Splunk On-CallのGraylogインテグレーション 🔗
Graylogは、テラバイト単位のマシンデータをリアルタイムで収集、保存、分析するためのオープンスタンダードに準拠したオープンソースの集中ログ管理ソリューションです。
要件 🔗
このインテグレーションは以下のバージョンのSplunk On-Callと互換性があります:
Starter
Growth
エンタープライズ
このインテグレーションは、Graylogバージョン3.1以降と互換性があります。
Splunk On-Callの設定 🔗
Splunk On-Callで、Integrations、Graylog の順に移動します。
Enable Integration を選択し、後で使うために Service API Endpoint をコピーします。
Graylogの設定 🔗
Splunk On-Call通知を作成する 🔗
http://127.0.0.1:9000 でGraylogのWeb UIを開きます。そこからログインして Alerts Notifications に移動し、Create Notification を選択します。通知にタイトルと説明を付けます。
通知タイプに HTTP Notification を選択し、前のフィールドの Service API Endpoint を URL フィールドにコピーします。
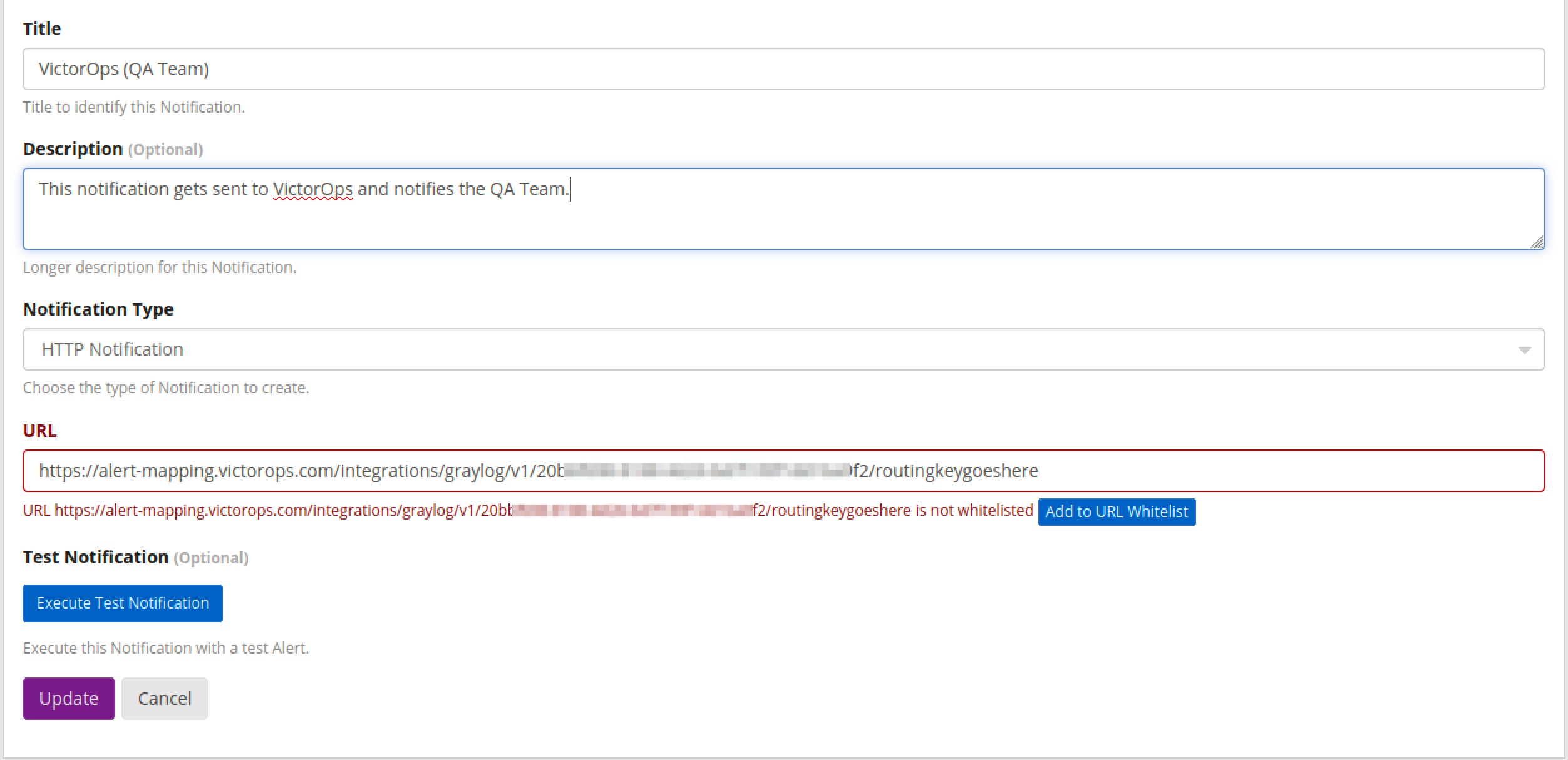
URLの末尾に適切なルーティングキーを付け、必要に応じてGraylogの許可されたURLに追加してください。
次に、Execute Test Notification を選択し、タイムライン上にテストアラートを作成します。

通知を保存するには、Create/Update を選択します。
注釈
Graylogに複数のルーティングキーを通知させたい場合は、ルーティングキーごとに新しい通知を設定する必要があります。
イベント定義にSplunk On-Call通知を追加する 🔗
Graylogの Alerts タブで、Event Definitions に移動し、新しいイベント定義を作成するか、既存のものを編集します。
イベント定義の Notifications タブに移動し、Add Notification を選択します。作成した通知を選択し、Done を選択します。
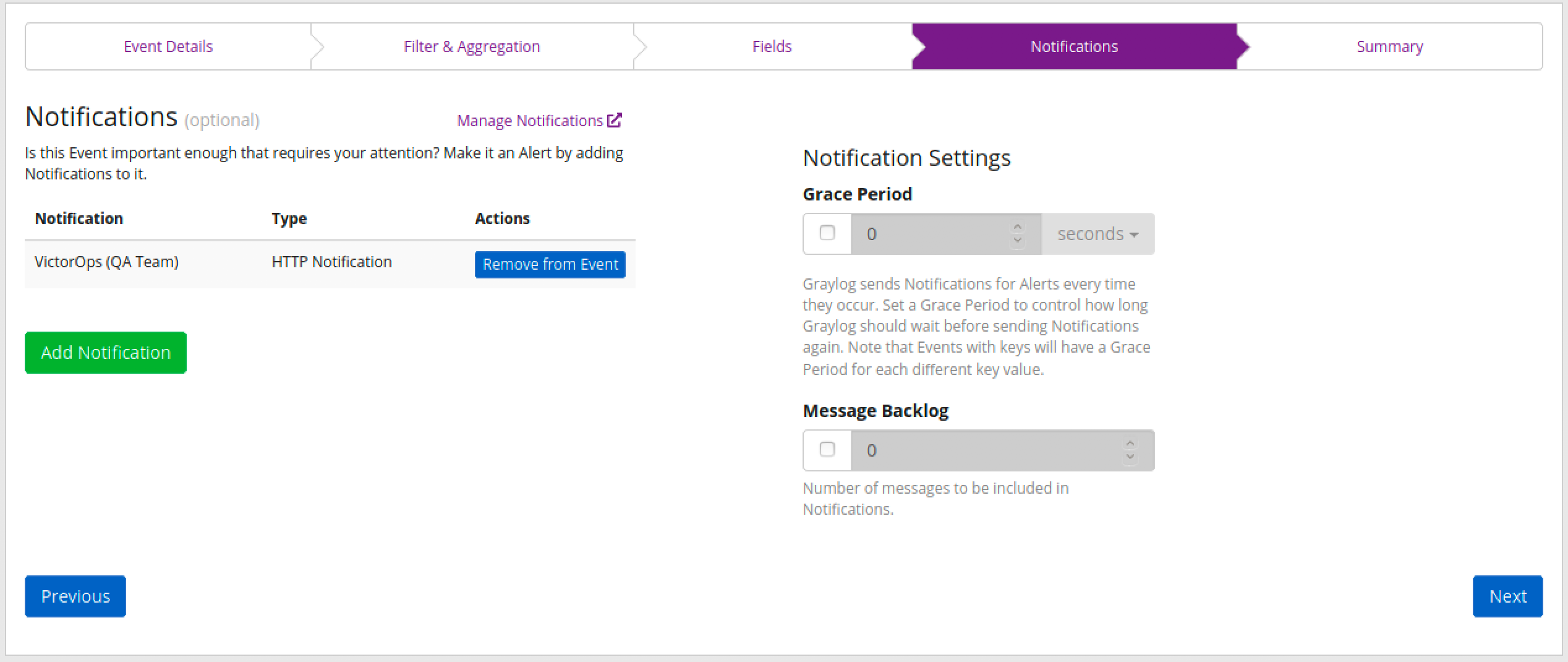
Splunk On-Callは、同じイベント定義IDを持つアラートを自動的に集約します。