Splunk On-CallのLogEntriesインテグレーション 🔗
Logentriesは、あらゆる規模でのリアルタイムのログ管理と分析を提供します。このインテグレーションにより、汎用メールエンドポイントを使用して、タグ付けされたLogentriesアラートをSplunk On-Callに送信できます。以下のガイドでは、このインテグレーションを実装するために必要な手順を説明します。
要件 🔗
このインテグレーションは以下のバージョンのSplunk On-Callと互換性があります:
Starter
Growth
エンタープライズ
Splunk On-Call 🔗
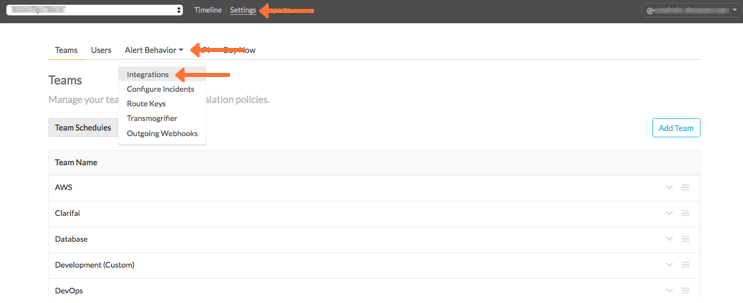
Splunk On-Callで、Settings、Alert Behavior、Integrations, :guilabel: LogEntries`を選択します。
インテグレーションがアクティブでない場合は、Enable Integration を選択してエンドポイントURLを生成します。URLをクリップボードにコピーし、$routing_key の部分を使用するルーティングキーに置き換えます。Splunk On-Callでルーティングキーを作成する を参照してください。
LogEntriesの設定 🔗
メインダッシュボードのメニューから Tags & Alerts を選択します。
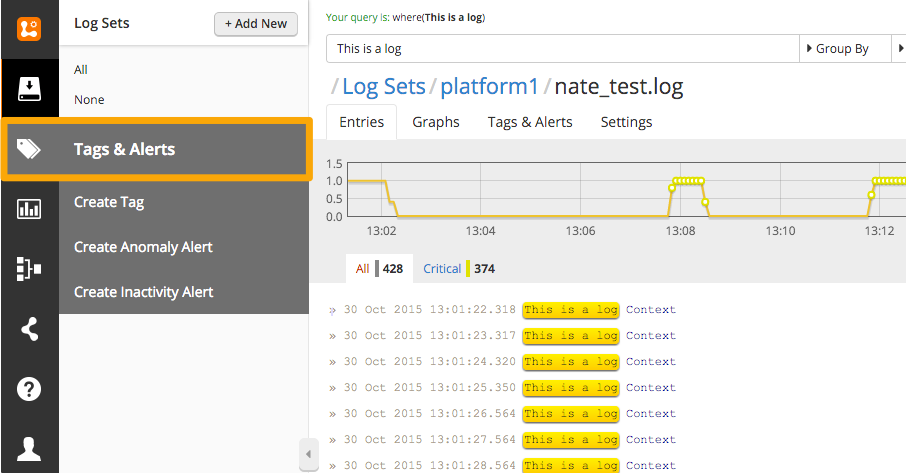
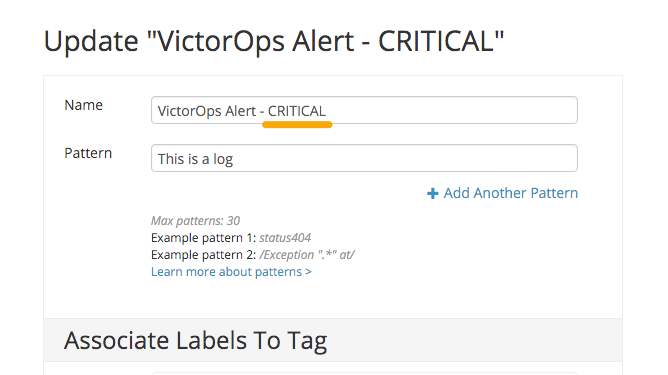
既存のタグを編集するか、新しいタグを作成します。タグに名前を付ける際には、そのアラートに必要なSplunk On-Callの重大度レベルを追加します。たとえば、warning という用語を追加するとSplunk On-Callの警告アラートが作成され、critical という用語を追加するとSplunk On-Callの重大インシデントが作成されます。
Splunk On-CallメールエンドポイントをLogentriesアラートタグによって通知されるメールアドレスに追加します。
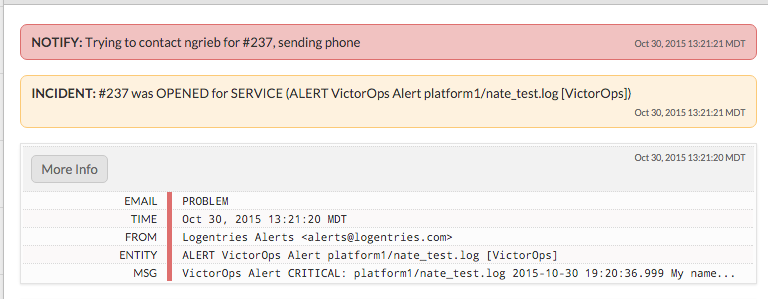
これで、検索が一致するたびに、関連する重大度レベルとともにアラートがSplunk On-Callタイムラインに送信されるようになりました。