Microsoft Teams用Splunk>VictorOpsアプリ 🔗
Microsoft TeamsでSplunk>VictorOpsアプリを使用して、選択したツールから重要なインシデントを処理します。このアプリケーションは双方向なので、インシデントのペイロード全体を確認し、インシデントを認識して解決することができます。Splunk On-CallはMicrosoft Teamsユーザーをマッピングするため、すべてのレポートが正確で、情報が失われることはありません。
要件 🔗
エンタープライズレベルのSplunk On-Callアカウントとグローバル管理者アクセス許可
Microsoft Teams組織の管理者アクセス許可
アプリをインストールするチームのMicrosoft Teamsチームオーナー
アプリが動作する仕組み 🔗
Splunk On-Callは、すべての単一または複数対応者のインシデントを、サブスクライブされた Microsoft Teamsチャネルにルーティングします。
インシデント管理用の新しいカードがMicrosoft Teamsチャネルに作成されます。インシデントカードは、インシデントイベントが発生すると更新されます。
Microsoft Teamsユーザーは、Splunk>VictorOpsアプリまたはMicrosoft Teamsのいずれかから、インシデントに対してスヌーズ、再ルーティング、確認、対応者の追加、解決などのインシデント管理アクションを実行できます。
アプリをインストールする 🔗
Microsoft StoreからSplunk>VictorOpsアプリをダウンロードし、アプリアイコンを選択してインストールプロセスを開始します。
Add to a team を選択し、Splunk>VictorOpsアプリのチャネルを選択します。チーム内の特定のチャネルにSplunk>VictorOpsアプリをインストールすると、そのチーム内のすべてのチャネルでSplunk>VictorOpsアプリが使用可能になります。
Set up a bot を選択して、アプリをチームに追加し、設定プロセスを開始します。
インストールプロセスを再度実行して、追加のチームからチャネルを選択し、Splunk>VictorOpsアプリへのアクセスを拡大することができます。
アプリを設定する 🔗
アプリの設定を始める前に、アプリを設定するための前提条件を満たしていることを確認してください。
前提条件 🔗
Microsoft Teamsの組織管理者およびチームオーナーとしてログインする必要があります。
また、Microsoft Teams組織管理者と同じメールアドレスを使用するSplunk On-Callアカウントが必要です。
アプリをインストールし、チームに追加したら、アプリを設定する必要があります。
Splunk>VictorOpsアプリをチームに追加すると、そのチームの全般チャネルに Welcome to VictorOps カードが表示されます。ボットコマンド
@Splunk VictorOps configureを実行して、チャネルに新しいカードを生成することもできます。Configure を選択します。
Add Configuration を選択します。
Splunk On-Call組織API IDとAPIキーを入力します。
Allow application to access MS Teams account details を選択します。
Microsoft Teamsからプロンプトが表示されたら、管理者認証情報を入力します。
Accept を選択し、同意します。
Save を選択して設定を完了します。
注釈
Microsoft Teamsが同意を登録するまでに、10秒ほどかかる場合があります。接続できないエラーが表示された場合は、10秒後にもう一度お試しください。問題が解決しない場合は、サポートにお問い合わせください。
チャネルをマップする 🔗
次に、Microsoft Teamsインスタンス内のチャネルへのマッピングを定義する必要があります。これは、Splunk On-Callチーム全体をデフォルトチャネルにマッピングするか、特定のSplunk On-Callエスカレーションポリシーをマッピングすることで行うことができます。
まず、Microsoft Teamsのチームオーナーは、アプリがインストールされているチャネルで
@Splunk VictorOps mapchannelコマンドを実行できます。表示されるカードで、Map Channel を選択します。
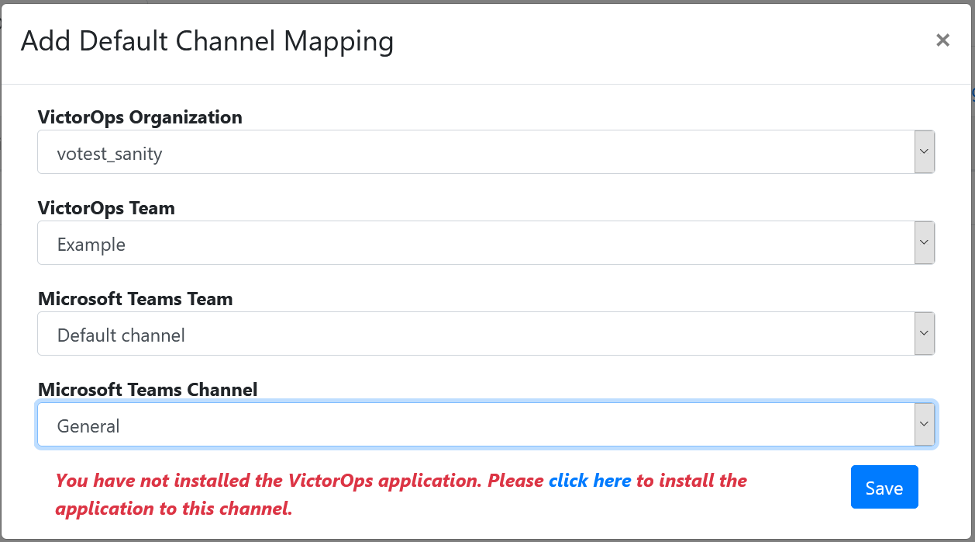
Add Mapping を選択し、Add Default Channel Mapping ダイアログボックスを開きます。
VictorOps Organization で設定済みの接続を選択します。
VictorOps Team を選択します。
Microsoft Teams Team を選択します。
Microsoft Teams Channel を選択します。
Save を選択します。
マッピングがデフォルトマッピング表に表示されます。
選択したMicrosoft TeamsチームにSplunk>VictorOpsアプリケーションがインストールされていない場合、アプリをインストールするオプションが付いた警告が表示されます。アプリをインストールし、Save を選択します。
エスカレーションポリシーのマッピング 🔗
Escalation Policy Mapping タブを選択します。
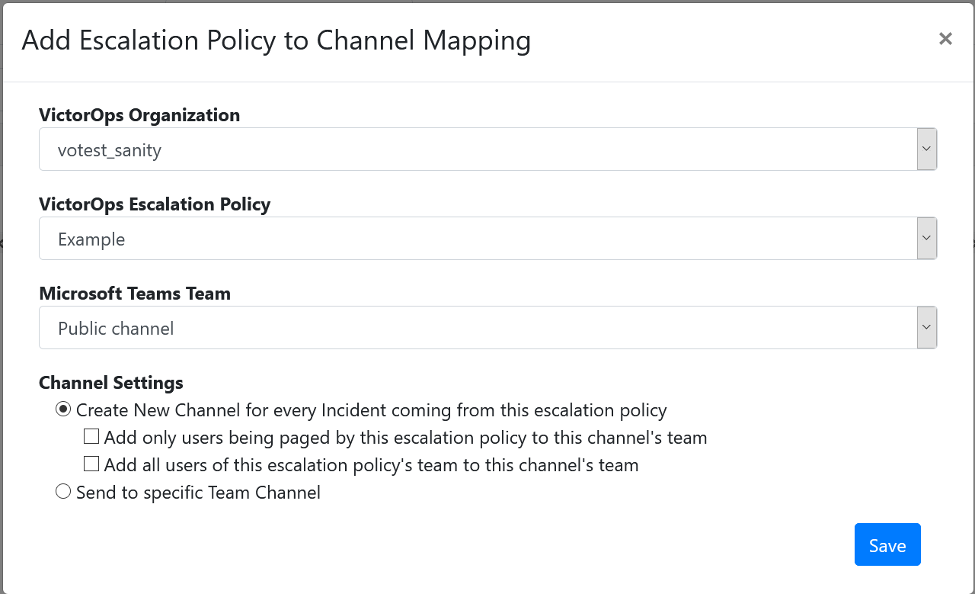
Add Mapping を選択し、Add Escalation Policy to Channel Mapping ダイアログボックスを開きます。
VictorOps Organization で設定済みの接続を選択します。
VictorOps Escalation Policy エスカレーションポリシーは、Splunk On-Callチーム内でアルファベット順に表示されます。
Microsoft Teams Team を選択します。
- Channel Settings を選択します。選択したチーム内の既存のチャネルに新しいインシデントをマップすることも、新しいインシデントごとにそのチーム内に新しいチャネルを作成することもできます。新しいチャネルを作成するオプションを選択した場合は、次のいずれかを実行できます:
エスカレーションによってページングされるSplunk On-Callユーザーのみを、チャネルに関連付けられたMicrosoft Teamsチームに追加します。このオプションは、設定されたVictorOps組織で対応するアカウントを持つMicrosoft Teamsメンバーに対してのみ機能し、メールアドレスでマッチングされます。
エスカレーションポリシー内のすべてのSplunk On-Callユーザーを、チャネルに関連付けられたMicrosoft Teamsチームに追加します。このオプションは、設定されたVictorOps組織で対応するアカウントを持つMicrosoft Teamsメンバーに対してのみ機能します。
最後に、これらのオプションを選択しないままにしておけば、すべてのユーザーをそのままにしておくことができます。
Save を選択します。
マッピングがエスカレーションポリシーマッピングテーブルに表示されます。
選択したMicrosoft TeamsチームにSplunk>VictorOpsアプリケーションがインストールされていない場合、アプリをインストールするオプションが付いた警告が表示されます。アプリをインストールし、Save を選択します。
Splunk>VictorOpsボットコマンド 🔗
アプリがインストールされている任意のチャネルで @Splunk VictorOps を実行することでSplunk>VictorOps botを呼び出すことができます。利用可能なコマンドは以下のとおりです:
help:ボットコマンドのリストを表示するにはhelpコマンドを使用します。configure: 現在のチャネルでアプリを設定するにはconfigureコマンドを使用します。このコマンドを使って接続を編集することもできます。mapchannel: mapchannelコマンドを使用して、デフォルトとエスカレーションポリシーのチャネルマッピングを作成します。createincident: createincidentコマンドを使用して、指定されたインシデントの説明、本文、および承認動作で、選択したエスカレーションポリシーまたはユーザーに警告するインシデントを作成します。
アプリをアンインストールする 🔗
Microsoft Teamsの組織レベルまたはチームレベルでSplunk>VictorOpsアプリをアンインストールできます。Microsoft Teams組織管理者は、どちらのレベルでもアンインストールの権限があります。Microsoft Teamsのチームオーナーは、自分のチームの設定のみを管理できます。チームオーナーが持つ権限はさまざまで、Splunk>VictorOpsアプリをアンインストールするには不十分な場合があります。
チームレベルでアンインストールする 🔗
チームレベルでアンインストールすると、自動的に登録が解除され、そのチーム内のすべてのチャネルからSplunk>VictorOpsアプリが削除されます。
サイドバーで Teams を選択します。
More options… を選択します。
Manage team を選択します。
Apps タブで、Splunk>VictorOpsの隣にある Uninstall を選択します。
Uninstall を選択して確定します。
組織レベルでアンインストールする 🔗
組織レベルでアンインストールすると、その組織内のすべてのチームからSplunk>VictorOpsアプリが自動的に削除されます。
サイドバーで Apps を選択します。
Splunk>VictorOps メニューを選択します。
Delete を選択します。
I understand the app will be deleted for all users を選択します。
Delete app を選択して確定します。
注意
組織レベルでSplunk>VictorOpsをアンインストールしても、チャネルは配信停止されません。回避策として、組織レベルでアンインストールする前にチームレベルでアンインストールしてください。
Splunk>VictorOpsアプリに必要な MS Teamsのアクセス許可 🔗
Splunk>VictorOpsアプリには以下のMS Teamsのアクセス許可が必要です:
Teamsアプリが全チームを管理するのを許可する
すべてのチームのTeamsアプリを管理する
すべてのチームにインストールされたTeamsアプリを読み込む
チャネルを作成する
すべてのグループメンバーシップの読み込みおよび書き込み
すべてのグループメンバーシップを読み込む
ディレクトリデータの読み込みおよび書き込み
ディレクトリデータを読み込む
全グループの読み込みおよび書き込み
すべてのグループを読み込む
全ユーザーのプロファイルを読み込む
全ユーザーの完全なプロファイルの読み込みおよび書き込み
サインインしてユーザープロファイルを読み込む