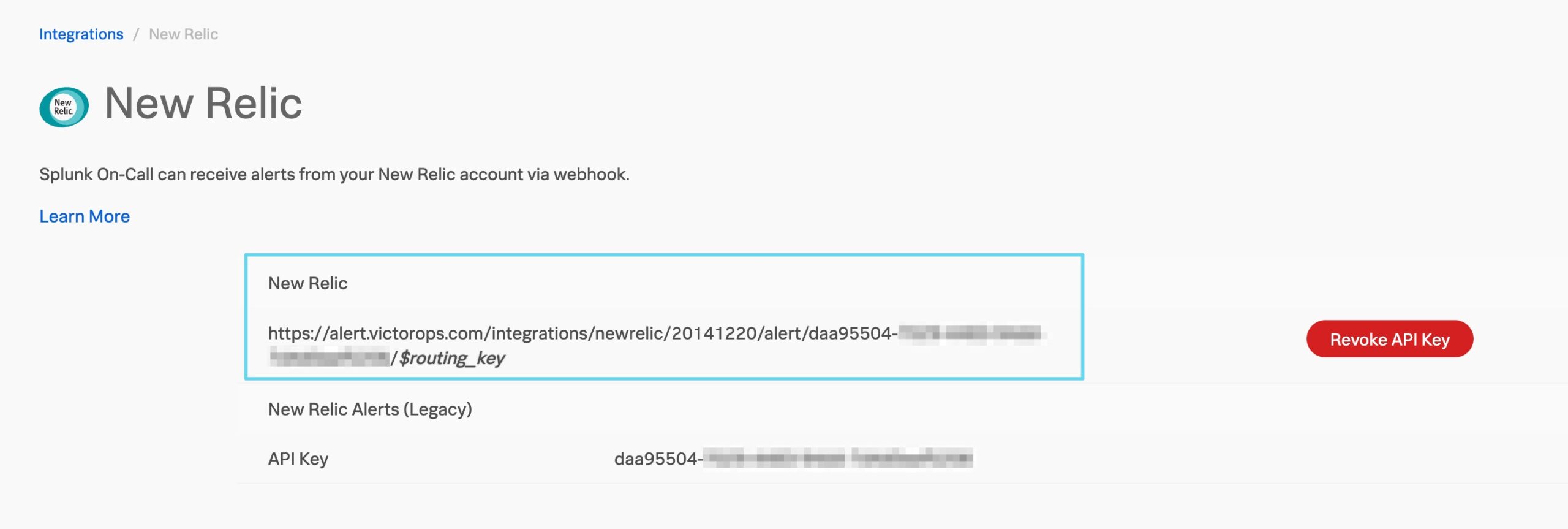
Splunk On-CallのNew Relicインテグレーション 🔗
Splunk On-CallのNew Relicインテグレーションを使用して、New Relic内でアラートクエリを定義し、Splunk On-Callを通して適切なエスカレーションチームに配信します。異なるルーティングキーを保持するさまざまなURLを使用することで、複数のオンコールチームとNew Relicチャネルを管理できます。
Splunk On-Call New Relicとのインテグレーションにより、チームは以下のことが可能になります:
New RelicとSplunk On-Callを統合し、アプリケーションのパフォーマンスとアラートを完全に把握します
リアルタイムで問題を解決するために、New RelicのモニタリングデータをもとにSplunk On-Callタイムラインで協力する
アラートとNew RelicインシデントをSplunk On-Callにルーティングし、オンコール・スケジュールで適切な担当者に通知する
Splunk On-Callで New Relicインテグレーションを有効化する 🔗
Splunk On-CallとNew Relicをリンクする 🔗
New Relic Alerts & AIを表示し、Workflows を選択します。
新しいワークフローを追加します。
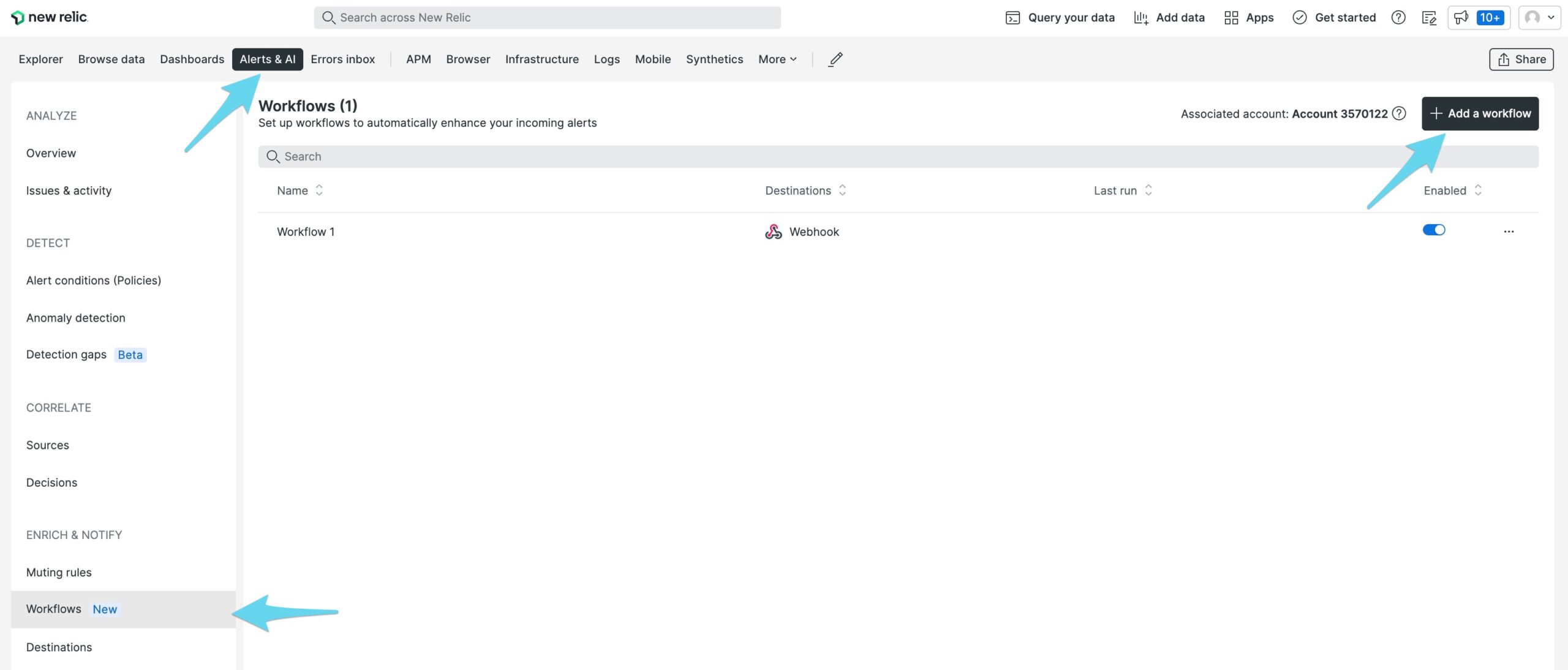
ワークフローの名前を入力し、フィルターリングとミュートセクションを定義します。
Webhook の下にある Notify を選択します。
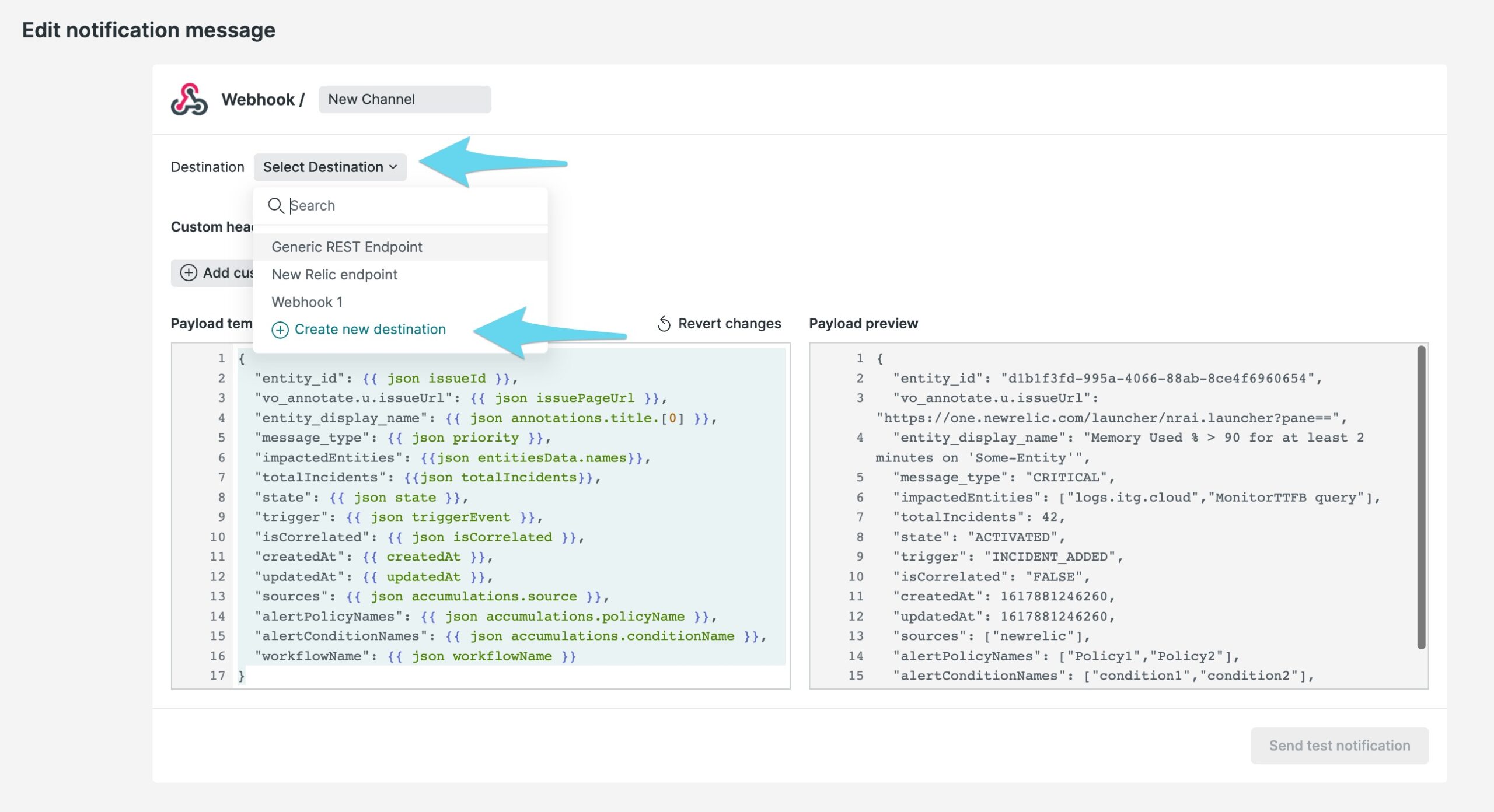
Select Destination を選択し、次に Create new destination を選択します。
先ほどコピーした New RelicのURLを Endpoint URL に貼り付けます。末尾の
$routing_keyは、アラートに使用する実際のルーティングキーに置き換えてください。ルーティングキーの詳細については、Splunk On-Callでルーティングキーを作成する を参照してください。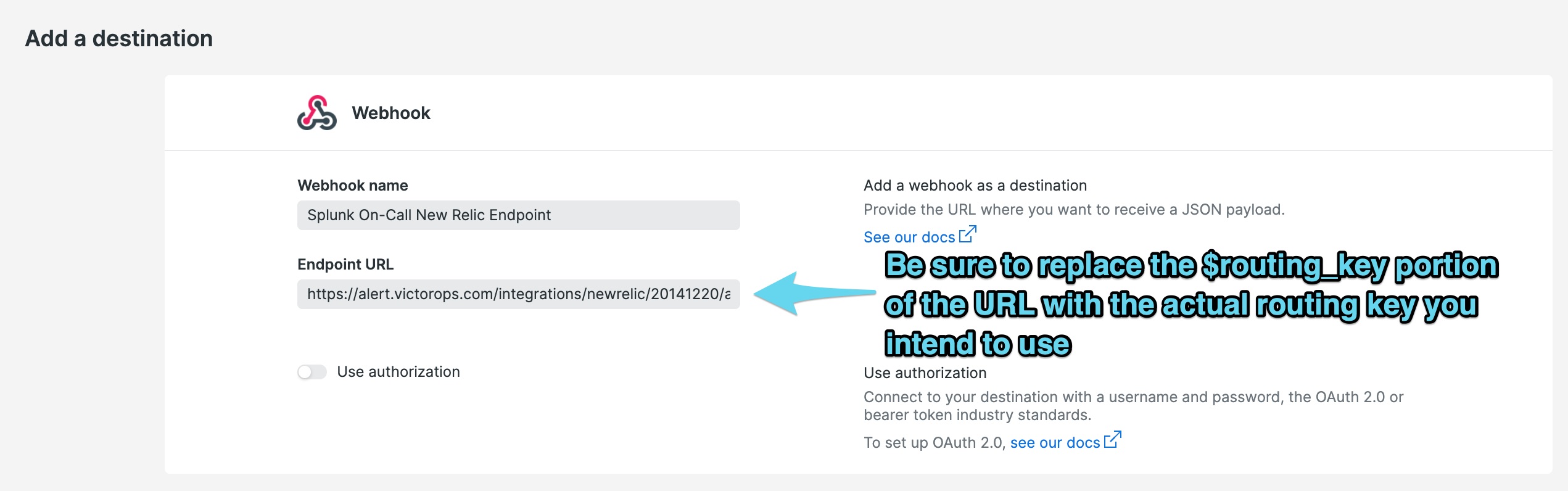
宛先を保存します。
Webhookに提供されたペイロードを更新します。以下のペイロードの例を参照し、カスタマイズしてください。
サンプルペイロード:
{ "impactedEntities": {{json entitiesData.names}}, "totalIncidents": {{json totalIncidents}}, "trigger": {{ json triggerEvent }}, "isCorrelated": {{ json isCorrelated }}, "createdAt": {{ createdAt }}, "updatedAt": {{ updatedAt }}, "sources": ["newrelic"], "alertPolicyNames":{{ json accumulations.policyName }}, "alertConditionNames": {{ json accumulations.conditionName }}, "workflowName": {{ json workflowName }}, "monitoring_tool":"New Relic", "incident_id":{{ json issueId }}, "condition_name" : {{ json accumulations.conditionName }}, "details" : {{ json annotations.title.[0] }}, "severity" : "CRITICAL", "current_state" : {{#if issueClosedAtUtc}} "CLOSED" {{else if issueAcknowledgedAt}} "ACKNOWLEDGED" {{else}} "OPEN"{{/if}}, "event_type": "INCIDENT" }
調整が完了したら Send test notification を選択し、Splunk On-Callアカウントに通知が届くようにします。
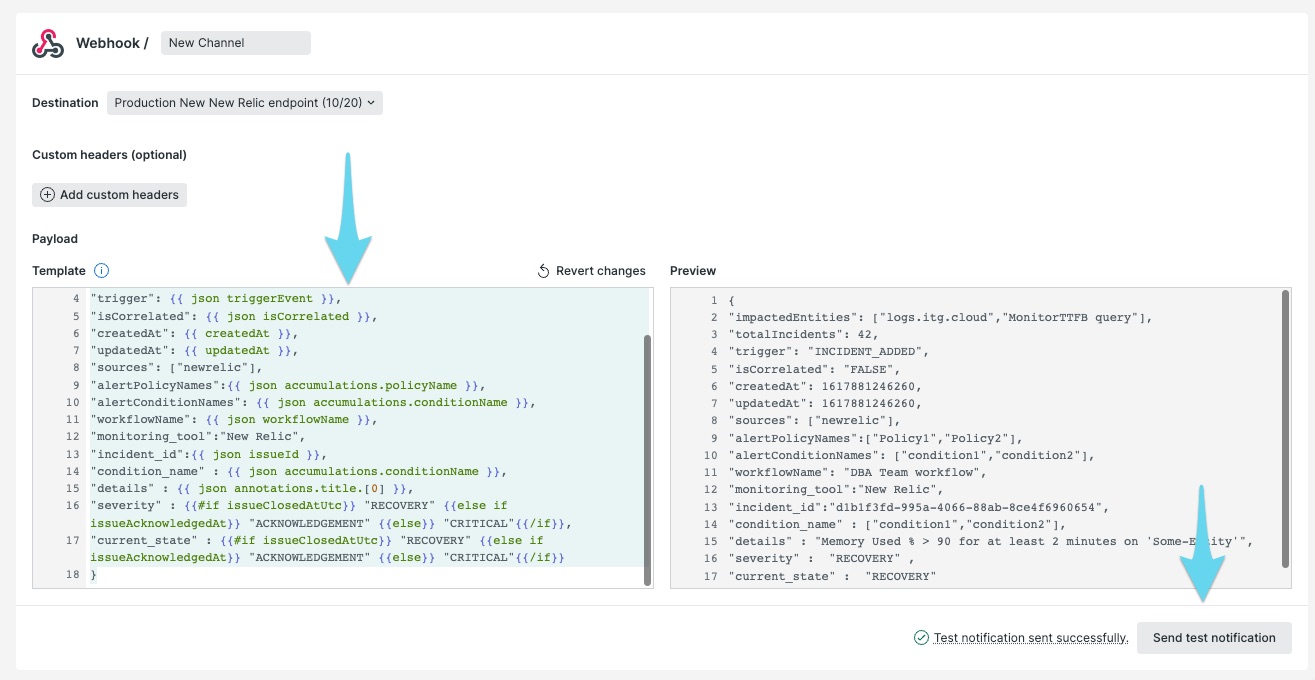
Update Message を選択し、次に Activate Workflow を選択して変更を保存します。
これで標準的なセットアップは完了です。必要に応じてこれを繰り返し、それぞれ異なるルーティングキーを持つ異なるWebhookチャネルに通知する新しいワークフローを構築します。これにより、Splunk On-Callの適切なグループにアラートをルーティングできるようになります。
レガシーバージョンのNew Relic 🔗
NewRelicのWebHookとしてVictorOpsを追加します。Tools を選択し、Alert policies
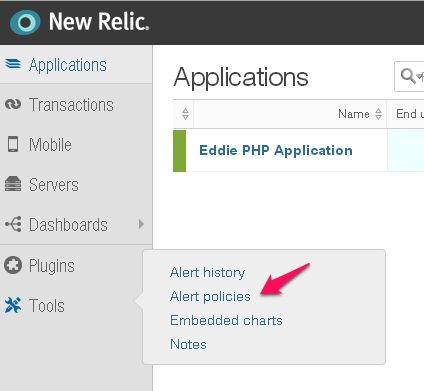 を選択します。
を選択します。Channels and Groups |newrelic10|を選択する
Create Channel を選択し、Webhook
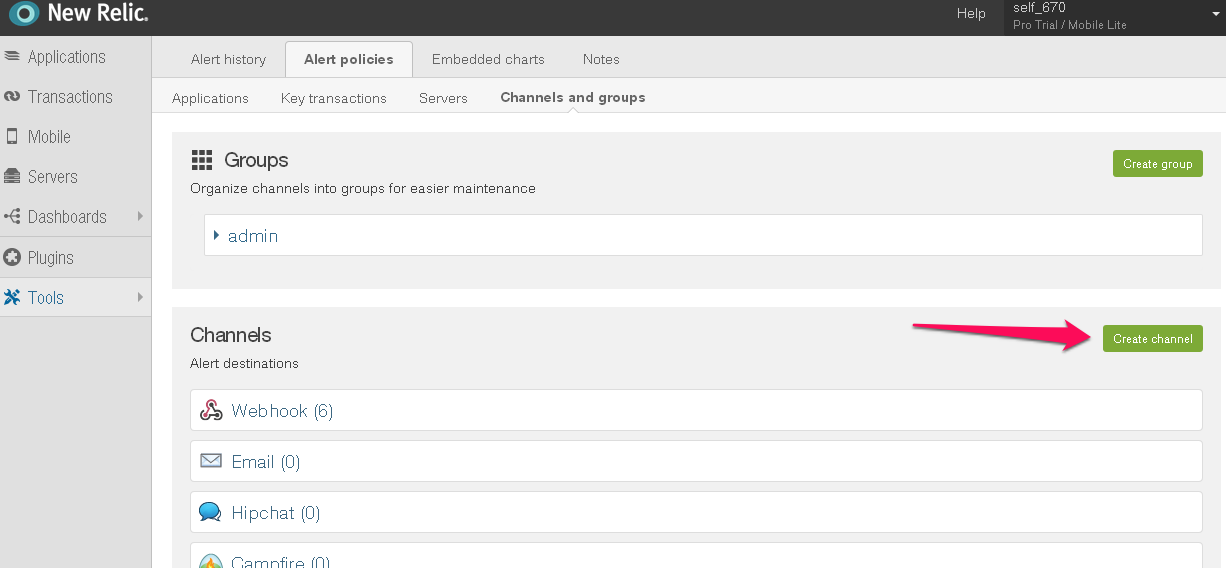
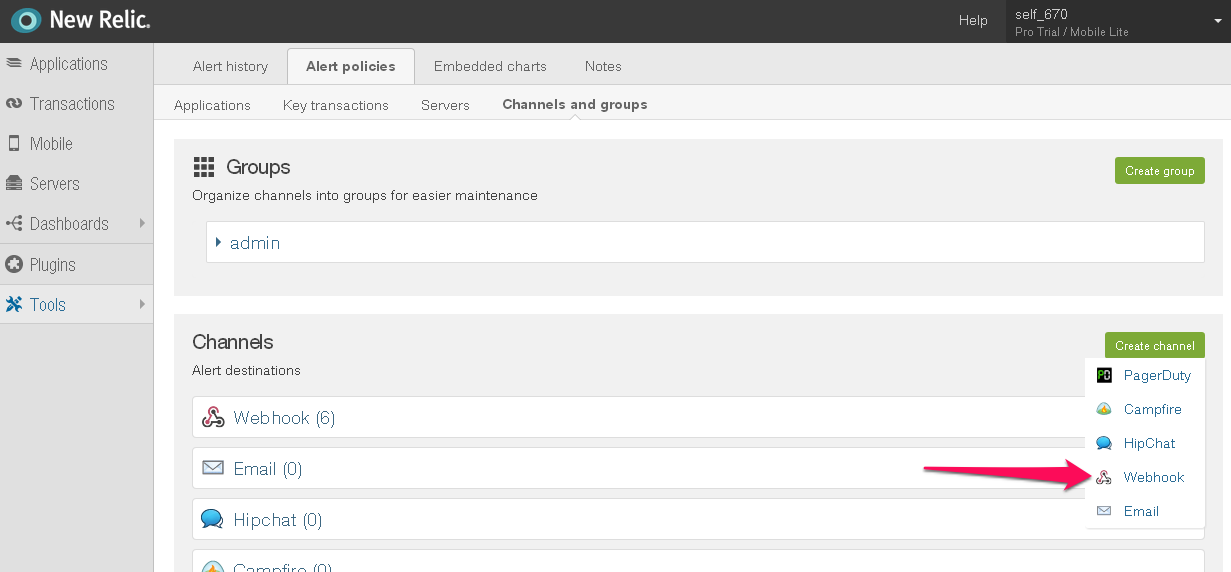 を選択します #. 任意の名前を入力してください。#. WebHookのURLに以下を入力します。正しいkeyとroute_key
を選択します #. 任意の名前を入力してください。#. WebHookのURLに以下を入力します。正しいkeyとroute_key https://alert.victorops.com/integrations/newrelic/20140115/alert/--key--/--routing--が含まれていることを確認してください #. Integrate with WebHooks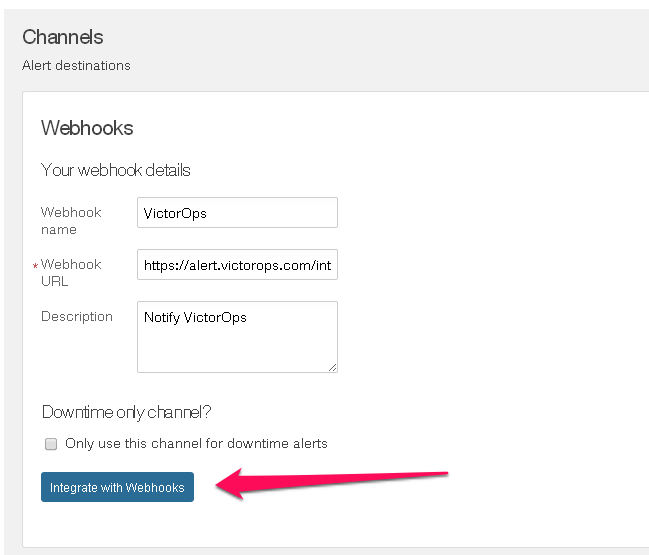 を選択します
を選択します