Splunk On-CallのRESTエンドポイントインテグレーション 🔗
RESTエンドポイントを使用すると、カスタマイズしたアラートとインシデントの詳細をSplunk On-Callタイムラインに送信できます。アラートは、message_type、entity_id、state_message などのフィールドでSplunk On-Callのインシデントワークフローに送信されます。アラートがSplunk On-Callに送信されると、適切な担当者やチームにインシデントの詳細とともに直接ルーティングされ、オンコール対応者に詳細な背景情報を提供します。
Splunk On-Call RESTエンドポイントは、JSON形式のHTTPS POSTリクエストを使用して、あらゆるソースからのアラートを受け付けます。リクエストの内容さえ設定できれば、Splunk On-Callでインシデントのトリガー、確認、解決を行うことができます。
RESTエンドポイントインテグレーションを有効にする 🔗
Splunk On-Callで、Integrations、3rd Party Integrations、REST - Generic を選択します。
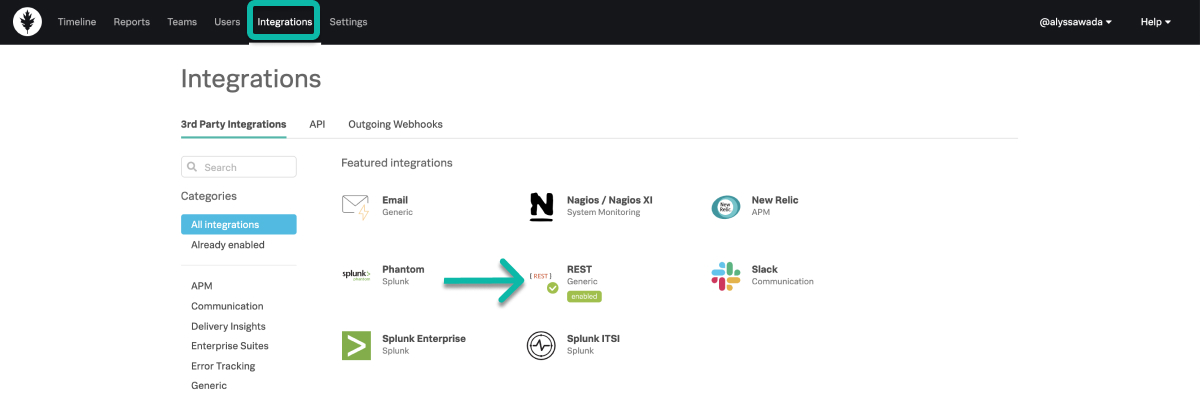
RESTエンドポイントインテグレーションが有効になっていない場合は、Enable を選択してエンドポイント先URLを生成します。
注釈
RESTエンドポイントは Splunk On-Call API とは異なり、インシデントを作成するのに適した方法です。
RESTエンドポイントインテグレーションルーティングキー 🔗
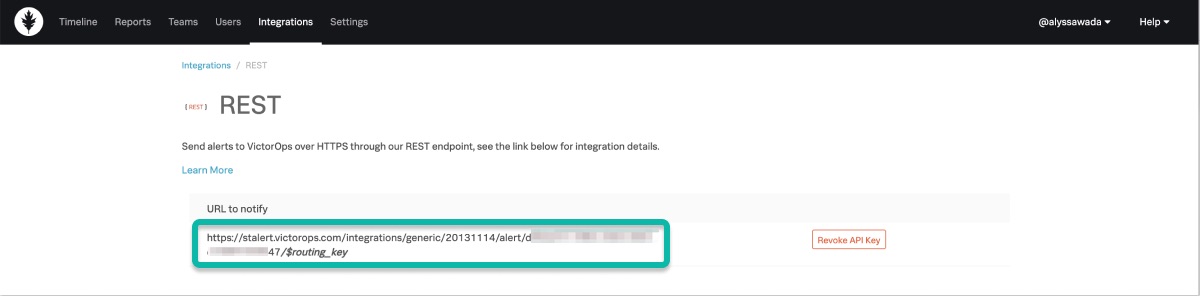
このインテグレーションに使用されるルーティングキーは、宛先URLに含まれています。最後のフォワードスラッシュ以降は、すべて自分のキーに置き換えてください。例えば、routing_keyの値が database であるとします:
...36437/$routing_key が ...36437/database になります
Splunk On-Callのルーティングキーの設定と関連付けは、Settings、Routing Keys を選択して行います。
ルーティングキーの詳細とベストプラクティスについては、Splunk On-Callでルーティングキーを作成する を参照してください。
推奨設定 🔗
必須なのは message_type だけですが、以下のフィールドはSplunk On-Calでのインシデントのワークフローとライフサイクルの確立に役立ちます。Splunk On-Callがサポートするさまざまなフィールドの詳細については、インシデントフィールド 用語集 を参照してください。
Setting |
Comment |
|---|---|
|
|
|
インシデントのID。このフィールドはインシデントのIDであり、インシデントのライフサイクルを通じて同じでなければなりません。インシデントのトリガー、確認、または解決時に同じ |
|
UIおよび通知での表示名。このフィールドを使用すると、ライフサイクルワークフローに影響を与えることなく、インシデントのサマリーをカスタムで、人にわかりやすく表示できます。 |
|
冗長なメッセージフィールド。このフィールドは文字数制限が高く、長い、冗長な、問題の説明を対象としています。このフィールドはいくつかの通知に含まれます:メールではフルコンテンツ、プッシュ、電話、またはSMS通知では文字制限とスペースが許す限り |
期待される反応 🔗
成功のメッセージには、結果とインシデントの entity_id が表示されます。例:
{ “result”:“success”, “entity_id”:“Your entity_id here” }
失敗メッセージには、結果と、失敗の理由を説明するエラーメッセージが表示されます。例:
{ “result”:“failure”, “message”:“Missing fields: message_type” }
アラート例 🔗
以下の例は、インテグレーションのいくつかの機能を示しています。
クリティカルインシデントをトリガーする 🔗
次のリクエストは新しいインシデントを開きます:
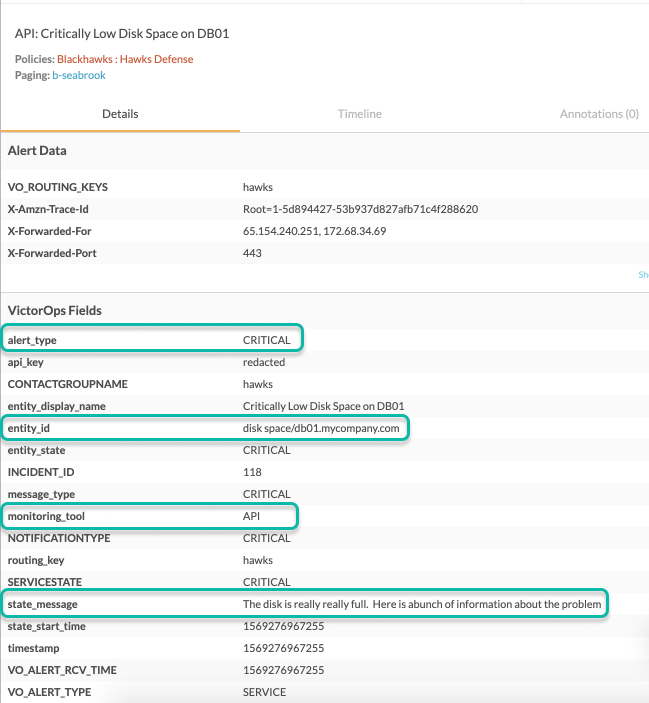
{ “message_type”:“CRITICAL”, “entity_id”:“disk
space/db01.mycompany.com”, “entity_display_name”:“Critically Low Disk
Space on DB01”, “state_message”:“The disk is really really full. Here is
abunch of information about the problem” }
対応は次のようになります:
{ “result” : “success”, “entity_id” : “disk space/db01.mycompany.com” }
Splunk On-Callでのインシデントの結果は以下のようになります:
インシデントを解決する 🔗
次のリクエストは、前の例で開かれた同じインシデントを解決します。entity_id が同じであることに注意してください。これによりSplunk On-Callは、このリクエストがどのインシデントに適用されるかを識別できます:
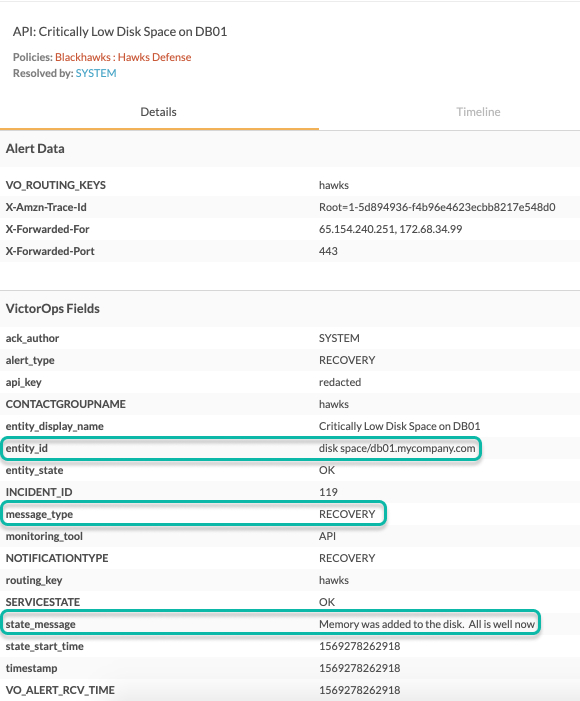
{ “message_type”:“RECOVERY”, “entity_id”:“disk
space/db01.mycompany.com”, “entity_display_name”:“Critically Low Disk
Space on DB01”, “state_message”:“Memory was added to the disk. All is
well now” }
対応は次のようになります:
{ “result” : “success”, “entity_id” : “disk space/db01.mycompany.com” }
Splunk On-Callでのインシデントの結果は以下のようになります:
cURLとインシデント対応 🔗
cURLコマンドを使ってエンドポイントを呼び出すこともできます。例:
curl -X POST -d ‘{“entity_id”:“ID of the
incident”,“message_type”:“critical”,“state_message”:“hi, this is some
state message.”}'
https://alert.victorops.com/integrations/generic/20131114/alert/[YOUR_REST_ENDPOINT_KEY]/[ROUTING_KEY_HERE]
注釈 🔗
アラートペイロードに注釈フィールドを追加することで、RESTエンドポイントを使用してSplunk On-Callに送信されるアラートに注釈を含めることができます。JSONペイロードに注釈フィールドを追加することで、INFO、WARNING、CRITICAL アラートに注釈を付けることができます。
インシデントが確認状態にあり、同じ entity_id を持つ新しいアラートがSplunk On-Call Timelineに入ってくると、そのアラートはオープンインシデントの下に集約されます。通知の集約 を参照してください。最新のアラートに含まれる新しい注釈は、インシデントの注釈タブに追加されます。注釈は各アラートペイロード内にも反映されます。
注釈ペイロード 🔗
Splunk On-Callが以下の構文で受け付ける注釈は3種類あります。注釈構文の最後に、注釈のタイトルをカスタマイズできます。たとえば、前のスクリーンショットでは、URL注釈のタイトルはSplunk On-Callでは Runbook と表示されます。
URL: *vo_annotate.u.url*
{ “monitoring_tool”: “API”, “message_type”:“INFO”,
“entity_id”:“disk.space/db01”, “entity_display_name”:“Approaching Low
Disk Space on DB01”, “state_message”:“The disk is really really full.
Here is a bunch of information about the problem”,
“vo_annotate.u.Runbook”:“https://help.Splunk On-Call.com/knowledge-base/rest-endpoint-integration-guide/”
}
Note: *vo_annotate.s.note*
{ “monitoring_tool”: “API”, “message_type”:“INFO”,
“entity_id”:“disk.space/db01”, “entity_display_name”:“Approaching Low
Disk Space on DB01”, “state_message”:“The disk is really really full.
Here is a bunch of information about the problem”,
“vo_annotate.s.Note”:“Once Disk Space is critically low there will be an
incident!” }
注釈
注釈には1,124文字の制限があります。
Image URL: *vo_annotate.i.image*
{ “monitoring_tool”: “API”, “message_type”:“INFO”,
“entity_id”:“disk.space/db01”, “entity_display_name”:“Approaching Low
Disk Space on DB01”, “state_message”:“The disk is really really full.
Here is a bunch of information about the problem”,
“vo_annotate.i.Graph”:“https://community.iotawatt.com/uploads/db6340/original/1X/266a3917cc86317830ae9cda3e91c7689a6c73a7.png”
}