Splunk On-CallのGrafanaインテグレーション 🔗
Splunk On-Call Grafanaインテグレーションを使用して、GrafanaアラートとダッシュボードをSplunk On-Callに転送し、適切なオンコールユーザーに通知します。Splunk On-Callでオンコール・スケジュール、ローテーション、エスカレーションポリシーを作成し、それらのパラメータに基づいてGrafanaアラートとチャートをルーティングします。Grafanaでログ、メトリクス、トレースを監視および可視化し、しきい値を設定してアラートを最適化し、チャートを作成し、実用的なシステムインサイトを表示します。
イベントが所定の監視基準を満たすと、Grafanaはアラート通知を送信します。その後、Splunk On-Callのタイムラインで、ユーザーは重要なアラートデータをルーティングし、適切な担当者にエスカレーションすることができます。Splunk On-CallとGrafanaのインテグレーションにより、オンコール対応者はシステムデータを中心にリアルタイムで協力し、平均確認時間(MTTA)と平均修復時間(MTTR)を短縮し、インシデントを迅速に解決することができます。
Splunk On-Call Grafamaのインテグレーションにより、チームは以下のことが可能になります:
システムパフォーマンスを長期的に追跡し、サービスの健全性を可視化し、該当する監視しきい値に達するとオンコールチームにアラートを発します。
メトリクス、ログ、グラフ、ランブックへのリンクの形でアラートコンテキストを表示します。
GrafanaアラートデータをSplunk On-Callソフトウェアで自動的にルーティングおよびエスカレーションし、単一の画面で協力してインシデントワークフローを推進します
インシデントの状況に合わせてチャットを行うことで、コラボレーションを改善し、重要なインフラ情報とダッシュボードを迅速に共有して、MTTAとMTTRを削減します。
Splunk On-CallでGrafanaを有効化する 🔗
メインのタイムラインから、Integrations、Grafana の順に移動します。
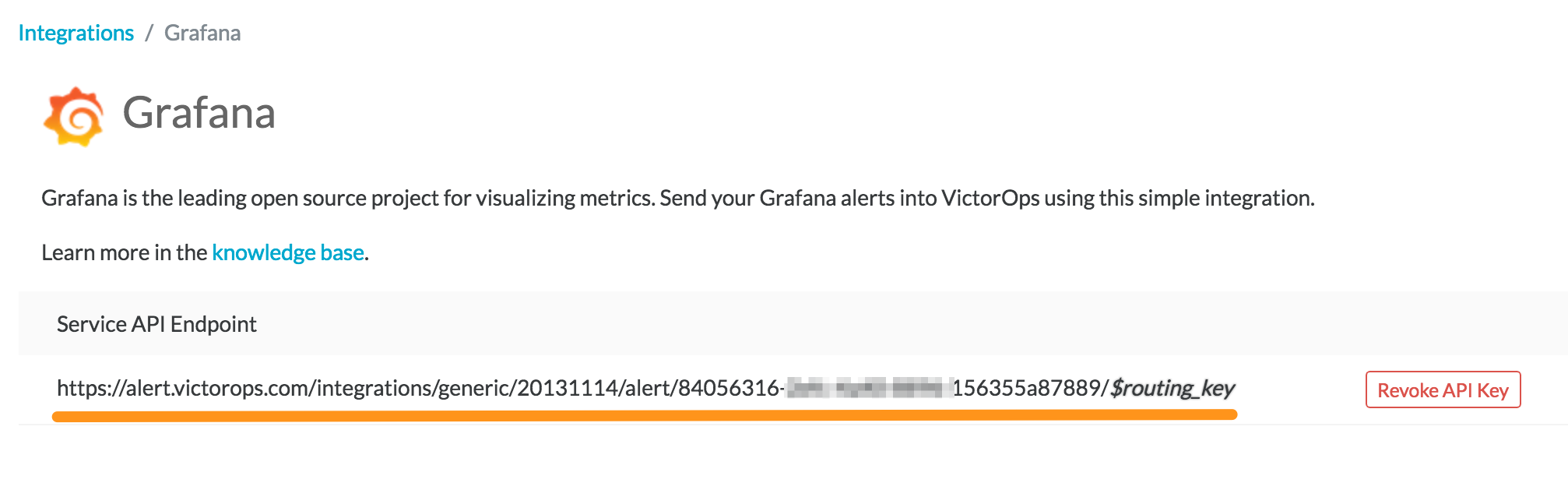
Grafanaインテグレーションを選択し、後で使用するために Service API Endpoint をコピーします。
GrafanaでSplunk On-Callを接続する 🔗
メインダッシュボードから、オプションメニューを選択し、次に Alerting、Notification Channels の順に選択します。
新しいチャネルを追加します。
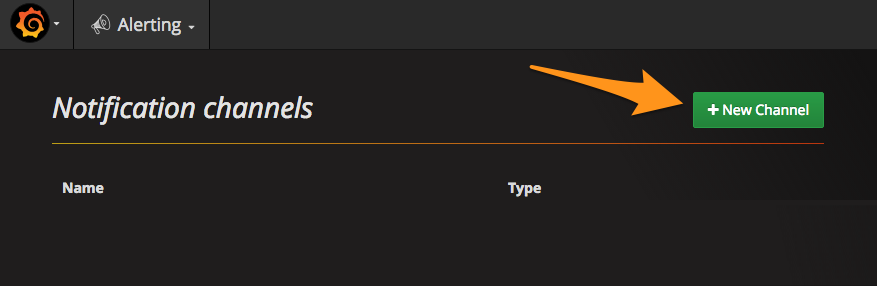
通知に名前を付け、VictorOps タイプを選択します。
VictorOpsの設定で Service API Endpoint を貼り付けます。
$routing_keyを使用するルーティングキーに置き換えてください。ルーティングキーの詳細については、Splunk On-Callでルーティングキーを作成する を参照してください。インテグレーションを保存します。
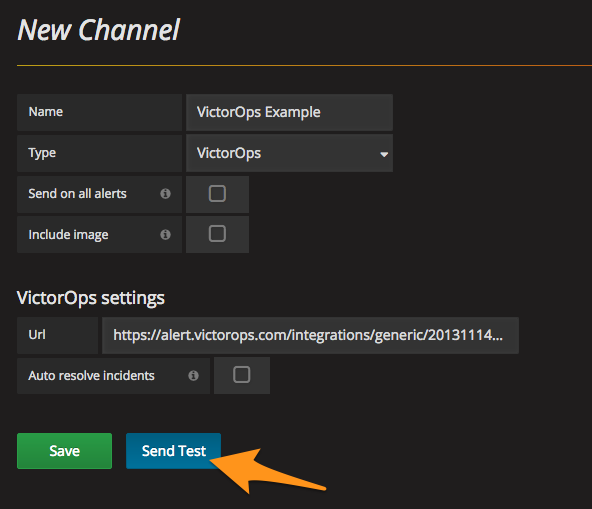
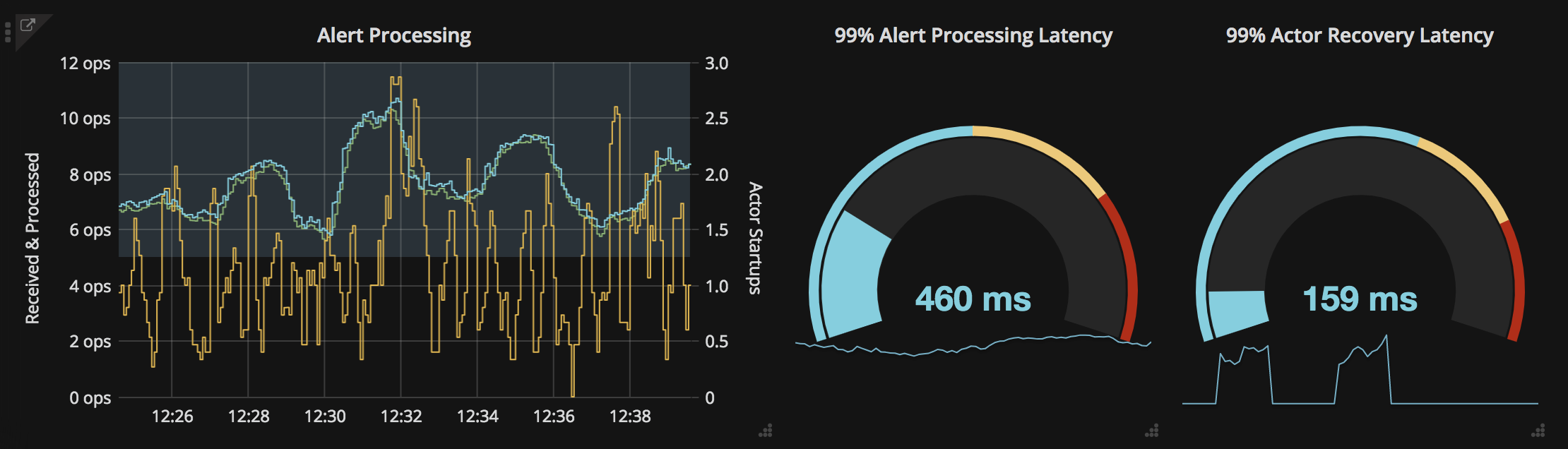
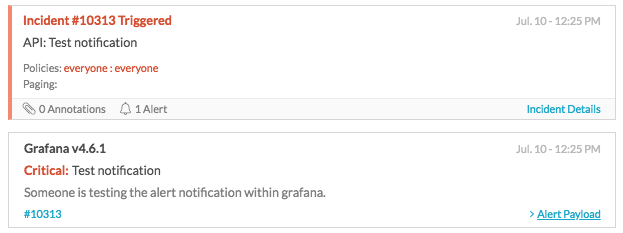
Splunk On-Callのテストアラートの結果は以下のようになります:
通知チャネルをアラートに接続する 🔗
Splunk On-Callにアラートを送信したいGrafanaダッシュボードパネルを探し、パネル名の横にあるドロップダウン矢印で Edit を選択します。
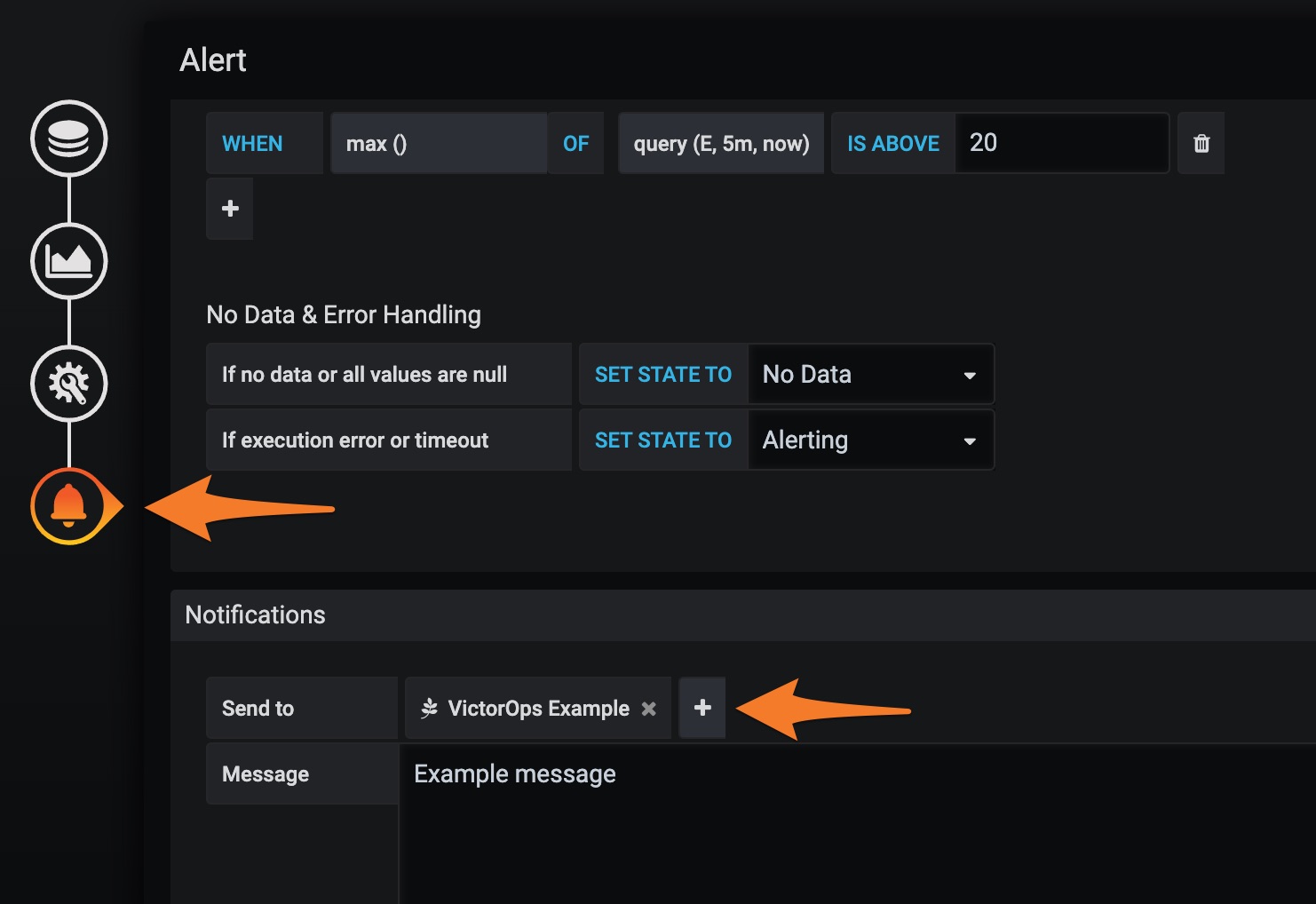
Alert セクションに移動します。
アラート条件を定義します。
Notifications で、プラスボタンを選択し、設定した通知チャネルを選択します。
変更を保存します。
これで標準設定は完了です。必要に応じてこれらの手順を繰り返し、ルーティングキーごとに別々の通知チャネルを作成します。
アラートに画像を含める 🔗
エンタープライズSplunk On-Call機能を使用している場合は、アラートのGrafana画像を通知に含めることができます。
Grafanaで通知チャネルを設定する場合は、Include image を選択します。
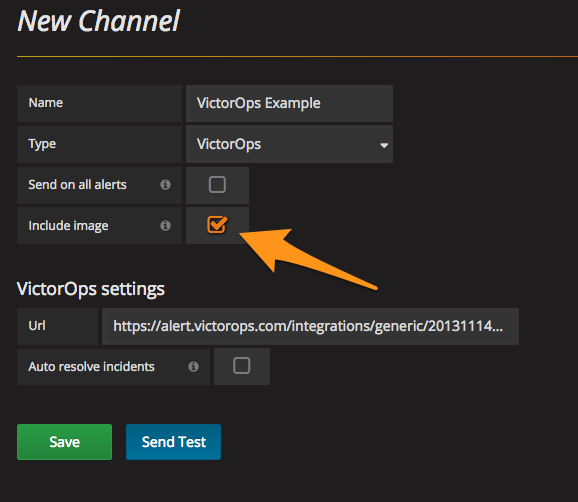
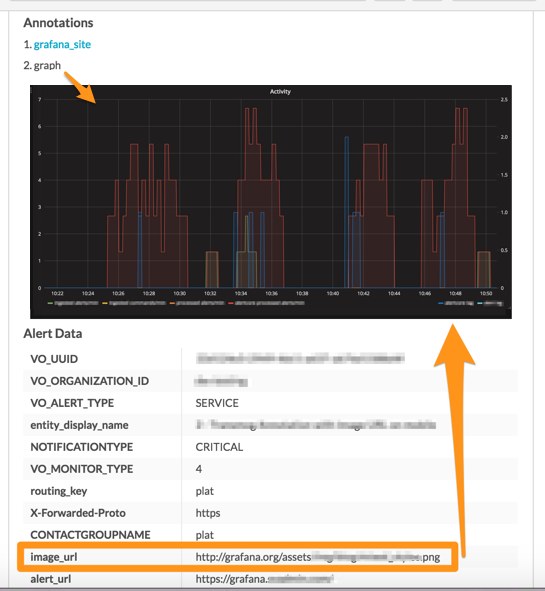
Splunk On-Callで、Settings、Alert Rules Engine と進み、以下のルールエンジンルールを追加して、image_urlをインシデントの注釈として表示します。Splunk On-Callが表示できるように、画像が一般にアクセス可能な場所にホストされていることを確認します。詳細については、Grafanaドキュメントの Use images in notifications を参照してください。
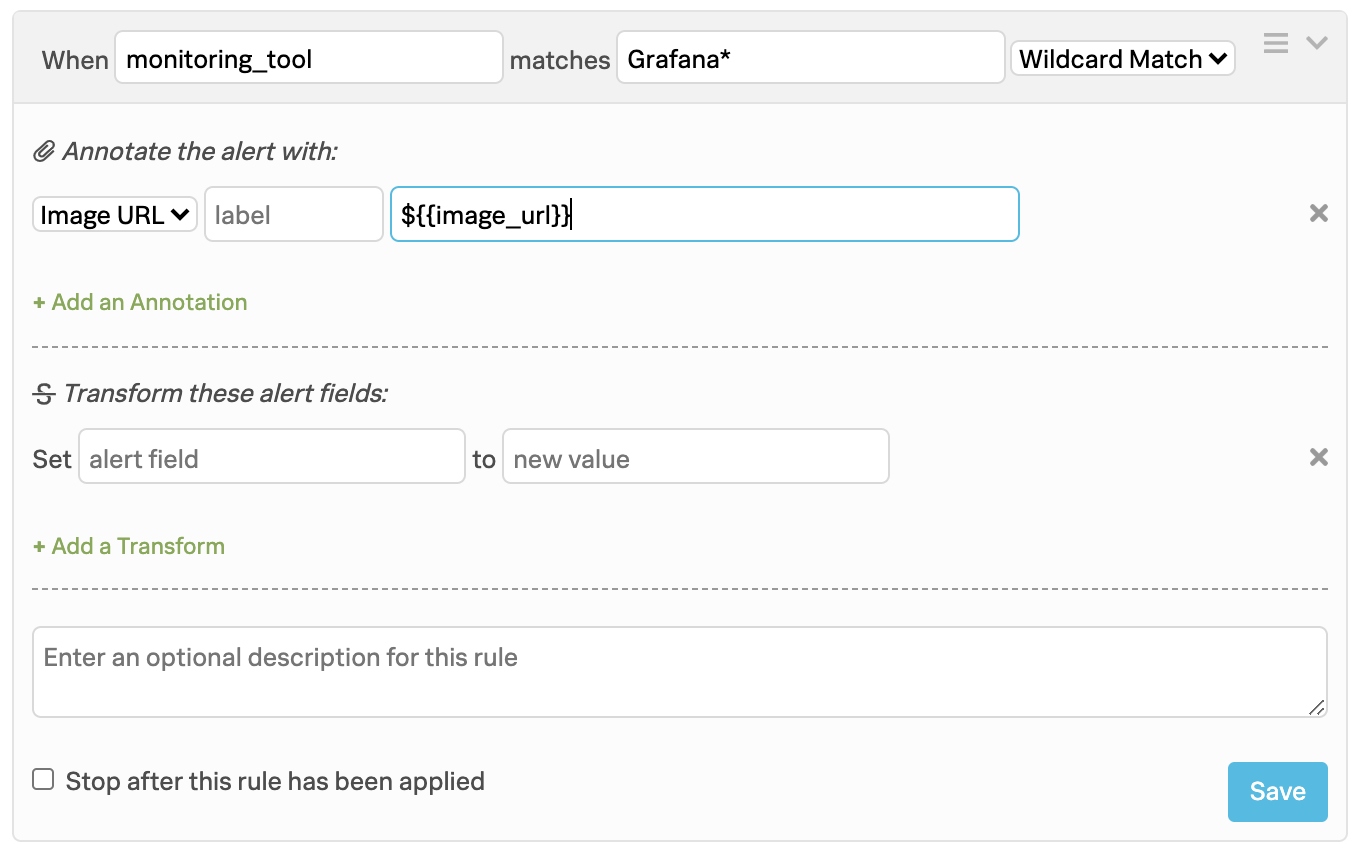
これでSplunk On-Callインシデントに画像が注釈として含まれるようになりました: