Splunk On-CallのLogicMonitorインテグレーション 🔗
LogicMonitorは、複数の監視ソリューションを置き換えます。サーバー(物理、仮想、クラウドベース)、アプリケーション(Web、メール、データベース、仮想化)、ネットワーク機器、ストレージアレイ、ロードバランサー、UPSなど、データセンター内のすべてを単一のWebポータルで監視します。Splunk On-CallとLogicMonitorのインテグレーションはREST APIを使用し、インフラストラクチャにLogicMonitorを実装している必要があります。
要件 🔗
このインテグレーションは以下のバージョンのSplunk On-Callと互換性があります:
Starter
Growth
エンタープライズ
注釈
インシデントが正しく解決されていることを確認するには、件名の「クリティカル」および「解決済み」に静的フィールドを選択します。
Splunk On-Callの設定 🔗
Splunk On-Callで、Settings、Alert Behavior、Integrations、LogicMonitor を選択します。
インテグレーションがアクティブでない場合は、Enable Integration を選択してエンドポイントURLを生成します。$routing_key セクションを使用したいルーティングキーに置き換えてください。
ロジックモニターの設定 🔗
メインダッシュボードから Settings、Integrations を選択し、Add を選択します。
ダイアログで、Custom HTTP Delivery を選択します。
以下の値を記入します:
名前:Splunk On-Call
説明:Splunk On-Callにアラート情報を送信する
Use different URLs or data formats to notify on various alert activity を選択します。
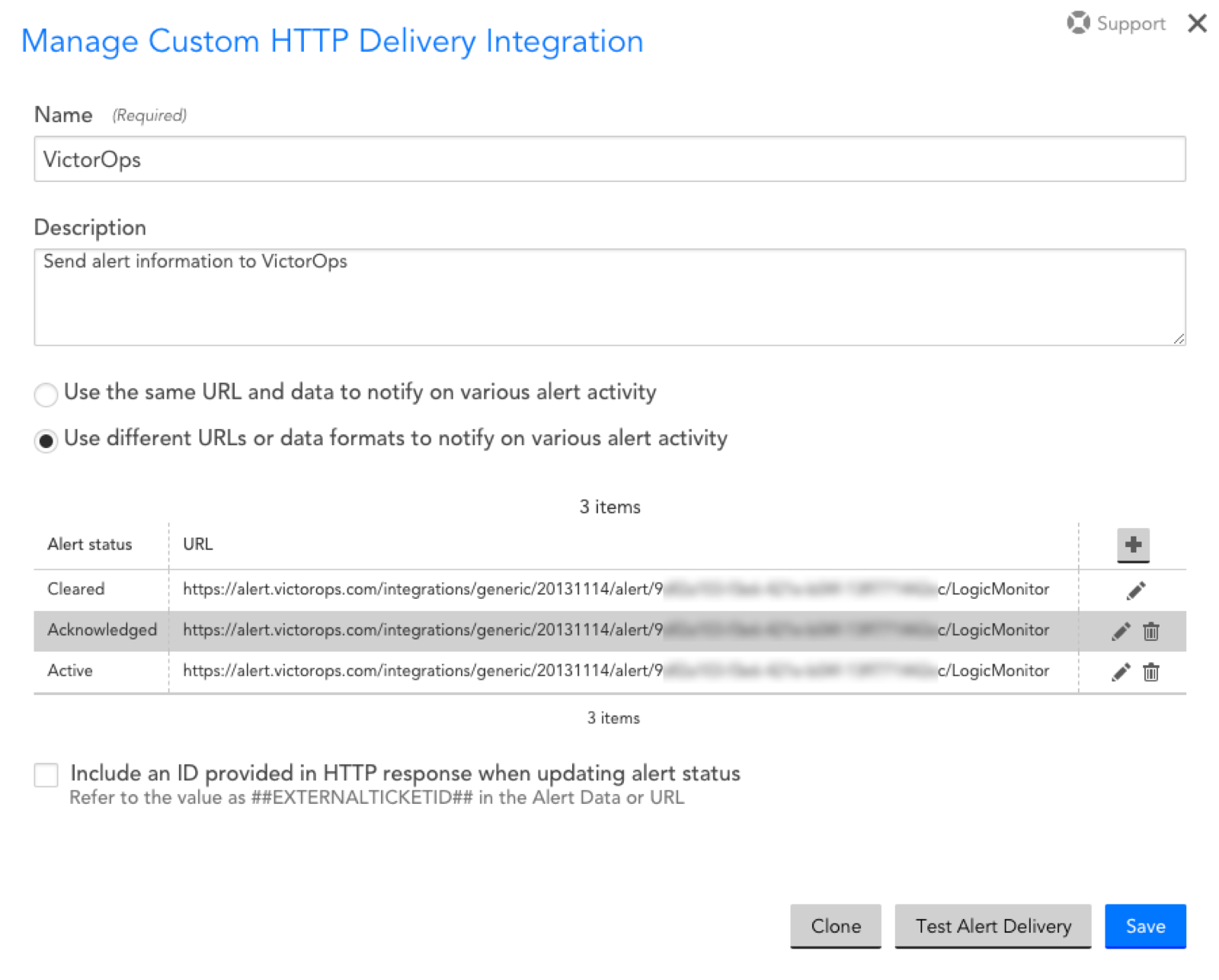
各アラートアクティビティ用にアラートメソッドを作成します。アラートアクティビティと、投稿本文で定義された対応するメッセージタイプという2つの設定を除いて、ほとんどの設定は同じです。これを行うには、アラートステータスのタイプごとに別々の設定を作成します。
HTTPメソッド: HTTP POST
URL:
https://alert.victorops.com/integrations/generic/20131114/alert/YOUR_API_KEY_HERE/YOUR_ROUTING_KEY_HEREアラートデータ:
Raw` を選択する
形式: JSON
アラートデータには以下のメッセージを貼り付けます。このサンプルでは、
message_typeにCRITICALという値を割り当てていることに注意してください:{ “message_type”:“CRITICAL”, “state_message”:“##MESSAGE##”, “entity_id”:“##ALERTID##”, “monitoring_tool”:“LogicMonitor”, “entity_display_name”:“##LEVEL## alert on ##HOST##”, “GROUP”:“##GROUP##”, “START”:“##START##”, “DESCRIPTION”:“##SERVICEDESCRIPTION##”, “SERVICE_CHECKPOINT”:“##CHECKPOINT##”, “SERVICE_GROUP”:“##SERVICEGROUP##”, “CLIENT_URL”:“https://##COMPANY##.logicmonitor.com”, “ALERT_URL”:“##AlertDetailURL##”, “ADMIN”:“##ADMIN##”, “ALERTID”:“##ALERTID##”, “ALERTTYPE”:“##ALERTTYPE##”, “ALERTSTATUS”:“##ALERTSTATUS##”, “CMDLINE”:“##CMDLINE##”, “DATAPOINT”:“##DATAPOINT##”, “DATASOURCE”:“##DATASOURCE##”, “DPDESCRIPTION”:“##DPDESCRIPTION##”, “DSIDESCRIPTION”:“##DSIDESCRIPTION##”, “DURATION”:“##DURATION##”, “EVENTCODE”:“##EVENTCODE##”, “EXITCODE”:“##EXITCODE##”, “FACILITY”:“##FACILITY##”, “GENERALCODE”:“##GENERALCODE##”, “HOST”:“##HOST##”, “INSTANCE”:“##INSTANCE##”, “LEVEL”:“##LEVEL##”, “LOGFILE”:“##LOGFILE##”, “MESSAGE”:“##MESSAGE##”, “SOURCENAME”:“##SOURCENAME##”, “SPECIFICCODE”:“##SPECIFICCODE##”, “STARTEPOCH”:“##STARTEPOCH##”, “STDERR”:“##STDERR##”, “STDOUT”:“##STDOUT##”, “THRESHOLD”:“##THRESHOLD##”, “TRAPOID”:“##TRAPOID##”, “TYPE”:“##TYPE##”, “VALUE”:“##VALUE##” }
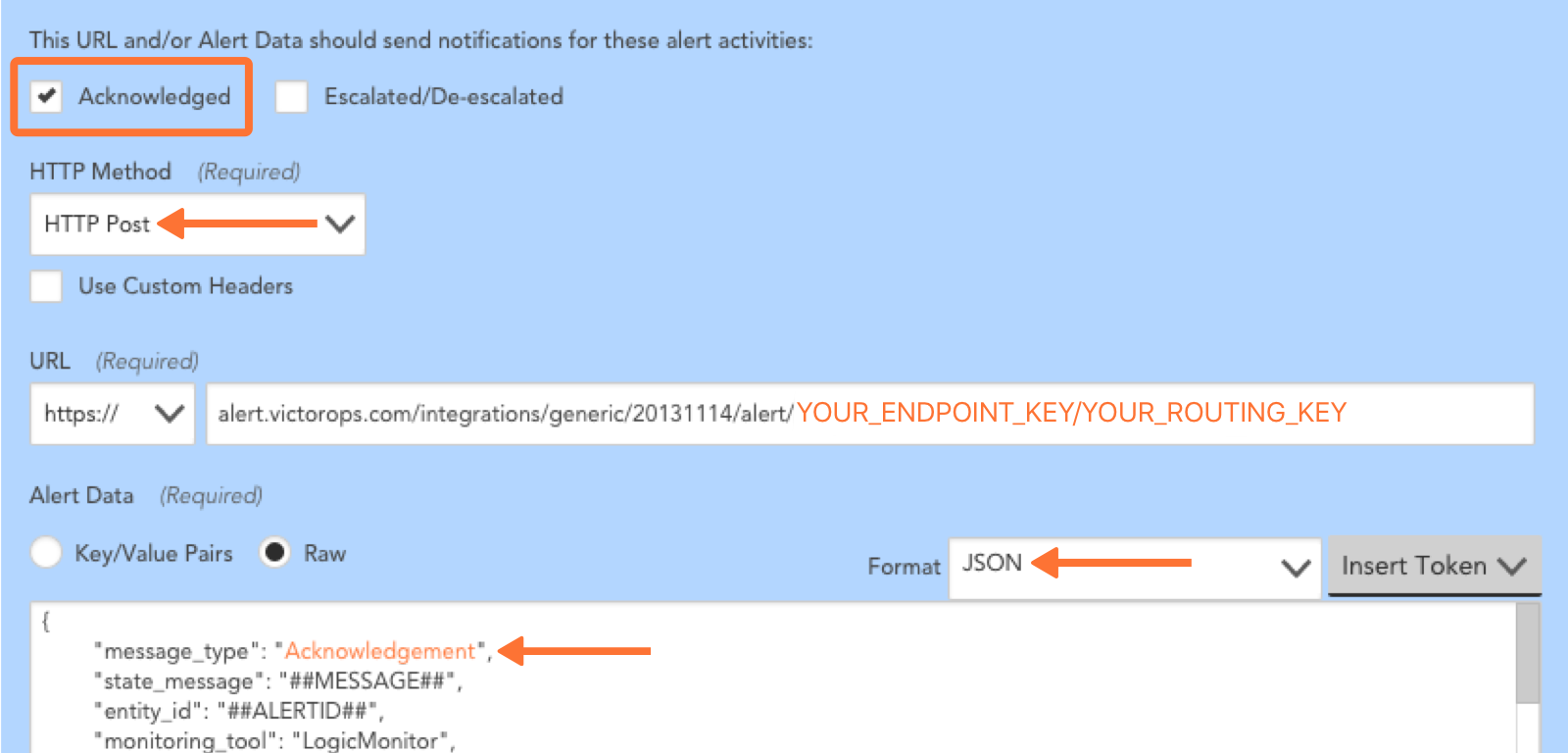
アラートステータスが「確認(Acknowledged)」の場合、および「クリア(Cleared)」の場合、ステップ1から4を繰り返す。それぞれについて、アラートデータ内の message_type フィールドをアラートステータスを反映するように変更します。以下のようにフィールドをマッピングし、明確化するためにスクリーンショットを参照してください:
アラートに注釈を追加する 🔗
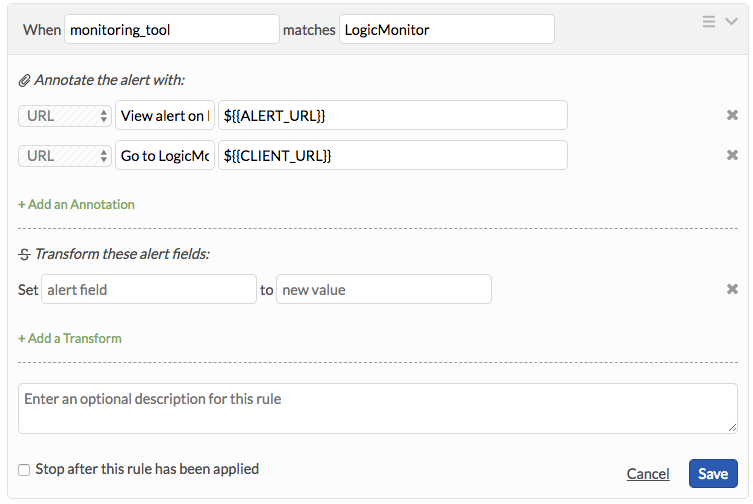
前の設定を使用すると、アラートURLとクライアントURLがフィールドとして送信されます。これらのフィールドをアクセス性の高い注釈として表示するには、以下のルールエンジンルールを実装します。
monitoring_toolがLogicMonitorと一致する場合。
アラートに次の注釈をつけます:
URL、LogicMonitorでのアラートの表示、
${{ALERT_URL}}URL、LogicMonitorへ移動、
${{CLIENT_URL}}
保存後、インシデントカードとアラートカードに両方のURLへの直接リンクが表示されます。
