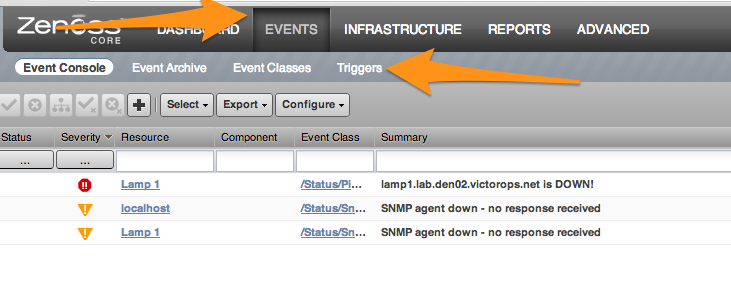
Splunk On-CallのZenossインテグレーション 🔗
Zenossはフリーでオープンソースのアプリケーション、サーバー、ネットワーク管理プラットフォームです。Splunk On-Call Zenossプラグインは、イベントトリガーや通知をキューに入れ、処理のためにSplunk On-Callサーバーに転送するスクリプトのセットです。通知のキューイングはZenossが通知コマンドを実行する際にインバンドで行われ、転送は長時間実行されるプロセスによってアウトオブバンドで行われます。
転送プロセスは、通知の送信を再試行することができ、送信に何らかの理由で長時間(デフォルトでは1分間)失敗した場合、設定されたアドレスへのメール送信にフォールバックします。
このパッケージはRPM、DEB、またはtarballとして提供されており、yumまたはapt-getを使用してSplunk On-Callをパッケージソースに追加することでインストールできます。
要件 🔗
このインテグレーションは以下のバージョンのSplunk On-Callと互換性があります:
Starter
Growth
エンタープライズ
このインテグレーションはZenoss 5.xのみをサポートしています。
サーバーにはPythonが必要で、これはZenossサーバーの要件でもあります。
サーバーにはcurlも必要です。
レイアウト 🔗
メインパッケージファイルは/opt/victorops/zenoss_pluginにインストールされます。
通知は/var/victorops/zenoss-alertsでキュー登録されます。
ログは/var/log/victoropsに書き込まれます。
Zenossのlibexec(/opt/zenoss/libexec)では、/opt/victorops/zenoss_plugin/binにあるいくつかのファイルに対してシンボリックリンクが作成されます。
インストール 🔗
注釈
お使いのシステムによっては、以下のコマンドの前に sudo を付加する必要がある可能性があります。
DEBパッケージ 🔗
wgetを使って.debパッケージをダウンロードします:
wget https://github.com/victorops/monitoring_tool_releases/releases/download/victorops-zenoss-0.22.44/victorops-zenoss_0.22.44_all.deb
ファイルを解凍する:
dpkg -i <path_to_file>
dpkgを使いたくない場合は、aptを使うこともできます。
sudo apt install <path_to_file>
RPMパッケージ 🔗
wgetを使って.rpmパッケージをダウンロードします:
wget https://github.com/victorops/monitoring_tool_releases/releases/download/victorops-zenoss-0.22.44/victorops-zenoss-0.22.44-1.noarch.rpmパッケージをインストールします:
rpm -i <path_to_file>
設定 🔗
DEBまたはRPMパッケージからインストールする場合、インストーラはプラグインファイルを/opt/victorops/zenoss_pluginに配置します。さらに、通知キューとログ用にそれぞれ/var/victorops/zenoss-alertsと/var/log/victoropsの2つのディレクトリが作成されます。
インストールしたら、/opt/victorops/zenoss_plugin/bin/configure.shスクリプトを実行してパッケージを設定する必要があります。設定スクリプトはZenossサーバーに接続します。これを使用するには、Zenoss管理者ユーザーIDとパスワードを提供する必要があります。スクリプトは両方の認証情報を取得するよう促します。
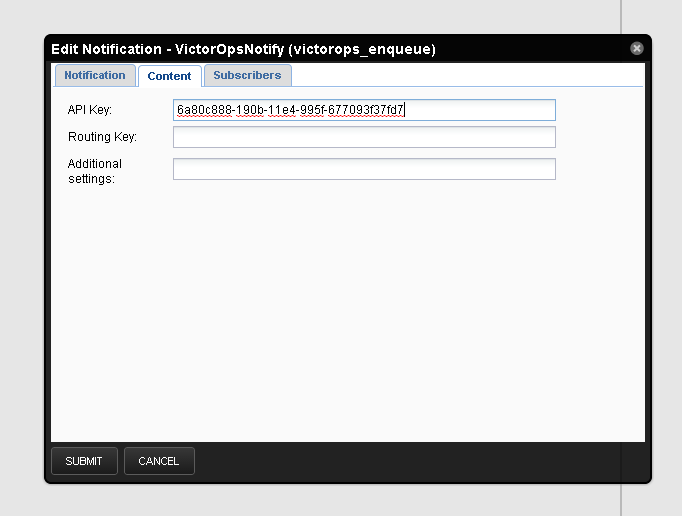
さらに、configure.shスクリプトに組織スラグとZenossアラートキーを指定する必要があります。これらはSplunk On-CallのZenossインテグレーションページに記載されています。Splunk On-Callへの通知送信に失敗した場合の予備連絡先としてメールアドレスを指定することもできます。そのためには、/opt/victorops/zenoss_plugin/conf/local.zenoss.confファイルを編集し、export FAILSAFE_EMAIL_TO の後にメールを追加します。
設定要素 🔗
configure.shスクリプトはZenossサーバーに接続し、Zenoss APIを使用して、通知をSplunk On-Callに転送するために必要ないくつかの要素を追加します。これらは以下のとおりです:
2つのZenossトリガー
コマンドとクリアコマンドの両方を含むZenoss通知
エスカレーションルーティング 🔗
Splunk On-Callに送信された通知によって作成されたインシデントは、デフォルトルートで処理されます。ルーティングを変更するには、VictorOpsNotify Notification の通知コマンドを変更し、Splunk On-Callのルーティングキーを VO_ROUTING_KEY= の後に記述します。
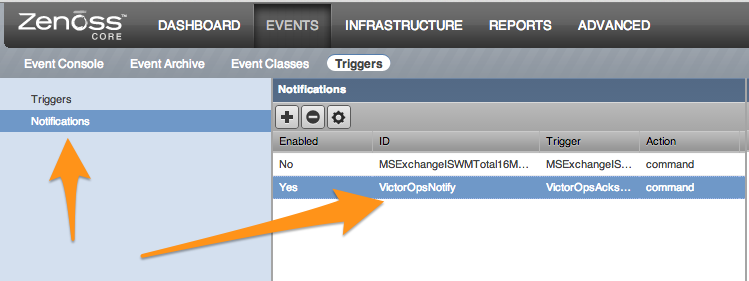
Content を選択し、VO_ROUTING_KEY= の後に希望のルーティングキーを入れます:
通知の処理方法 🔗
Splunk On-Callに通知するアクションは、通知の詳細をディスク上のファイルに保存します。数秒以内に、フォワーダープロセスが詳細をSplunk On-Callに送信し、そこで通常のアラート処理が実行されます。
詳細の転送が失敗した場合、詳細のタイムスタンプがチェックされ、詳細が古い場合(デフォルトでは1分)、代わりに設定時に指定したバックアップメールアドレスに詳細が送信されます。