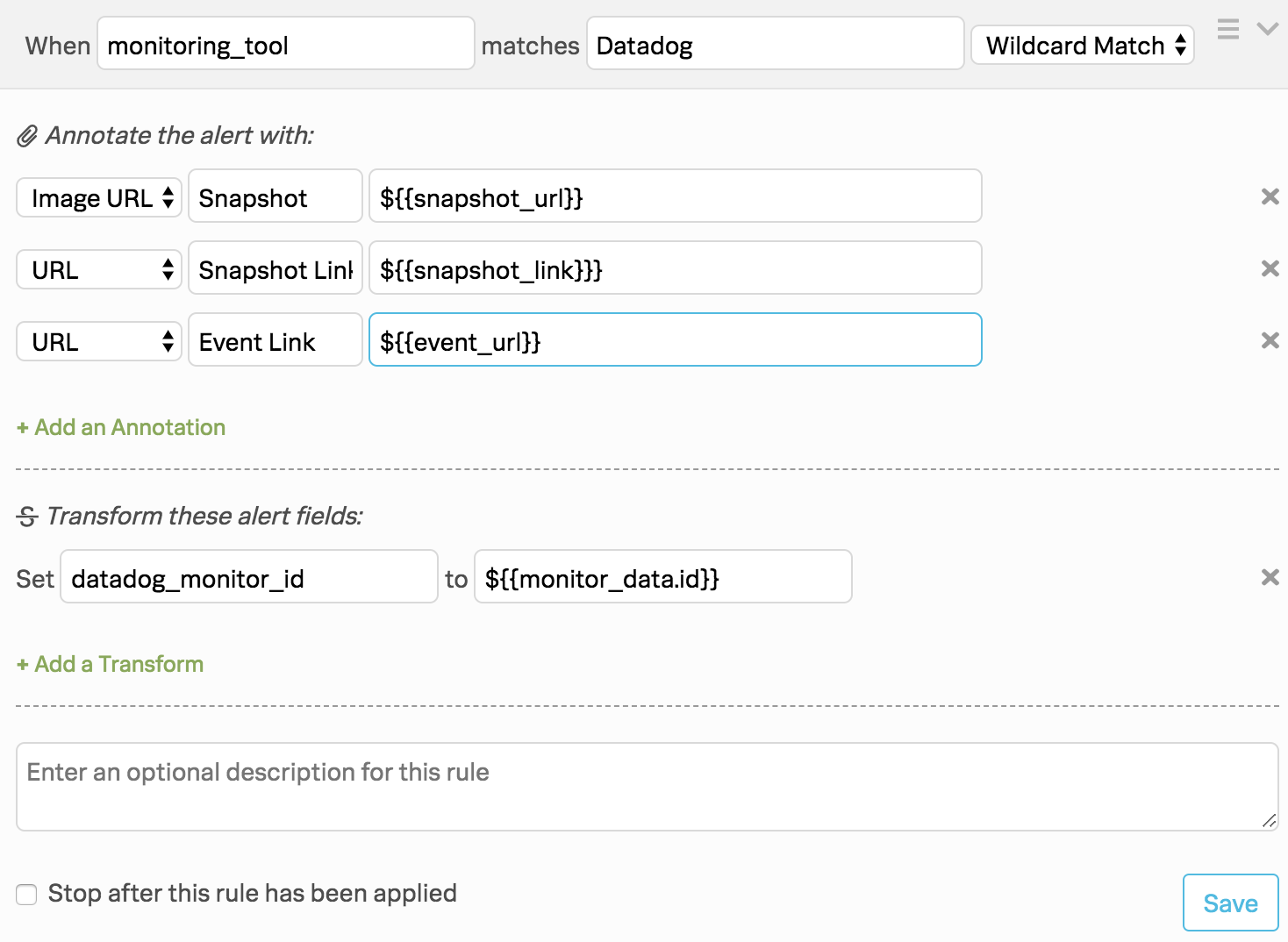
(オプション)追加のアラートルールエンジンのルール変換 🔗
Datadogのアラートには通常、スナップショット画像を自動的にレンダリングし、Datadogへのリンクを提供するために注釈をつけられるアラートへのリンクが含まれています。また、ルールエンジンの変換を追加することもできます:
monitoring_tool が Datadog と一致する場合
- Transform these alert fields で、以下の変換を設定します:
Image URL、Snapshot、${{snapshot_url}} の順に選択します。この変換により、Splunk On-Callタイムラインにスナップショット画像がレンダリングされます。
URL、Snapshot Link、${{snapshot_link}}} の順に選択します。この変換は、Datadogの画像へのリンクを提供します。
URL、Event Link、${{event_url}} の順に選択します。この変換は、Datadogのイベントへのリンクを提供します。